
English for Electrical Engineers
..pdfText 12. CELL PLANNING
When planning a location/service area for a wireless network, three main approaches exist: equilateral triangles, mesh (square or rectangle), and hexagonal coverage. Although propagation considerations recommend the circle as a cell shape, the circle is impractical for design purposes. An array of circular cells produces ambiguous areas, which are contained either in no cell or in multiple cells. On the other hand, any regular polygon approximates the shape of a circle and three types, the equilateral triangle, the square and the regular hexagon, can cover a plane with no gaps or overlaps. A service area could be designed with square or equilateral triangles, but for economic reasons the regular hexagonal shape has been adopted. The economical motivation for choosing the hexagon is as follows: Assume a base station located at the center of each cell, the center being the unique point equidistant from the vertices. The vertices are in fact the worst case points since they lie at the greatest distance from the nearest base station. Restricting the distance between the cell center and any vertex to a certain maximum value helps to assure satisfactory transmission quality at the worst case points. If an equilateral triangle, a square, and a regular hexagon all have the same center-to- vertex distance, the hexagon has a substantially larger area. Consequently, to serve a given total coverage area, a hexagonal layout requires fewer cells, therefore fewer transmitter sites. It is worth noting that in real wireless networks, the shape and size of the cell does vary, but for analytical modeling only homogeneous cells sizes are considered. Furthermore, in real wireless networks rectangular and sectorized cell layout is common in urban environments. However, in the scope of this chapter only hexagonal shaped homogeneous cells are considered.
As you read
AName the titles of the main cell planning approaches.
BDescribe the economical motivation for choosing the hexagon approach.
Before you read text 13
How do you think the text will tell us about?
What Russian version of the title can you suggest?
Text 13. COMPLEX OBJECTS NEED COMPLEX SECURITY
The safety of people, property and business is unavoidable subject of interest of every businessman. To constantly keep it on the higher level from the various risks which are spoiling it and in order to take economically correct measures there are used various technical security systems. For coordinate and successful protection of bigger retail, business, hotel and industrial objects or the complexes of objects the integrity application is extremely important because we are talking about objects with large surfaces, where there is a bigger exposure for people, property, and security with several systems of technical security. They usually have a surveillance center, which can be in mount of e.g. hotel reception where there can be somebody who pursues the job of operator 24 hours a day all year around.
The series of the integrated precaution increase the security level because the weaknesses of some measures don’t mach.
Unstoppable development of technology has provided high reliability of devices which are used in technical security, it has increased their accessibility and lower their price and by that made them obligatory factor of security especially if we a talking about complexes facilities. At the same time the number and the complexity of the systems which are used for
51
protection of an object grows in expanse (more systems and a higher number of elements such as detectors, cameras and printers) and in depth (more complex devices which are becoming harder to use because of the increasing of functions).
According to 2008, integrated systems of technical security have 10% stake on market. That fact has a special meaning because a few years ago the stake of integrated systems was inconsiderable and was not mentioned in annual report. It is expected that the stock of integration will proceed to grow especially on the complexes facilities. In that contribution goes the facts from the series of research done in the last few years among the technical protection users. According to the research from J.P. Freeman Co. integrated systems are third, after uniformed guard and digital video-surveillance, factor of the decreasing risk in banks.
According 2005 European Retail Teath Barometer, integrated technical security systems are third factor which decreases lost in retail sector, after investment in basic system of technical security and focused strategies for preventing robbery.
In accordance of the Security Sales & Integration research from 2009, 58% of terminal users of technical security are exceptionally interested for integration of the system and 29% of them even presume that the difficulties upon integrations are a big objection to the technical protection.
Trend is to connect all other technical systems in facility in order to be able to monitor and manage them easily. These systems can be air conditioning, ventilation, lighting, elevators, etc. and they can connect with technical security systems to ensure a monitoring and control from a single integrated interface. Thus, in addition to increasing the security of the facility (blocking the use of elevators in case of fire alarms), and increases the ability to manage all technical building systems, including energy saving. This system allows the operator to control air-conditioning and lighting, and to turn it off when are no more people in the area. Surveillance can verify the events obtained from other technical systems typically associated with building management.
