
Hackers Beware
.pdf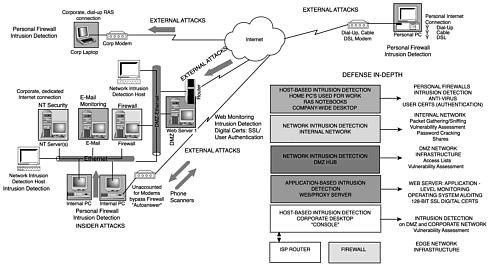
Multiple defensive measures are key; another key measure is to give entities, which can be users or computers, the minimal amount of access needed to do their jobs. This is called principle of least privilege and is discussed in the next section.
Principle of Least Privilege
Whenever anyone or anything is given more access than it needs, the potential for abuse rises. When it comes to security, people and programs should only be given the least amount of access needed to perform their jobs and nothing else. This is the foundation for the principle of least privilege. I consulted for one company that had given domain administrator access to everyone who worked in it. When I questioned people about this, their response was, “Someone might need that access at some point, so we figured it was better that they have it now than have to ask for it later.” In this case, the company was adhering to a principle of most privilege, giving users more access they would ever need, and they wondered why they had so many security issues. Users will always want more access than they need to do their jobs. I solve this by having the users tell me what job functions they need to perform, instead of the users telling me what access they need. Based on those functions, appropriate access can be provided to them.
From an application or software standpoint, this can be a bigger problem. If an application is running as root and an attacker can compromise the program, then he immediately has root access to the system. All applications should be reviewed to see what access they need to run correctly, and give those applications the least amount of access and nothing else. Limiting the access that users and applications have to a network will help protect it from potential abuse.
“Hackers Beware “ New Riders Publishing |
790 |
As with applications and software, these programs should be given the least amount of privileges needed for it to run. In order to give software the least amount of privilege, you need to know what is running on your system.
Know What Is Running on Your Systems
The only way you can secure your systems and network is if you know what is running on them. Things that you must be aware of are: operating system versions and patch levels, applications and version, open ports, and so forth. An attacker is most likely going to compromise your system by taking advantage of an open port or a vulnerability in the software you are running. If you do not know what is running on your systems, you will not be in a position to protect and defend against these types of attacks.
Many companies install servers and run applications, but they have no idea what is actually running on their systems. A common way that attackers break into a system is by compromising test or sample scripts that were automatically installed on the system when the software was installed. In most cases, the company did not know the software was present on their system. Therefore, the only way a company can secure its systems is if it knows its systems like the back of its hand.
If you know what is running on your systems, including key systems, you will be able to decrease the number of successful attacks against your system. Even with strong security, an attacker will still potentially be able to penetrate your defenses. In those cases, you need to be able to detect the attack as soon as possible.
Prevention Is Ideal But Detection Is a Must
Ideally, a company wants to setup its security so it can prevent all attacks. If this were the case, a company would setup its security once, and because it prevented all types of attacks, the company would be in good shape. Unfortunately, this is not the case. Not only does security constantly change, but as soon as a company connects to the Internet, it will never be able to prevent every single attack. There will always be some attacks that sneak through. The main reason for this is because a company connects to the Internet to provide additional functionality to the company and its employees. As long as legitimate traffic needs to flow in and out of the company, other traffic will be able to sneak in. The only way a company could come close to preventing all attacks is if it denied all in-bound and out-bound traffic. If this were done, it would defeat the purpose of connecting to the Internet. Unfortunately, when it comes to functionality versus security, functionality always wins. Hopefully, as awareness increases, this will change and companies will properly weigh security with functionality.
“Hackers Beware “ New Riders Publishing |
791 |
Because a company cannot prevent all attacks, a company must be able to detect when an attacker sneaks into its network. If an attacker can gain access to a network and the company is not able to detect him, then the attacker will have full access to the entire network. This is why a company must put measures in place to detect an attack as early as possible. The sooner a company detects an attack, the less overall damage the attacker will cause. A strong perimeter is a good starting part, but mechanisms for early detection and a warning system to detect attacks as quick as possible are key.
Not only is detection key, but if a company increases the security of its hosts by applying the latest security patches, it can decrease the chance of a potential compromise.
Apply and Test Patches
New attacks are discovered on a regular basis, and in most cases, they take advantage of an error in the underlying operating system or application. Therefore, the only way to protect against these attacks is to apply the appropriate patch from the corresponding vendor. Most vendors have special areas on their web sites where they post known security vulnerabilities in their software and where they make the patch available. It is key that you find these web sites and review them on a regular basis. This way, when a new patch comes out, you can apply it before an attacker breaks in. A key thing to remember is that if a vendor acknowledges a vulnerability, you can assume that all the attackers know about it. Therefore, every day that passes that your system is not patched is an open invitation for an attacker to compromise your system. Also, not only should patches be applied on a regular basis, but they should also be tested before they are loaded on an operational system. Just because a vendor released a patch does not mean that when you load it on your system, the system will continue to work properly. The only way to guarantee this is to test every patch on a test server before applying it to your production servers.
