
Hackers Beware
.pdf“*SMBSERVER” is supposed to be some sort of wildcard, but it is optional and no current Microsoft platforms seem to accept it to open sessions.”
Next, the client initiates an SMB dialect (essentially a version) negotiation. It does this by sending a list of all the SMB dialects supported by the client to the SMB server, and the SMB server chooses the dialect it determines to be most appropriate. The 8 dialects supported by a WinNT 4.0 SP4 machine are as follows:
SMB: Dialect = "PC NETWORK PROGRAM 1.0"
SMB: Dialect = "XENIX CORE"
SMB: Dialect = "MICROSOFT NETWORKS 1.03"
SMB: Dialect = "LANMAN1.0"
SMB: Dialect = "Windows for Workgroups 3.1a"
SMB: Dialect = "LM1.2X002"
SMB: Dialect = "LANMAN2.1"
SMB: Dialect = "NT LM 0.12"
For this test, dialect 7, NT LM 0.12 was chosen by the SMB server, and the following is the output:
14 |
LEGIONBOX01 |
*SMBSERVER |
SMB: C |
Negotiate Dialect: PC |
NETWORK PROGRAM 1.0 |
|
|
||
15 |
*SMBSERVER |
LEGIONBOX01 |
SMB: R |
Negotiated Protocol 7 |
Both client and server having agreed to the dialect, the client now initiates a tree connect to the “hidden” IPC$ share on the SMB server.
16 |
LEGIONBOX01 |
*SMBSERVER |
SMB: C |
Connect IPC |
\\10.10.26.194\IPC$ |
|
|
||
17 |
*SMBSERVER |
LEGIONBOX01 |
SMB: R |
IPC Connected |
Once connected, a named pipe is created over the commands that can be passed.
18 |
LEGIONBOX01 |
*SMBSERVER |
SMB: C |
NT Create \srvsvc |
|
19 |
*SMBSERVER |
LEGIONBOX01 |
SMB: R |
F=0800 |
NT Created |
20 |
LEGIONBOX01 |
*SMBSERVER |
MSRPC: |
C Bind(0x0B) |
|
21 |
*SMBSERVER |
LEGIONBOX01 |
MSRPC: |
R Bind |
Ack(0x0C) |
With the named pipe now established, the client issues the share enumerate command, and the SMB server responds with the (unicode) names of all the shares on the system, including the “hidden”
“Hackers Beware “ New Riders Publishing |
490 |
administrative shares. Legion apparently ignores these administrative shares, however, they are not displayed within the GUI.
22 |
LEGIONBOX01 |
*SMBSERVER |
SRVSVC: CALL |
(Share Enumerate) |
|
23 |
*SMBSERVER |
LEGIONBOX01 |
SRVSVC: RESP |
(Share Enumerate) |
|
to Frame 22 |
*SMBSERVER |
SMB: C |
F=0800 Read 856 at 0 |
||
24 |
LEGIONBOX01 |
||||
25 |
*SMBSERVER |
LEGIONBOX01 |
SMB: R |
Status=OK |
|
Once the work is done, the client tears down the logical NetBIOS session, but leaves the NetBIOS-ssn TCP connection in place to support further communication between these two systems in the future.
26 |
LEGIONBOX01 |
*SMBSERVER |
SMB: C |
F=0800 |
Close |
|
27 |
*SMBSERVER |
LEGIONBOX01 |
SMB: R |
Closed |
|
ACK=176113 |
28 |
LEGIONBOX01 |
*SMBSERVER |
TCP: D=139 S=2168 |
|||
WIN=7801
Protocol Description—Brute Force Password Cracking Component
The Legion brute force password cracker is very simple from a protocol perspective. The client goes through a process almost identical to that previously described to establish a NetBIOS session with the SMB server. The main difference is that the brute force password cracker uses the actual NetBIOS name of the SMB server (supplied by the user) instead of *SMBSERVER as the Called NetBIOS name in the NetBIOS session request. After the session is established, the client issues an SMB account setup command using the client computer’s NetBIOS name as the account name.
1 |
[10.10.26.14] |
[10.10.26.231] |
SMB:: C |
Setup |
account |
LEGIONBOX01 |
[10.10.26.14] |
SMB:: R |
Setup |
|
|
2 |
[10.10.26.231] |
|
|||
After the account has been set up, Legion simply issues one SMB connect command after another to the NetBIOS share in question, each time passing a different pass-word. The SMB server dutifully responds to each of the invalid attempts with a “Bad password” reply and awaits further attempts.