In bigger and more complexes objects, equipped with several large technical security systems, it becomes hard and complicated to control and monitor them without using computer and unique interface because it is necessary to monitor every system on a separated computer. Working mutually with unconnected systems means that operators in surveillance center need to know how to control multiple different object systems which enables the actualization of the main task – qualified choosing based on the information which they get from the system and the right application of the adequate procedures. That’s why is necessary to hold the growing complexity of the technical security system in the frames of usable, especially from the operator’s view which necessary means integrating various systems and transporting a part of intelligence from the operator to the system.
After you read
What is it said about 2009, 2008 and 2005?
Why is the integrity application extremely important?
What is the trend according to the text?
The process of scientific discovery is, in effect, a continual flight from wonder.
—Albert Einstein, Autobiographical Notes
52
Before you read text 14
What effort should be taken to be sure that the system is kept secure?
How do you understand the quotation above?
Text 14. 10 WAYS TO KEEP IT SYSTEMS SECURE
Use these tips to protect your business from hackers, crooks and identity thieves.
Technology continues to be a boon for entrepreneurs, offering increased mobility, productivity and ROI at shrinking expense. But as useful as modern innovations such as smartphones, tablet PCs and cloud computing are to small businesses, they also present growing security concerns. Following are 10 safety tips to help you guard against high-tech failure:
1.Protect with passwords. This may seem like a no-brainer, but many cyber attacks succeed precisely because of weak password protocols. Access to all equipment, wireless networks and sensitive data should be guarded with unique user names and passwords keyed to specific individuals. The strongest passwords contain numbers, letters and symbols, and aren’t based on commonplace words, standard dictionary terms or easy-to-guess dates such as birthdays. Each user should further have a unique password wherever it appears on a device or network. If you create a master document containing all user passcodes, be sure to encrypt it with its own passcode and store it in a secure place.
2.Design safe systems. Reduce exposure to hackers and thieves by limiting access to your technology infrastructure. Minimize points of failure by eliminating unnecessary access to hardware and software, and restricting individual users’ and systems’ privileges only to needed equipment and programs. Whenever possible, minimize the scope of potential damage to your networks by using a unique set of email addresses, logins, servers and domain names for each user, work group or department as well.
3.Conduct screening and background checks. While rogue hackers get most of the press, the majority of unauthorized intrusions occur from inside network firewalls. Screen all prospective employees from the mailroom to the executive suite. Beyond simply calling references, be certain to research their credibility as well. An initial trial period, during which access to sensitive data is either prohibited or limited, is also recommended. And it wouldn’t hurt to monitor new employees for suspicious network activity.
4.Provide basic training. Countless security breaches occur as a result of human error or carelessness. You can help build a corporate culture that emphasizes computer security through training programs that warn of the risks of sloppy password practices and the careless use of networks, programs and devices. All security measures, from basic documentdisposal procedures to protocols for handling lost passwords, should be second-nature to members of your organization.
5.Avoid unknown email attachments. Never, ever click on unsolicited email attachments, which can contain viruses, Trojan programs or computer worms. Before opening them, always contact the sender to confirm message contents. If you’re unfamiliar with the source, it’s always best to err on the side of caution by deleting the message, then potentially blocking the sender’s account and warning others to do the same.
6.Hang up and call back. So-called "social engineers," or cons with a gift for gab, often prey on unsuspecting victims by pretending to be someone they’re not. If a purported representative from the bank or strategic partner seeking sensitive data calls, always end the call and hang up. Then dial your direct contact at that organization, or one of its public numbers to confirm the call was legitimate. Never try to verify suspicious calls with a number provided by the caller.
7.Think before clicking. Phishing scams operate by sending innocent-looking emails from apparently trusted sources asking for usernames, passwords or personal information.
53
Some scam artists even create fake Web sites that encourage potential victims from inputting the data themselves. Always go directly to a company’s known Internet address or pick up the phone before providing such info or clicking on suspicious links.
8.Use a virus scanner, and keep all software up-to-date. Whether working at home or on an office network, it pays to install basic virus scanning capability on your PC. Many network providers now offer such applications for free. Keeping software of all types up to date is also imperative, including scheduling regular downloads of security updates, which help guard against new viruses and variations of old threats.
