
Hackers Beware
.pdf• File-level rootkits: o TrojanIT
o Lrk5
o Ark
o Rootkit (there are several with this name)
oTk
•Kernel-level rootkits:
oKnark
o Adore
To give you an idea of how these programs work, we will cover one filelevel rootkit—trojanIT, and one kernel-level rootkit—knark.
TrojanIT
TrojanIT is a fairly simple file-level rootkit, but it is used to show how filelevel rootkits work and how powerful they are. Let’s go back to our earlier example where after an attacker created a Trojan version of login, he wanted to Trojan who and other programs, so an administrator could not tell whether the attacker was logged into the system. For example, if an attacker’s account name is evileric, and he has a directory called evileric with all his tools, he does not want the administrator to be able to find him using who or ls. He wants to create Trojan versions of these programs that ignore evileric anytime the system runs across it. Now if an administrator does an ls of a directory that contains a subdirectory called evileric, it will list every file and subdirectory except the one with the name evileric, which is what the attacker wants. TrojanIT is a program that does exactly this. Given 9 keywords, it will hide those keywords from the following programs:
•w
•who
•ps
•ls
•netstat
TrojanIT is simple to install and all attackers need to type are the following commands:
•Chmod +x install
•./install
To run the program, an attacker can either run each Trojan separately, specifying the 9 keywords as command-line options, or he can run the all program to configure all five programs at once. If he uses the all program, then all five programs will ignore the same 9 words. However, if he runs each Trojan separately, then each program can have a different 9
“Hackers Beware “ New Riders Publishing |
610 |
words that it ignores. For example, the following command would be run to ignore eric1 through eric9 for all five programs:
./all eric1 eric2 eric3 eric4 eric5 eric6 eric7 eric8 eric9
To remove the Trojan version of each program, which is necessary if the attacker wants to re-install the program with a different set of keywords, he would type the following commands:
•mv /bin/.ls /bin/ls
•mv /bin/.ps /bin/ps
•mv /bin/.netstat /bin/netstat
•mv /usr/bin/.who /usr/bin/who
•mv /usr/bin/.nop /usr/bin/w
Now let’s take a look at the power of a kernel-level rootkit.
Knark
Knark is a kernel-based rootkit that uses a loadable kernel module on Linux operating systems. Knark is easy to install and after it is installed, the victim is working in a virtual reality world created by the attacker. To install knark, an attacker would issue the following commands:
•Make
•Insmod knark
At this point, the program is installed and no rebooting of the operating system is necessary. After knark is installed, it generates lists that are stored in /proc/knark, which control the system and enable the attacker to know what is going on. The following are the lists and the corresponding information that the lists provide:
•Files Which files are hidden on the system.
•Nethides Lists of strings that are hidden in /proc/net/tcp and /proc/net/udp.
•Pids List of pids that are hidden on the system.
•Redirects List of programs that are redirected executables.
The developers have several programs an attacker can use to interact with the system, which enable the attacker to control knark. The following are some of the programs:
•Hidef Used to hide files and directories.
•Ered Used to configure executable redirection.
“Hackers Beware “ New Riders Publishing |
611 |
•Nethide Used to hide certain string values in /proc/net/tcp and /proc/net/udp, which are the programs that netstat uses to display information to an administrator.
•Rootme Used to gain root-level access.
•Rexec Used to remotely execute programs on the knark server.
Based on this list, these programs are easy to use, which makes it simple for an attacker to control a compromised machine. Remember, there is no password required to use these programs, so if knark is installed on a system, anyone can run these programs. This means that if an administrator is suspicious that his system might have been compromised, he can issue one of the commands, and if they work, he knows it has been knarked. As you can see, knark is very powerful and enables the attacker to have full control of the machine and redirect any executable without modifying any of the files.
Because there are several easy-to-use applications that an attacker can use to create backdoors on Windows systems, mainly NT, the following is a separate section where we look at several of these programs.