3 [10.10.26.14] [10.10.26.231] SMB: C Connect A: \\SMBSHAREBOX1\LEGION
4 [10.10.26.231] [10.10.26.14] SMB: R Status=Bad password
5 [10.10.26.14] [10.10.26.231] SMB: C Connect A: \\SMBSHAREBOX1\LEGION
“Hackers Beware “ New Riders Publishing |
491 |
6 |
[10.10.26.231] |
[10.10.26.14] |
SMB: R Status=Bad password |
7 |
[10.10.26.14] |
[10.10.26.231] |
SMB: C Connect A: |
\\SMBSHAREBOX1\LEGION |
SMB: R Status=Bad password |
||
8 |
[10.10.26.231] |
[10.10.26.14] |
|
9 |
[10.10.26.14] |
[10.10.26.231] |
SMB: C Connect A: |
\\SMBSHAREBOX1\LEGION |
SMB: R Status=Bad password |
||
10 |
[10.10.26.231] |
[10.10.26.14] |
|
11 |
[10.10.26.14] |
[10.10.26.231] |
SMB: C Connect A: |
\\SMBSHAREBOX1\LEGION |
SMB: R Status=Bad password |
||
12 |
[10.10.26.231] |
[10.10.26.14] |
|
13 |
[10.10.26.14] |
[10.10.26.231] |
SMB: C Connect A: |
\\SMBSHAREBOX1\LEGION |
SMB: R Status=Bad password |
||
14 |
[10.10.26.231] |
[10.10.26.14] |
|
15 |
[10.10.26.14] |
[10.10.26.231] |
SMB: C Connect A: |
\\SMBSHAREBOX1\LEGION |
SMB: R Status=Bad password |
||
16 |
[10.10.26.231] |
[10.10.26.14] |
|
17 |
[10.10.26.14] |
[10.10.26.231] |
SMB: C Connect A: |
\\SMBSHAREBOX1\LEGION |
MB: R Status=Bad password |
||
18 |
[10.10.26.231] |
[10.10.26.14] |
|
19 |
[10.10.26.14] |
[10.10.26.231] |
SMB: C Connect A: |
\\SMBSHAREBOX1\LEGION |
SMB: R Status=Bad password |
||
20 |
[10.10.26.231] |
[10.10.26.14] |
|
21 |
[10.10.26.14] |
[10.10.26.231] |
SMB: C Connect A: |
\\SMBSHAREBOX1\LEGION |
SMB: R Status=Bad password |
||
22 |
[10.10.26.231] |
[10.10.26.14] |
|
23 |
[10.10.26.14] |
[10.10.26.231] |
SMB: C Connect A: |
\\SMBSHAREBOX1\LEGION |
SMB: R Status=Bad password |
||
24 |
[10.10.26.231] |
[10.10.26.14] |
|
Eventually, when the correct password is guessed, access is granted to the NetBIOS share and it is accessible to the client.
25 [10.10.26.14] [10.10.26.231] SMB: C Connect A: \\SMBSHAREBOX1\LEGION
26 [10.10.26.231] [10.10.26.14] SMB: R A: Connected
27 [10.10.26.14] [10.10.26.231] TCP: D=139 S=1073 ACK=73721 WIN=7361
It is worth pointing out that this brute force password cracking process can be very fast. In my specific case, where both systems were connected to the same LAN, all 12 attempts at guessing the password were completed within 200 milliseconds, and the Win95 server never gave any indication that it was under attack. At this rate, a 250,000-word dictionary could be processed in just over an hour.
Description of Variants
There are not necessarily direct relations between the following variants and Rhino9’s Legion, but the NetBIOS exploit is used. (Based on timelines
“Hackers Beware “ New Riders Publishing |
492 |
of development, Legion (as a concept) is likely in the bloodline of most of the following variants.)
Getsvrinfo 1.0 by AbuseLabs
This is a little program coded for Windows NT that obtains the parameters of a remote Windows NT server. Parameters include: NetBIOS name, NetBIOS domain/workgroup, amount of users currently logged in, and remote operating system version.
