
Hackers Beware
.pdfBy nature of how the Internet works, any machine that uses the Internet to communicate is inherently vulnerable to this type of attack. As we will cover in the next section, there are things that can be done to minimize the threat of a session hijacking attack, but there is no way to eliminate the threat. This can be frustrating because, with most other exploits, if you apply a patch, the problem goes away. With session hijacking, as long as users communicate over a network, the threat exists.
Little Can Be Done to Protect Against It
As we will cover in the next section, besides encryption, there is little that can be done to protect against session hijacking. This can be frustrating to many administrators, because they rely on countermeasures to protect against certain types of attacks. Based on this, people tend to forget that there is a threat and overlook session hijacking when performing forensic analysis after a breach. I know several companies that ignore the threat that session hijacking poses and discount that anyone would do that to them. But just because little can be done from a protection standpoint does not mean it is not a threat.
Hijacking Is Simple (with the Proper Software)
Session hijacking in theory is very complex. To perform it manually takes someone very skilled in network technology and computers—even then, it takes a considerable amount of time. However, based on the efforts of some very smart people, there are programs attackers use that make it much simpler to perform session hijacking. For those with even less skill, there are commercial programs available with easy-to-use interfaces that make it trivial for a large number of people to perform session hijacking. An attacker does not even need to understand how hijacking works. If he has a target in mind, a means to see the communication, and one of these tools, he can hijack a session like a professional.
Highjacking Is Very Dangerous
Session hijacking is dangerous for a large number of reasons. One of the main reasons is that it is operating system independent. It does not matter what operating system you are running, if you make a TCP/IP connection, an attacker can take over your session. Another reason is it can be used for both passive and active reasons. You can use it to capture sensitive information and passwords, without anyone ever knowing. From an active standpoint, it can be used to gain access and compromise a machine. Therefore, the potential harm is extremely high.
“Hackers Beware “ New Riders Publishing |
200 |
Most Countermeasures Do Not Work
As we will see in the next section, a lot of our traditional countermeasures are ineffective against session hijacking. You might have been told that if you have strong authentication or one-time passwords, your systems will be safe. Well, with some attacks that is true, but when it comes to session hijacking, these types of countermeasures are ineffective
Protecting Against Session Hijacking
As you have seen, session hijacking is an insidious threat because the attacker is taking over a legitimate session. In other types of attacks, you can remove what the threat exploits and therefore eliminate the threat. Unfortunately, in this case, to eliminate the cause would prohibit any legitimate connections, which defeats the purpose of having an Internet connection. Therefore, it is not an option. The following are some other options you can take to minimize the threat of session hijacking:
•Use encryption
•Use a secure protocol
•Limit incoming connections
•Minimize remote access
•Have strong authentication (least effective)
Use Encryption
Encryption is probably one of the few ways you can protect against session hijacking. If an attacker cannot read the data that is transmitted, it is much more difficult to hijack the session. One crucial aspect is to make sure that the local host is not compromised. If an attacker can compromise one of the end computers that is participating in the encryption, he can read the traffic before and after it is encrypted, because he has access to the machine that is performing the encryption. If an attacker has access to the machine, you have other issues.
At a minimum, all connections that are coming from the Internet must be encrypted. It is too easy to target Internet connections that anyone can see into your corporate network. Therefore, any critical connections where sensitive data can be transmitted must be encrypted. For example, if the finance employees need to access the remote accounts payable server, that connection must be encrypted.
Ideally, you want all traffic on your network to be encrypted. Most people want a solution that will solve most of their security needs—the silver bullet. Ironically, the technology that comes close to being a silver bullet has been around for a while, but no one wants to use it because they feel
“Hackers Beware “ New Riders Publishing |
201 |
it is too cumbersome. If companies religiously used encryption for all of their communications, we would have a lot less security issues.
Encryption schemes like Kerberos will help, depending on which encryption scheme is being used. Also, now that Windows 2000 has Kerberos support built in, more and more companies might start to use it. Also, Ipv6, which is the next generation of IP, also has encryption built into the protocol, which will help solve many of these issues.