NT Backdoors
The following programs are used to preserve access or create backdoors on Microsoft operating systems, and they are discussed in the following sections:
•Brown Orifice
•Donald Dick
•SubSeven
•Back Orifice
The first exploit, Brown Orifice, actually uses Netscape to create a backdoor and can be run against Microsoft and UNIX operating systems. This shows how an attacker can run an exploit against a victim’s system, compromise the system, and create a backdoor by starting up a web server. The remaining 3 programs are remote control type programs, which after a target system is compromised, can be installed and enable an attacker to have full access to a remote host. They can also be installed through Trojan programs.
Brown Orifice Exploit
Brown Orifice is actually two exploits: one in the java core that allows Java to start a server that can take connections from any client; the
“Hackers Beware “ New Riders Publishing |
612 |
second enables Java to access any local files. Both are exception errors and are examples of poor error checking by applications.
Exploit Details
•Name: Brown Orifice
•OSs Affected: Netscape Communicator 4.0 through 4.74 running on Windows, Macintosh, and UNIX systems. (However, there is currently research about whether or not it will work on older versions of Netscape.)
•Protocols/Services: Uses two holes in the Java runtime libraries embedded in Netscape’s Web browser.
•Written by: Jacob Babbin
Protocol Description
The exploit is a demonstration of two holes in Netscape Communicator’s Java Libraries and a buffer overflow in the Java core. The first hole is an I/O exception error that gets the victim’s IP address through use of an embedded applet, which uses an exception error in one of the Java core libraries. After the exception error is reached, the payload of the daemon is dumped, which then sets up a listening port for itself. This daemon circumvents the Java security checks and allows any clients or attackers access. The second part of the exploit, again, uses an exception error to push arbitrary code through the overflow. This exploits an exception error that exists in the Java libraries of Netscape. It uses a malformed URL string that allows local file system access to the victim’s machine.
How the Exploit Works
Brown Orifice first does a browser check to make sure that a victim is running Netscape; the exploit doesn’t work for IE at this point. Then it starts the first part of its infection with an I/O Exception error, which overloads the Java security library buffer. The Java security library buffer dumps its payload of the daemon into the buffer and starts a listening port of 8080, which also bypasses all Java security checks. Then it begins to accept inbound requests and starts the BOHTTPD daemon. The listening port can be changed if the attacker wants to change it to help avoid detection. After the daemon starts, it sends a value back to the BOHTTPD.java file, which is the core of the exploit.
After the core receives the value that the system is successfully running a web server, it starts the second part of the exploit. The second half of the exploit is another exception error that uses a malformed URL request string to the victim’s file system. After the daemon receives acknowledgment that the server is started, it sends a malformed string of a URL request to the Java I/O of Netscape causing an I/O Exception error. The key point is that the malformed string is in reference to a request to
“Hackers Beware “ New Riders Publishing |
613 |
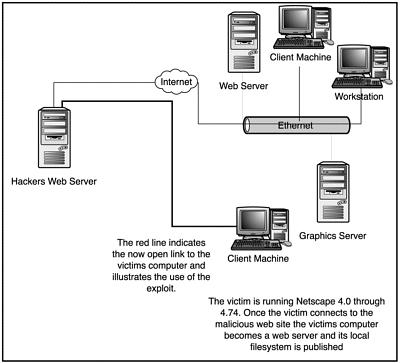
see the victim’s local file system, which is embedded in a created mimetype. Then an I/O Exception overflow is sent to the Input stream of Netscape forcing the loading of a pirate set of mime-types for file sharing. After the reloading of the pirate set of mime-types is complete, BOHTTPD sends a cgi script message to the author’s web site, which publishes the victim’s IP, address as being available now to hackers.
The last part of the exploit checks on the daemon side for web serving, and it checks on the overflow status of the URL request library.
Diagram
Figure 15.1 shows a diagram of how the exploit works to create a backdoor on the target machine.
Figure 15.1. Diagram of the Brown Orifice exploit.
How To Use It
One of the best possible uses of this exploit is to hide it on “security” web sites. With the popularity of web sites that offer to scan your network or computer for viruses or security holes, it would not be hard to fool some users into thinking that they were just having a security scan performed. Instead they are unknowing participants in having their machines turned into web servers and file-sharing platforms. The other method would be to take advantage of the fact that the exploit starts by using hidden fields of a cgi-driven web page. A malicious webmaster could have the exploit run
“Hackers Beware “ New Riders Publishing |
614 |
on either a well-known web site that has been hacked or on his own illegal site.