9.Keep sensitive data out of the cloud. Cloud computing offers businesses many benefits and cost savings. But such services also could pose additional threats as data are housed on remote servers operated by third parties who may have their own security issues. With many cloud-based services still in their infancy, it’s prudent to keep your most confidential data on your own networks.
10.Stay paranoid. Shred everything, including documents with corporate names, addresses and other information, including the logos of vendors and banks you deal with. Never leave sensitive reports out on your desk or otherwise accessible for any sustained period of time, let alone overnight. Change passwords regularly and often, especially if you’ve shared them with an associate. It may seem obsessive, but a healthy dose of paranoia could prevent a major data breach.
The average cost to an organization to recover from such a breach is $6.75 million, according to Javelin Strategy & Research. And that doesn’t count damage to your reputation or relationships. So be proactive and diligent about prevention. An ounce far outweighs a pound of cure.
After you read
Make a list of the tips and try to describe them using only one sentence for each.
As you read
What, in your opinion, are the most dangerous consequences of these problems?
Text 5 mentions 10 tips. What is the most secure one in your opinion?
Before you read text 15
What danger can appear if we speak about computing and industrial control systems?
How can we solve the problem concerning the cyber-attack?
Text 15. TRUSTED COMPUTING FOR INDUSTRIAL
CONTROL SYSTEMS AND INFRASTRUCTURE
Beyond the stuxnet worn that targeted industrial software and equipment, supervisory control and data acquisition (SCADA) attacks are becoming increasingly common.
In an article for the Wall Street Journal on taking the cyber-attack threat seriously, Barack Obama noted: “Last year, a water plant in Texas disconnected its control system from the internet after a hacker posted pictures of the facility's internal controls.
"More recently, hackers penetrated the networks of companies that operate our natural gas pipelines. Computer systems in critical sectors of our economy – including the nuclear and chemical industries – are being increasingly targeted".
In October, US Secretary of Defense Leon Panetta warned about the growing threat of attacks against the country’s critical infrastructure.
"We know of specific instances where intruders have successfully gained access to these control systems," Panetta said.
54
"We also know they are seeking to create advanced tools to attack those systems and cause panic, destruction and even loss of life."
Industrial control systems (ICS) play a critical role in any nation’s infrastructure. Specific ICS areas include:
Resource extraction and transportation;
Power generation, distribution and delivery;
Healthcare equipment and data exchange;
Process control;
Transportation;
Building automation;
Manufacturing.
Communications in all these areas suffer from proprietary protocols in legacy and current hardware. In addition, security in these systems has historically not been a major consideration.
In the US, the Department of Homeland Security’s Industrial Control Systems Cyber Emergency Response Team (ICS-CERT) is concerned with the disruption that can be caused by attacks on ICS and other enterprise equipment.
ICS-CERT has advised that the Shamoon virus, first detected by Symantec in August, could harm control systems even though it does not specifically target them. Vulnerabilities in ICS products are being disclosed at alarming rates, and new mysterious vulnerability markets present new dynamics for assessing risk and crafting strategy. In general, ICS attack targets can include power plants, chemical plants, water delivery systems, and many other facilities with control networks.
Companies and IT managers who want to avoid finding out how extensive the damage and disruption might be to their systems have a solution available that has been developed over several years as part of overall enterprise computer and network security protection. Developed by technical expert members who represent the leading companies that supply computing and network technology – as well as high-tech users including The Boeing Company, BAE Systems, and many others – the Trusted Computing Group’s (TCG’s) open standards now include specifications that address the connectivity management and network security of ICS environments.
These new specifications build on other TCG open standards for protecting enterprise information in hard drives, through TCG’s Trusted Storage, or the network, through TCG’s Trusted Network Connect (TNC) including entry points such as machine-to- machine (M2M) interfaces. The increased security provided by these systems can additionally be anchored in the Trusted Platform Module (TPM) hardware, an integrated circuit, hardwarebased root of trust that delivers substantial endpoint protection.
The existing networks in enterprises, including the internal intranet and virtual LANs (VLANs), external connectivity to internet, cellular and WiMAX, present provisioning, operational management, health monitoring, system reliability, security and other scaling challenges. These challenges are exacerbated by ICS environments, where traditional IT management tools do not apply well. TCG’s Interface for Metadata Access Points (IF-MAP) provides a solution for publishing, searching and subscribing to metadata, the data about data. The open standard protocol was designed for security coordination use cases. It provides a highly scalable architecture optimised for loosely structured metadata.