Use a Secure Protocol
Whenever you are connecting to a remote machine, especially for sensitive work or administrative manners, use a secure protocol. You do not know how many times I see administrators telnet to the firewall or external router to administer it. When I see this happen, I look at them dumb founded. Here we have security professionals who are leaving themselves wide open to session hijacking and other types of attacks.
There are too many solutions available to leave yourself vulnerable. At a most basic level, there are protocols like ssh or secure telnet. At a more corporate level, there are VPN technologies that can go from client to server. When designing your security infrastructure, make sure you account for secure protocols when communicating with the various devices that make up your network.
Limit Incoming Connections
It’s the most basic principle they teach you in Firewall 101: Limit who can make incoming connections to your internal network. The less traffic that you allow to flow from the Internet into your corporate network, the more secure you will be. This also goes for minimizing the risk of session hijacking: The less possible ways an attacker can get into your network, the less ways he has to hijack a session. Ideally, you should block as much traffic as possible at both the external router and the firewall. Remember, the more protection you have, the better off you will be.
Minimize Remote Access
Minimizing remote access is the opposite of the last item we covered (limit incoming connections) but requires more attention. Most companies limit incoming traffic but allow internal users to connect to whatever machines they would like on whatever protocols. Some people argue that it is okay, because no sensitive information flows out of a company, which is a false statement. Also, in some companies, more sensitive information flows out of the company than into the company. Think of the possibilities for hijacking the business office as it connects to a bank each morning to manage its funds, or as an executive connects to his stockbroker to trade
“Hackers Beware “ New Riders Publishing |
202 |
stocks. Think of the potential financial damage (in the millions of dollars) this can cause if an attacker can hijack the session.
Strong Authentication—Not Effective
I’ve included this last item because a lot of people have the false assumption that strong authentication eliminates or minimizes the risk to session hijacking. Because session hijacking takes over a session after the user is authenticated, it really doesn’t matter how they authenticated. You can have the best authentication in the world, but if you only authenticate at the beginning of a session and an attacker takes over your session after you are successfully connected, authentication does not come into play. The only time authentication helps is if a user has to re-authenticate at random intervals throughout a session. Based on the inconvenience factor, very few sites do this
Summary
Session hijacking can cause a lot of damage, and it is fairly difficult to defend against. If you allow legitimate users to make connections to your systems, which you have to do, there is the chance that an attacker can hijack them. A large part of the vulnerability has to go back to how authentication works. Because authentication is only done at the beginning of a session, after a user is authenticated, an attacker can take over the session and become that user. For example, consider that an attacker gets physical access to your computer after you log on in the morning. After you authenticate, you are good for the remainder of the day, which makes it easy for that attacker to become you by sitting down at your terminal. In this example, you need physical access, but it emphasizes the risk to hijacking.
With session hijacking, the attacker can gain the same access without having any physical access; in fact, he could be on the other side of the world. This is why it is so important that a company addresses its security from as many angles as possible. Just because you have a firewall and strong authentication does not mean that an attacker cannot gain access by taking over a legitimate user’s session.
“Hackers Beware “ New Riders Publishing |
203 |

Chapter 6. Denial of Service Attacks
You come home from work after a long day at the office and the phone rings. You pick up the phone and no one is there. So you hang up, and immediately the phone rings again. After several times of doing this, you stop answering the phone, but the person keeps calling over and over again. The next morning when you go to work your boss says, “I tried calling you last night, but the phone was busy.” You actually weren’t on the phone, but an attacker was able to use up all your resources, so that legitimate calls did not come through. This is an example of a Denial of Service attack. In this case, the attacker kept your phone line tied up, so that your boss could not get through and legitimate users were denied access. As you can already see from this non-technical example, Denial of Service attacks can be very annoying and very difficult to protect against. In this simplified example, it would be difficult to protect against the attack. One solution to Denial of Service attacks is redundancy—you could put in a second line. However, that would not stop the attacker from launching an attack against both lines. As you will see throughout this chapter, Denial of Service attacks are extremely difficult to prevent, and from an attacker’s standpoint, they are very easy to launch.