The author of this exploit, however, didn’t intend on making this exploit into a network-based attack. However, if an attacker uses social engineering or other tactics to get people to go to his hacked web site, or if he directs users to his hacked web site through a seemingly innocent email, this could be enough to infect them. Again, this exploit was not created to be used for network-based attacks. It is not designed to replicate itself or to be spread in any way other than to report on the successful infection of a victim’s machine to the author’s web site.
Signature of the Exploit
First, you can begin your search by looking for machines serving web content that are not supposed to, such as workstations. You can also block traffic coming from and going to potential attackers’ systems at your firewall. Another option is to look for web requests on the network that are not coming or going to your web browser.
How To Protect Against It
There are several things a company can do to protect against this attack. First, on your border router, you can block all traffic to and from the author’s web site. Then on your firewall, you can block all inbound and outbound traffic destined for port 8080. That port shouldn’t be open because it is not used by anything but personal web servers, and there is little reason in a business environment to run smaller, less protected personal web servers. Second, you should turn off the Server service on all Windows machines on your network that are not servers. Tell your users not to use Netscape versions from 4.0 to 4.74 until Netscape comes out with a patch for the exploit. If you have to use your Netscape browser, you can also go to Edit, Preferences, Advanced and turn off Java. However, the functionality of most web sites will have problems without Java enabled. Another option is to set your IDS to look for http packets that are not coming from your web servers. Filter for a destination address of the author’s site or for packets with the payload of “BOHTTPD” or “db_update.”
Source Code/Pseudo Code
Here is the start of the exploit. On the author’s web site, the basis is a cgidriven web page called BOHTTPD.cgi, which gives additional details.
BOHTTPD.CGI SOURCE
#!/usr/bin/perl
“Hackers Beware “ New Riders Publishing |
615 |
use CGI;
use BOHTTPD;
my $cgi = new CGI;
sub show_applet {
my $path = $cgi->param('path') ||
(is_ms ? '/c:/Program Files' : '/usr/local'); $path =~ s/^\/+//;
$path =~ s/\/+$//;
my $host = $ENV{REMOTE_HOST} || $ENV{REMOTE_ADDR}; my $port = $cgi->param('port') || 8080;
my $url ="http://${host}:${port}/${path}/";
my ($HOST, $PATH, $PORT, $URL) = map html_escape($_), $host, $path, $port, $url;
// This is the start of the exploit it is doing error checking to see which
browser the // // victim is running. If you are running Netscape then it
launches the exploit.
if (is_ie) { print qq< <p>
BOHTTPD does not yet work with Internet Explorer.
Get the latest version of Netscape Communicator in order to convert your browser into a Web Server!
</p>
>
} else { print qq<
<h3>Congratulations!</h3>
<p>You are now running BOHTTPD on port $port!</p> <p>Click the link below to access your browser's web server:</p>
<ul>
<li><code><a href="$URL">$URL</a></code> </ul>
<applet trustproxy=1 code="BOHTTPD.class" name="BOHTTPD" width=0 height=0>
<param name="host" value="$HOST"> <param name="port" value="$PORT"> <param name="path" value="$PATH"> </applet>
>
}
}
“Hackers Beware “ New Riders Publishing |
616 |
// This |
is where the exploit launches the start of the daemon |
process |
|
sub show_form { |
|
my $path |
= $cgi->param('path') || |
(is_ms ? |
'/C:/Program Files/' : '/usr/local/'); |
$path =~ |
s/^\/\/+/\//; |
$path =~ |
s/\/\/+$/\//; |
my $port |
= $cgi->param('port') || 8080; |
my ($PATH, $PORT) = map html_escape($_), $path, $port;
show_info;
print qq<
<form action="BOHTTPD.cgi:" method=post> <h3>Run BOHTTPD in Netscape</h3>
<ul>
>;
show_warning;
print qq< <table> <tr>
<td>Path</td>
<td><input type=text name=path value="$PATH"></td> </tr>
<tr>
<td>Port</td>
<td><input type=text name=port value="$PORT"></td> </tr>
<tr>
<td colspan=2>
<input type=hidden name=do value=applet> <input type=submit value="Start BOHTTPD"> </td>
</tr>
</table>
</ul>
</form>
>
}
sub show { show_header;
if ($cgi->param('do') eq 'applet') { show_applet;
} else {
“Hackers Beware “ New Riders Publishing |
617 |
show_form;
}
// This is the return of the exploit after it has completed both the first and
second parts // and is running smoothly.