Adding to the protection that IF-MAP enables, TCG recently announced a new standard that extends TNC IF-MAP for greater network security. IF-MAP Metadata for ICS Security specification addresses the deployment, management, and protection of large-scale industrial control systems by creating secure virtual overlay networks on top of the standard, shared IP network infrastructure typically used in ICS.
IF-MAP metadata and extended identifiers are defined in the specification along with a prescribed set of MAP client behaviours. Together, they provide the necessary coordination
55
and configuration management functionality for creating secure logical overlay networks for communication between and with ICS devices.
There are distributed ICSs that are isolated from the corporate network through a variety of traditional mechanisms, each with varying tradeoffs between cost, management, security, and performance. Since many of the ICS environments represent the revenuegenerating components of an enterprise, there are significant business drivers to add connectivity between corporate network services and these systems.
Adding increased connectivity into what has traditionally been isolated with an air gap presents significant people, process, and technical challenges. Naturally, the goal is to make an investment in an architecture that has a clear ROI, and to determining the level of defensive layers appropriate to the surety and risk required for a given enterprise. The TCG ICS Security specification bridges gaps between IT management tools and the operational requirements of ICSs, while simplifying the application of additional defensive layers of security.
Building on the soon-to-be-published ISA 100.15 architectural model for secure ICS communications over untrusted shared networks (TR100.15.1, “Wireless Backhaul”), the ICS domain-specific network architecture defined in the new specification:
Operates with legacy (existing) ICS devices and infrastructure
Enables isolation between ICS security domains and/or individual ICS components
Enables the use of cryptographically bound identities for ICS devices and Policy Enforcement Points (PEPs)
Enables the use of overlay networks for isolating and protecting key components
Enables the creation of extended metadata for defensive layers such as firewall and deep packet inspection (DPI)
Provides operational access control
Enables self-provisioning ICS Devices
With enough effort, any physical or cyber security system can ultimately be breached, yet businesses interested in strengthening their defenses against attackers need to explore the protection that can be added to their network infrastructure, including the ICS elements. The Trusted Computing Group with its established history of providing improved trust to enterprise computers, networks, and more, has the standards-based tools to implement this higher level of security. For ICS and SCADA equipment, the new ICS Security Metadata specification provides the means to add a layer of management and security into new and existing ICS environments. The alternative of doing nothing could provide first-hand experience to the destruction and disruption that increasingly dangerous malicious software can cause.
After you read
Answer these questions:
1.What do these abbreviations stand for: SCADA, ICS-CERT, TNC, TPM, IF-MAP?
2.How many Specific areas does ICS include?
3.Which viruses were mentioned? How do they work?
4.How does TCG protect the networks, systems?
Before you read text 16
What is the infrastructure network? How do you understand it?
56
Text 16. INFORMATION SYSTEM
FOR INFRASTRUCTURE NETWORKS
J. Berchtold, IIS Institute for Independent Studies Zürich
We investigate and develop a plug-in framework to amalgamate data form data acquisition and measurements, monitoring and modeling and to treat them into usable formats for the various interpreting, visualisation, control and monitoring software. This decisionmaking informational support system is ported and implemented onto the MDAC platform. Simulation and optimization of power systems and assurance of operational reliability of power complexes is researched. It includes assurance of tolerance of power supply systems on the basis of data-analytical decision-making environments.
Information originates and is best captured on-site. Its exponentially growing amount cast into electronic data needs to be processed and analysed immediately in order to avoid critical data transfers (bandwidth, security, ownership). While “soft”- ware (data gathering and data transfer) is universal and has developed in a sophisticated manner and to a great extent, “hard”-ware (information processing infrastructure) seems to be trapped in static and rigid facilities (conventional data centres) or to limited compute capacity (smart phones, portable computers, cloud services). Modern compute technology is still not ready to conquer the remote spot. In order to allow “hard”-ware to grow and develop at the pace of “soft”- ware, one has to free it from static facilities and embed it into a versatile structure that copes with environmental challenges of any kind. Only processed information creates added value.