To put Denial of Service attacks in perspective, let’s examine the three main areas of security: confidentiality, integrity, and availability. Denial of Service attacks are attacks against the third component, availability. Availability is preventing, detecting, or deterring the unauthorized denial of access to information and systems. Types of Denial of Service attacks range from crashing a user’s machine by sending them data they are not expecting, to overloading a machine by sending it too much information. No matter which type of attack is being performed, the end result of a Denial of Service attack is the same—a legitimate user cannot get access to the information he needs.
What Is a Denial of Service Attack?
A Denial of Service attack (DOS) is an attack through which a person can render a system unusable or significantly slow down the system for legitimate users by overloading the resources so no one else can access it. This can also result in someone damaging or destroying resources, so they cannot be used. Denial of Service attacks can either be deliberate or
“Hackers Beware “ New Riders Publishing |
204 |
accidental. It is caused deliberately when an unauthorized user actively overloads a resource. It is caused accidentally when an authorized user unintentionally does something that causes resources to become unavailable. An organization should take precautions to protect a system against both types of Denial of Service attacks.
Most operating systems (including NT and numerous variants of UNIX), routers, and network components that have to process packets at some level are vulnerable to DOS attacks. In general, DOS attacks are difficult to prevent. However, restricting access to critical accounts, resources, and files and protecting them from unauthorized users can hinder many DOS attacks.
It seems that the number of Denial of Service attacks are increasing every day. If an attacker is unable to gain access to a machine, most attackers will just crash the machine to accomplish a Denial of Service attack. This means that even though your systems may be patched and properly secured, an attacker can still do damage to your company.
Types of Denial of Service Attacks
There are two general types of Denial of Service attacks. The first type involves crashing a system or network. If an attacker can send a victim data or packets it is not expecting, and it causes the system to either crash or reboot, then in essence, the attacker has performed a Denial of Service attack because no one will be able to get to the resources. From an attacker’s standpoint, what is nice about these attacks is that you can render a system inaccessible with a couple of packets. In most cases, for the system to get back online would require intervention from an administrator to reboot or power off the system. So, this first type of attack is the most damaging because it requires little to perform and human interaction to fix.
The second type of attack involves flooding the system or network with so much information that it cannot respond. For example, if the system can only handle 10 packets a minute, and an attacker sends it 20 packets a minute, then when legitimate users try to connect to the system, they are denied access because all the resources have been exhausted. With this attack, an attacker has to constantly flood the system with packets. After the attacker stops flooding the system with packets, the attack is over and the machine resumes operation. This type of attack requires a lot more energy on the part of the attacker because he has to keep actively flooding the system. In some cases, this type of attack could crash the machine, however in most cases, recovering from this attack requires minimal human intervention.
“Hackers Beware “ New Riders Publishing |
205 |
It is important to note that both of these attacks can be launched from a local system or over a network.
What Is a Distributed Denial of Service Attack?
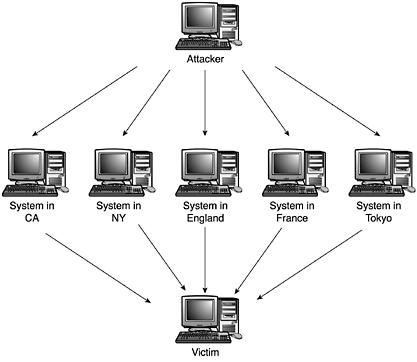
With a traditional Denial of Service attack, a single machine is usually launching the attack against a victim’s box. However, in the year 2000, a new type of attack was introduced—a distributed Denial of Service attack or DDOS. In this case, an attacker breaks into several machines, or coordinates with several friends, to launch an attack against a target machine or network at the same time. So, now it is not just one machine launching the attack, but several. This makes it difficult to defend against the attacks because the machine is not just receiving a lot of packets from one machine, but from any number of machines all at the same time. Also, because these attacks are coming from a wide range of IP addresses, it is much more difficult to block and detect because a small number of packets from each machine might slip under the Intrusion Detection Systems (IDS) radar. If a single IP address is attacking a company, it can block that address at its firewall. If it is 100 machines, this is extremely difficult. Further in this chapter, in the section, “Tools for Running DOS Attacks” we examine several tools that make it easy to launch DDOS attacks.