Because new patches are released all the time, this means that new vulnerabilities are being discovered constantly. So, just because a system is secure today does not mean it will be secure tomorrow. Therefore, a company’s security is constantly changing, and to keep up with it, checks of the system must be done on a regular basis.
Regular System Checks
Because companies are changing on a daily basis, there is no doubt that the computer systems and networks are also constantly changing. New systems are being added, new applications are being loaded, and older applications are being removed. Therefore, just because a system is
“Hackers Beware “ New Riders Publishing |
792 |
secure today does not mean that it will be secure tomorrow. To maintain a secure environment, systems must be scanned on a regular basis for any unusual changes. For example, if a new user account appears or new ports are open, this could indicate an attempted or successful attack. Unfortunately, security is not something that you do once and forget about, it is something that must be constantly reviewed and updated.
Now that we understand some of the key things that can be done to secure a company’s network and computers, let’s look at some of the problems that exist. Because so many companies have ignored security for so long, we will continue to have a large number of problems until companies start protecting their systems.
Things Will Get Worse Before They Get Better
The number of new attacks discovered is increasing daily. Not only is the number increasing, but so is the sophistication of the tools being developed to attack systems. Attackers no longer need to have knowledge of how an exploit works. If they can use a mouse and surf the web, they can compromise a system and gain access with no knowledge of what they did. This fact is down right scary. It is key that you understand this: If you think you are only trying to protect your site against a couple of sophisticated attacks, and you do not realize that anyone is a potential threat, then your company could still be quite vulnerable.
This book should be viewed as a starting point for understanding the threat of attacks and securing your systems. Having a secure network requires constant research of new exploits and an understanding of how they work, so your company can be secure. It is also critical for a company to realize that any change to a network or computer system, no matter how small it might seem, could have an impact on the security of the entire company.
Things will get worse before they get better because companies have ignored security for too long. But by reading this book, understanding what threats exist, and taking the necessary actions to secure your site, you are going a long way to protect your company from the myriad of attacks that currently exist. We know that there will be a lot of problems in the immediate future. Now let’s take a deeper look into what the future holds from a security standpoint.
What Does the Future Hold?
No one knows for sure what the future holds, but one thing I can tell you is that it is going to be interesting. In the beginning of this book, I mentioned that it is a good time to be an attacker. This means that there will be a lot of damage done to computer networks. I can also say that it
“Hackers Beware “ New Riders Publishing |
793 |
is a good time to be a security professional. As I just stated, things are going to get worse before they get better—this just means that there are some exciting years ahead of us.
So, let’s take a quick look at what might happen in the future based on the current state of affairs. My predictions for the future are the following:
•Security breaches will increase
•A major security event will happen
•Vendors will make secure products
•Companies will make security a priority
•We will have a secure world
I listed these items as bullets, and not numbers, because based on the current state of affairs, things will start changing, however, the events might not occur in the order in which they are listed. Some of these events may not occur at all, but based on what has occurred over the last 6 months, these are my predictions. Let’s look at each one of these events in detail.
Security Breaches Will Increase
Based on the current tools and attacks that exist, versus the current state and view of security at most companies, the number of attacks must increase. Attackers really have the upper hand. Until companies start following some of the general guidelines that I covered in this section and securing their sites, attackers will continue to have free reign. If you look at the average number of attacks occurring per month, the number keeps increasing. What is occurring is what I call the iceberg effect. When companies look at the problem, they say that yes, there are a lot of security breaches occurring, but it is not that bad. The problem with this logic is that what they are looking at are companies that detected a breach and reported it.
For additional information on the number of reported breaches and how they have increased over the last several years and last several months, two excellent sites are the CERT (Computer Emergency Response Team) and Security Focus. The CERT statistics can be found at http://www.cert.org/stats/cert_stats.html and the Security Focus statistics can be found at http://www.securityfocus.com.
When you look below the surface, the problem is a lot worse. First, a lot of companies have such poor security that they do not realize that their security has already been breached. Just because a company has not detected an attack does not mean that its security has not been breached. It just means that they have not detected it. Second, some companies that actually detect an attack might not want to report it to authorities.
“Hackers Beware “ New Riders Publishing |
794 |
This may be due to a fear of bad publicity or other reasons, so these companies might just take the loss and move forward. So, as you can see, the problems are a lot worse than what is publicly reported. At least for the near term, the number of attacks are going to increase whether the media is reporting the attacks or not. So, if your company has not had any attacks launched against it, or if you notice a huge slow down in attacks, it is likely that you are not looking in the right areas.