The Project Modular Data Acquisition Centre (MDAC) was initiated to cope with modern information processing challenges. The concept is a scientific platform for on-site information processing consisting of a scientist's network and the MDAC bringing compute capacity to the field. The proposed information system for infrastructure networks and urbanistics is researched and implemented onto the MDAC platform. The objective is to build a pluggable 4D modeling framework which easies software for modeling and visualization. It can be extended and customized through an open plug-in architecture.
A decision-making informational support system for power systems and power complexes is applied. Management of life cycle of electric equipment networks is implemented on the basis of modern methods of CALS-technologies. We investigate how iterative feedback cycles of sensing and analyzing system data will enhance operational processes and the stability of the system. The state-of-the-art in data processing appears to be the spatial and temporal separation between data acquisition and analysis. Nowadays compute infrastructure like conventional data centres, cloud services and modular data centres fail to unite this processes. Portable devices may to some extent be used for on-site data processing but they only provide limited compute capacity. The lack of such systems is the poor protection from environmental hazards, thus they carry incalculable risks when exposed on-site.
The proposed information system plans, monitors, coordinates and analyses operational processes. The plug-in framework carries modular structure in order to incorporate additional features at a later stage.
As you read
Using the web browser find out the information about the IIS and make up a presentation about it.
Would suggest some new ideas to the MDAC project?
After you read
1.Make a list of the words which can describe the MDAC platform.
2.What is the main objective of the MDAC platform?
3.What information can be titled as the impact and result of the project?
57
Before you read text 17
Can we connect these words with each other if we speak about technology and the progress?
Text 17. AUTOMATION, ROBOTICS, AND CONTROL
The Automation, Robotics, and Process Control group is concerned with the development of technologies for controlling the dynamics of complex systems for a variety of applications.
State-of-the-art automation solutions are developed for a wide range of industries, ranging from sub-micron, high precision machinery for optoelectronics and semiconductor manufacture, to high-speed assembly of consumer goods. Our data-driven systems facilitate flexibility, self diagnostics and minimal change over time. A representative project in this area is the development of an automated fiber-optic coil winder for fiber-optic gyroscope production. This computer-controlled machine reduces cycle time by an order of magnitude, actively controls winding tension, winds several patterns with zero change-over time and includes a vision-based error detection and correction system for increased quality and reliability.
Improving materials processing capabilities is of fundamental importance to meeting the manufacturing requirements for the next generation of materials. However, processing problems are increasingly more difficult as we seek to manufacture new materials, achieve greater control over material microstructure, and meet stringent performance requirements.
We focus on developing and applying a controls-based approach to enhancing materials processing capabilities which includes an integrated effort of physical modeling, sensor development, system design and control development. Design of both the system and control structure needs to be conducted with an understanding of the dominant process physics. Research projects, typically conducted with industry partners, span a range of important applications areas including enhanced materials processing for opto-electronic applications, advanced engines, power systems and cutting tools.
Specific applications now under development include integration of mechanical and control system design for industrial robot manipulators, adaptive tuning of adjustable vibration absorbers for aircraft and space structures, active and/or passive methodologies for introducing motion confinement characteristics in repetitive structures, distributed impact damping as a means of attenuating vibrations of machinery and structures, friction modeling and compensation applied to precision machining, disk head positioning, teleoperation, and robotic manipulation, as well as biologically-inspired control of walking robots.
A natural extension of computer-based control is the introduction of modern wired and wireless networking technologies to integrate spatially distributed sensors, actuators, and other devices to close control loops. We focus on the use of wireless networking technologies (IEEE 802.11b, Bluetooth, etc.) for both hard real-time (teleoperated robot control, robotic surgery, etc.) and soft real-time (supervisory control of mobile robots) applications. Also, it is aimed at understanding the fundamental information processing (datarate) requirements for controlling complex physical systems. Data compression techniques which optimize closed-loop control performance are being developed for communication links between sensors and actuators that are subject to network congestion or other data-rate limiting factors.
58
After you read
1.Find the Russian equivalent for the wordphrases and sentences highlighted in the text.
2.Do you agree with the author that Design of both the system and control structure needs to be conducted with an understanding of the dominant process physics?
Mistakes are the portals of discovery. —James Joyce, Dubliners
Before you read text 18
How do you understand the word combination “Intelligent Building”?