show_footer;
}
print "Content-type: text/html\n\n"; &show;
END
Additional Information
For the source code, visit the author’s web site at
http://www.brumleve.com/BrownOrifice/.
Additional information on the exploit can be found at the August 8th 2000 bugtraq reports: http://archives.neohapsis.com/archives/bugtraq/200008/0054.html.
A Bugtraq member, Hiromitsu Takagi of Electrotechnical Laboratory, created a sample to show what can be done with a slightly-modified BOHTTPD server. You can see this sample at http://java- house.etl.go.jp/~takagi/java/test/Brumleve-BrownOrifice-modified- netscape.net.URLConnection/Test.html.
At this site, you can really see how this exploit impacts a broad range of operating systems.
Donald Dick 1.55
Donald Dick is a tool that enables a user to control another computer over a network. It uses client/server architecture, with the server residing on the victim’s computer. The attacker uses the client to send commands through TCP or SPX to the victim listening on a predefined port.
Exploit Details
•Name: Donald Dick 1.55 with Last Updated GUI Component fromVersion 1.53
•Location: http://people.alt.ru/computers/donalddick/
•Variants: Back Orifice, SubSeven, Netbus
•Operating Systems: Microsoft 95/98/NT/2000
•Protocols/Services: TCP/UDP, SPX/IPX
•Written by: Ryan J. Maglich
“Hackers Beware “ New Riders Publishing |
618 |
Protocol Description
The Donald Dick client connects to the server machine through two different protocols, TCP and SPX.TCP/IP is the most widely-used protocol for interconnecting computers among LANs and the Internet. Some of the advantages of using TCP/IP is that the protocol offers broad connectivity for different types of computers, support for routing of packets, and a centralized domain assignment for connections between organizations. Another one of TCP’s abilities is to correctly order packets when the computer receives them according to their sequence numbers. Two of the biggest drawbacks of TCP/IP are: It is relatively slow compared to other protocols, such as IPX, and second, the cost and effort needed to setup connections between global networks. The difficulty in setting up network connections is derived from the limit on the total number of available addresses. One of the advantages to using UDP is its capability to do checksumming of packets to make sure nothing was changed in transit. Although this secures the information in transit, it adds to the performance overhead causing many people to turn it off.
SPX is a reliable, connection-oriented protocol for communicating between computers. One of the features of SPX is that it uses IPX as a datagram service. While IPX packets are unreliable, SPX adds a service of packet acknowledgement. With this technique, packets are not repeated unless there is no acknowledgement of receipt. Some other advantages include ease of setup and fast connections. One of the disadvantages of SPX/IPX is that there is no centralized network numbering scheme. This would enable different networks to use the same set of addresses for computers, increasing traffic collisions and incorrectly routing packets. Another disadvantage of IPX is that it requires all links of the network to be able to handle 576 byte packets, therefore packets are limited to this maximum for safety.
How the Exploit Works
The creation of the server software revolves around two files. The first file is the initialization file called ddsetup.ini, which contains the default settings for the server and installer. The second file is ddsetup.exe, which constructs the installer file based on the ddsetup.ini file.
Many sections of the ddsetup.ini file determine the server’s/installer’s overall actions, ability to be detected, and its setup. The first section determines the default ports for the SPX and TCP protocols. The setup file can specify multiple listening ports for each protocol, or it can disable a protocol by not listing any ports. If the ports are prefixed with a “B”, then this port is also a datagram listening port, which is used by ddsfind, a port scanning/trojan finding tool.
“Hackers Beware “ New Riders Publishing |
619 |