Because the number of attacks are increasing, it is only a matter of time before an attacker pushes the threshold and causes a major event.
A Major Security Event Will Happen
A major security event seems inevitable because there are too many security vulnerabilities on most systems, and the foundation of the Internet has minimal built-in security. When we combine these factors with how much companies and countries rely on the Internet, a major security event seems even more likely.
For example, what would happen to the US economy if the Internet stopped working? What if you woke up one morning and there was no more web, no more email, no more worldwide connectivity? What would that do to our economy? Think of how many companies would instantly disappear because they rely solely on the Internet for sales and delivery. As if that were not enough, other groups of companies would suffer severe financial consequences as well if they could no longer rely on the Internet. If you think stock market crashes have an impact on the economy, that would be nothing if the Internet stopped working for a couple of weeks.
To build on this, let’s look at a possible scenario to illustrate that there could be major security events occurring that we would not even know about. For example, what if a Fortune 100 company developed a new, state of the art technology that could make the company billions of dollars over the next ten years. Suppose this new technology would have had huge impacts for the local economy and the national economy. Then, two years into the development, after the company has hired a large number of people and has invested heavily in new factories and infrastructure to build the technology, suppose a foreign competitor releases a competing product. Because this competitor is first to market, the company that invented the technology would have to stop development because it would have lost the market share. Not only would the company lose the potential billions of dollars it would have made from this imaginary new product, but it has a huge impact on the economy because all those people hired for development would be laid off. Now, the company would likely have written this off to poor market analysis, but what if the true cause were that the competitor broke into the company’s network through the Internet and stole its secret?
“Hackers Beware “ New Riders Publishing |
795 |
Situations such as this are probably occurring all the time—companies loose large amounts of money, but they write it off to other problems. What if a company steps back and says, “Could this have been caused by a weakness in security?” Then, when the company goes through its logs, it may notice unauthorized access to its key servers. Because many companies do not appreciate the damage that Internet attacks can cause, there have probably been several major security events against companies that were caused by weak network security, and the companies did not even realize an intrusion occurred.
Now let’s look at some of the areas that could be impacted.
Areas That Could Be Compromised
In terms of major security events, there are the obvious attacks against a company’s security. In terms of corporate espionage, I think this is an area that will have increasing potential for damage. Corporate espionage is more of a threat to a specific company, but what if these attacks were launched against 5 or 6 companies in the same business area? Then it would have more of an impact on a company’s economy. Not only will corporate espionage between companies increase, but corporate espionage between countries will also increase. Think about this for a minute; if a foreign government can help give its local companies a competitive advantage over foreign competitors, it could have financial gains for the local economy.
Let’s take a step back and look at some of the areas that could be used to either take down the Internet or cause a major security event. There are many possibilities because the Internet and many company networks have minimal security built in. The following list is not even close to complete, but it should give you an idea of some of the key areas an attacker might go after:
•DNS
•TCP
•Operating System backdoors
DNS
DNS or the domain name system is responsible for resolving domain names to IP addresses. A question I like to ask people is this: “Can the Internet function without DNS?” Well, this is really a trick question. From a technical standpoint, the Internet does not care about domain names; it only cares about IP addresses to which it can route information. So, from a purely functional standpoint, the Internet can function without DNS. The key question is, “Would anybody use it?” If most people had to remember IP addresses, they would not use the Internet. So, from a usability standpoint, DNS is necessary. This means that if someone can take down
“Hackers Beware “ New Riders Publishing |
796 |
the DNS system, the Internet would come to a stand still, and no one would use it.
DNS works extremely well from a functionality standpoint, but like most systems, it has minimal built-in security. Attackers can access a company’s DNS server to find out information. Attackers can also send false entries to a DNS server to corrupt the information stored in the DNS server. This type of attack is known as a DNS cache poisoning attack. Also, like most systems connected to the Internet, DNS is susceptible to a Denial of Service attack. So, as you can see, if attackers can target DNS servers, they can cripple the usability of the Internet. Now, let’s take a look at one of the key protocols of the Internet, TCP.
TCP
TCP is one of the key protocols of the TCP/IP suite. Most traffic routed on the Internet uses TCP. As we have seen already, TCP has many potential vulnerabilities that an attacker can exploit. Like most protocols on the Internet, TCP works very well from a functionality standpoint, but it has minimal built-in security. Therefore, if attackers could figure out a way to stop TCP packets from being routed, or if they could cause packets to go to the wrong destination, they could take down the Internet.