Make your own example which describes the quotation above.
Text 18. WHAT DOES “INTELLIGENT BUILDING”
MEAN TODAY?
The discussions around "smart systems" and "intelligent buildings" have increased dramatically in the past five years, and for good reason — competition. Buildings are being forced to look at all aspects of their design — management, amenities, and operations — to be more attractive to owners and occupants than their competitors. At the same time, market pressure from consumers is forcing buildings to keep up with the rapid pace of innovation. Hence the move to smart or intelligent buildings.
Over the last half-decade, smartphones have gone from cool new gadgets to essential tools for conducting business. Temperature and lighting controls have gone from just thermostats and switches on the walls to WiFi-controlled from a mobile app. In this competitive market, tenants are asking questions about what the cellular coverage is like or what type of control they will have to reduce the energy consumption of their HVAC and lighting systems.
It is difficult to get through a day without hearing discussions about "big data," or the "Internet of Things" (IoT) in the news. As these solutions become commonplace over the next several years, they will enter the commercial building market with its thousands of devices that are controlling and monitoring systems and are ripe for data extraction and analytics.
But what does it actually mean to be a "smart" or "intelligent" building? "Smart" is used to describe advanced sensors, actuators, and related devices. A smart device or system is operated by a microprocessor, has programming to execute a pre-defined set of actions or sequence of operation, and communicates with external systems via some form of data network. "Intelligent" is used to describe a combination of smart devices and systems, with supervisory software enabling coordination and collaboration between the smart items. True intelligence implies the ability to automatically adjust operating parameters interactively between smart items to optimize building functionality. Optimization may benefit energy savings, occupant comfort, safety and security, or operational productivity, but at the core, an intelligent building is greater than the sum of its smart parts.
Since so many new technologies out there show promise, how does a building owner select the right solution or even ensure that the technology is a wise investment?
www.facilitiesnet.com/buildingautomation/article/What-Does-8220Intelligent-Building8221- Mean-Today-15283#
59
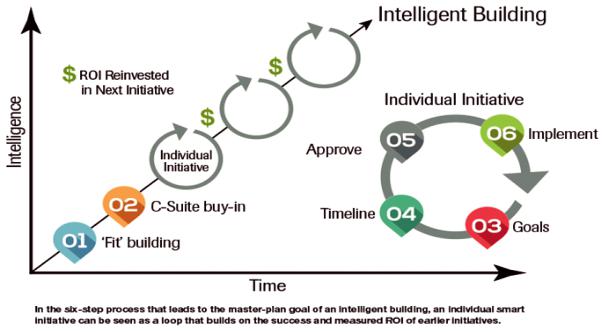
After you read
1. Can you describe the diagram which can describe the intelligent building process?
Before you read text 19
1. What must be taken into account when we speak about building automation system?
Text 19. BUILDING AUTOMATION SYSTEMS: What to Look for Getting the Best System for Your Application Requires Asking the Right Questions up Front
1.Building automation systems (BASs) are great at generating data. The trouble is, much of this data is useless for day-to-day operations. A good user interface will distill this data into useful information and present it in graphics, trends, color maps, and other easily understood formats.
The Crosby Independent School District near Houston used information from its BAS to compare energy use and classroom environments from all of its schools, and focused its efforts on the buildings that needed work. The result? During a 3-month period, the district reduced energy consumption by more than 1 million kilowatt hours and saved nearly $85,000. Equally important, it gave students a classroom environment where they could excel.
When investigating building automation systems (BASs), it can be difficult to know what features you need, what system is best, or even what to ask system providers. The following questions will help you get the answers you need to make an educated decision.
2.If your staff consists of dozens of engineers and technicians maintaining a large campus, you need to consider the capabilities of the system and all the tools and programs you'll need to support it. If your "staff" consists of one person who performs several functions at once, you may want to hire a vendor to provide the support and just focus on how your operator will use the system. Ask to see a demonstration of a system in a facility like yours. A system that works great for a large university may not be the best choice for an elementary school.
3.Building managers spend much of their time scheduling occupancy, adjusting setpoints, troubleshooting complaints, and responding to alarms. These functions should be as easy and intuitive as possible, whether you're fine-tuning a single room or shutting down the
60