Figure 6.1 is an example of what a DDOS attack looks like.
Figure 6.1. Diagram of a distributed Denial of Service attack (DDOS).
“Hackers Beware “ New Riders Publishing |
206 |
As you can see, multiple systems from all around the world are launching an attack against a single victim. If DOS attacks are difficult to prevent when they are coming from a single source, think of how much harder it is to protect against DDOS attacks that are coming from multiple machines at multiple locations.
Why Are They Difficult to Protect Against?
DOS attacks are difficult to protect against because you can never totally eliminate the threat. If you are connected to the Internet, there is always the chance that an attacker may send you too much data that you are not able to process. Therefore, you can minimize your threat my increasing your bandwidth, however an attacker can always use additional resources to flood your network.
Let’s look at another example. You come home from work and you live on a cul-de-sac, which means there is only a single road to get to your house, and there is currently a truck blocking that road. Very easily, someone has just launched a Denial of Service attack, denying you access to your house. One way to protect against this attack is to build a second road, so you have an alternate route to your house. First, this is very expensive, and second, it does not completely eliminate the threat. Now, someone could just get two trucks and block both roads. You could then build a third road, but they could still block that route. The bottom line is that there are things that can be done to minimize the threat, but if an attacker has enough time and resources, he can still be successful.
Now that we understand what Denial of Service attacks are and why they are such an insidious threat, let’s look at several known DOS exploits.
“Hackers Beware “ New Riders Publishing |
207 |

Description of Exploits
At this point in the book, we are starting to address different exploits in detail. In going over how exploits work, and what can be done to prevent exploits from damaging your systems, I have created a general format that is used throughout the remainder of the book. The following is an outline of the format and a brief description of each item.
Exploit Details
•Name: Name of exploit
•Variants: Name of different variants of the exploit
•Operating System: OSs impacted
•Protocols/Services: Protocols or services the exploit uses
Protocol Description
This section gives a brief description of the protocol the exploit uses. In most cases, to understand the exploit, you need to understand the protocol‘s strengths and weaknesses.
Detailed Description
After the foundation information is described, a detailed description of the exploit is covered.
How the Exploit Works
This section describes how the exploit works and why it is able to exploit the feature in the protocol or application program.
Diagram
This section provides a typical diagram of how the exploit would work on a network.
How to Use It
This section shows the programs used to exploit the vulnerability and how to use them.
Signature of the Attack
This section shows you what to look for if you are trying to detect
“Hackers Beware “ New Riders Publishing |
208 |

or block the attack.
How to Protect Against It
This provides a description of what can be done to patch the protocol or how a company can protect itself.
Source Code/Pseudo Code
This section provides links to where the source code can be found and a brief listing and description of the pseudo code. Source code is the actual code that someone compiles to run the exploit.
Because source code is sometimes hard to read, pseudo code is a description of what the code does and is easier to follow.
Additional Information
This section provides resources for additional information.
Types of Denial of Service Attacks
At this point, we understand what a DOS attack is and why they are so difficult to protect against. Now let’s look at several types of DOS attacks to get a better idea of how they work. The following are the exploits we explore in this chapter:
•Ping of Death
•SSPing
•Land
•Smurf
•SYN Flood
•CPU Hog
•Win Nuke
•RPC Locator
•Jolt2
•Bubonic
•Microsoft Incomplete TCP/IP Packet Vulnerability
•HP Openview Node Manager SNMP DOS Vulnerability
•Netscreen Firewall DOS Vulnerability
•Checkpoint Firewall DOS Vulnerability
Some of these attacks have been around for a while, however, they are included because they cover very important concepts of how DOS attacks work, and they give you an idea of the range of services or protocols that can be attacked, to cause a Denial of Service attack. For example, the exploit Ping of Death is covered because it is one of the “classic” DOS attacks, and it shows how simple an attack can be. Others, such as smurf,
“Hackers Beware “ New Riders Publishing |
209 |