Because most of the Internet relies on computers running operating systems, this provides another potential area for compromise.
Operating System Backdoors
A computer by itself is basically an object that has little value to its end users. What makes computers so valuable is the operating system that runs on the computer. By installing an operating system onto a computer, you turn the computer from a hunk of metal into a very functional device. Most computers on the Internet use one of two operating systems: Microsoft or UNIX. This is one of the reasons why new attacks have such a detrimental impact because they can be run against so many different computer systems. This leads to a huge potential problem. Because so much of the Internet relies on so few operating systems, if an attacker could somehow insert a backdoor into the operating system source code, and then it were distributed to everyone who purchased the software, the backdoor could be used at a later time to launch an attack. In such a case, by running a special code, every system with that operating system installed would be controlled by an attacker.
There have been many cases where operating system vendors’ computers have been compromised, and there are rumors that the source code for most operating systems is floating around the Internet. To make matters worse, what about internal employees? Does a company really trust everyone who works at the company? How hard would it be for a
“Hackers Beware “ New Riders Publishing |
797 |
malicious insider to insert some hidden back door into the source code? Unfortunately, the answer is it would not be that hard to do. When you have millions of lines of code, it is relatively simple for a programmer to program in some hidden features that no one in the company would detect. One example of this are Easter Eggs, and additional information can be found in Chapter 2, “How and Why Hackers Do It”.
Now that it seems almost inevitable that there will continue to be security breaches, including one or two major breaches. But, let’s look at the positive side of the equation—when things start getting better. This is a world were vendors start building more secure products and companies invest the appropriate funds.
Vendors Make Secure Products
At some point in time, vendors need to realize that they need to build more secure products. Some vendors are starting to respond, but it is not going to occur overnight. Also, the more pressure that people and companies put on the vendors will help them respond sooner. After there are major security events occurring, hopefully vendors will realize the importance of security and will build secure versions of their operating systems and applications. Perhaps vendors will realize this before there is a major security event, but is highly unlikely. When vendors begin making secure operating systems, companies can install them knowing they are secure and can withstand most attacks.
One of the main reasons why most operating systems are not considered secure is because the default installation is not secure. Software ships and installs with the most common features installed by default. This way, companies can get up and running as soon as possible with the least amount of effort. This works from a functionality standpoint but not from a security standpoint. If a company is willing to spend enough energy, it can remove any unnecessary services, close any unneeded ports, and make the operating system secure, however, this requires a lot of expertise and time. The problem is this puts vendors in a dilemma. On the one hand, if they ship their systems with all the required services running, it creates a system that is not secure. On the other hand, if they ship a system with no services running, then this requires the end user to have a high degree of expertise to turn on services, but the system is secure.
To get around this problem, in my opinion, vendors will start releasing two versions of their products:
1.Normal/functional version This version contains an out-of-the- box install of the operating system, which has most of the common features running and the latest security patches applied.
“Hackers Beware “ New Riders Publishing |
798 |
2.Secure version This version contains a minimal installation of the operating system. No additional services or ports are open and only the core functionality is running. If any additional services are needed, the end user must install them and configure the system manually.
By doing this, companies can pick which version they want, and if security is important, they can pick the secure version of the software. Today, if there were two versions, most companies would not pick the secure version. This statement is based on the fact that if enough companies today put pressure on vendors, there would likely be two versions. So, the next thing that companies need to do is make security a priority.
Companies Will Make Security a Priority
When it comes to business, money is king. In most cases, companies want to be as profitable as possible. So, why would a company spend millions of dollars on something that will not save them any money? The answer is they wouldn’t. Yet, that is how most companies look at security—they view it as a waste of money. Because many executives do not really understand the threat to their companies and what the risks are, they do not want to spend money on security. Once companies realize how much money they are loosing based on poor security, they will invest in a proper security infrastructure. In many cases, when companies come to this realization, they will drive the other events, such as influencing vendors to making more secure version of their products. If companies demand something and are willing to pay for it, vendors will deliver.
We Will Have a Secure World
Hopefully, at some point in the future, we will have a secure world. It will never be 100% secure, but hopefully we can do a much better job than the current state of affairs. It would be similar to today’s world. Most people would agree that here in the U.S. we live in a fairly safe world. That is the same goal of security and the Internet— to have a secure world where most systems and companies have a good level of security. Companies will still get broken into, but it won’t be nearly as bad as it is today.
Conclusion
To wrap up this book, remember that security is constantly changing. Just because a company is secure today does not mean it will be secure tomorrow. Reading this book and understanding what a company is up against is a great start, but your journey does not end after you finish this book, it is just the beginning. Security is a never-ending journey. With every journey there are some high points and some low points, but
“Hackers Beware “ New Riders Publishing |
799 |