GNITvse rc1: GNIT Vulnerability Scanning Engine by glitch of ellicit.org
A vulnerability scanner that scans for the following: NBTStat Scan, Null IPC Session Establishment, Net View Scan, Enumerates all Global Groups, Enumerates all Local Groups, and Enumerates all User Accounts.
NB4 by Craig at freenet.de
This is a NBTSTAT scanner, written in Batch language, that scans from xxx.xxx.xxx.1 to xxx.xxx.xxx.255 for NetBIOS hosts.
NBName by Sir Dystic at CDC
NBName decodes and displays all NetBIOS name packets it receives on UDP port 137. Using the /DENY * command-line option, it responds negatively to all NetBIOS name registration packets it receives. Using the /CONFLICT command-line option, it sends a name release request for each name that is not already in conflict with machines from which it receives an adapter status response. The /FINDALL command-line option causes a wildcard name query request to be broadcast at startup, and each machine that responds to the name query is sent an adapter status request. The /ASTAT command-line option causes an adapter status request to be sent to the specified IP address, which doesn’t have to be on your local network. Using /FINDALL /CONFLICT /DENY * disables your entire local NetBIOS network and prevent machines from rejoining it.
Net Fizz 0.1 by Zorkeres
Net Fizz is a multithreaded net share scanner for Windows NT only. It is fast and has the capability of showing hidden shares.
NetBIOS Auditing Tool (NT) 1.0 by Secure Networks Inc.
The intention of this package is to perform various security checks on remote servers running NetBIOS file sharing services. In the grand scheme of NetBIOS and Windows NT security, NetBIOS Auditing Tool is fairly small. It is, without question, a step in the right direction, but like any software, it needs further development.
“Hackers Beware “ New Riders Publishing |
493 |
NTInfoScan 4.2.2 by David Litchfield
NTInfoScan is a security scanner designed specifically for the Windows NT 4.0 operating system. It is simple to use; you run it from a command line, and when the scan is finished, it produces an HTML-based report of security issues found with hyper-text links to vendor patches and further information. NTInfoScan is currently at version 4.2.2. It tests a number of services, such as ftp, telnet, and Web service, for security problems. In addition to this, NTInfoScan checks NetBIOS share security and User account security.
Winfingerprint 2.2.6 by Kriby Kuehl at technotronic.com
This program allows for advanced remote Windows OS detection. Some of the current Features are:
•Determines OS using SMB Queries
•PDC (Primary Domain Controller)
•BDC (Backup Domain Controller)
•NT MEMBER SERVER
•NT WORKSTATION
•SQLSERVER
•NOVELL NETWARE SERVER
•WINDOWS FOR WORKGROUPS and WINDOWS 9x
•Enumerates Servers
•Enumerates Shares including Administrative ($)
•Enumerates Global Groups
•Enumerates Users
•Displays Active Services
•Ability to Scan Network Neighborhood
•Ability to establish NULL IPC$ session with host
•Ability to Query Registry (currently determines Service Pack Level & Applied Hotfixes).
•Changes: Enumerates Transports, Retrieves Date & Time.
Winfo 1.4 by Arne Vidstrom
Winfo uses null sessions to remotely retrieve a list of user accounts, workstation trust accounts, interdomain trust accounts, server trust accounts, and shares from Windows NT. It also identifies the built-in Administrator and Guest accounts, even if their names have been changed. Of course, Winfo will show all hidden shares. One of the features is the -n switch, which activates null session mode. Without this switch, Winfo can be used to retrieve the information mentioned, but it uses an already established connection to the other computer. For example, if null sessions have been restricted, but you have a valid user account, then you can connect first and use Winfo to retrieve the information you need.
“Hackers Beware “ New Riders Publishing |
494 |
How the Exploit Works
Legion is not an exploit in the truest sense of the word, however it is a program that can be used in a malicious manner.
When used to enumerate shares on an NT system, Legion takes advantage of the fact that a default installation of an NT system allows anonymous users to connect to the interprocess communication share, IPC$, without a password. This connection can then be used as a conduit through which various information gathering commands can be passed to the target system. Although Microsoft has provided a mechanism to disallow these “null sessions” since Service Pack 3, a default installation of an NT system, even with the latest Service Pack applied, still allows anonymous connections of this type. In addition to file shares, other key pieces of information, such as users, groups, and Registry settings, can all be enumerated through this null session. Manual modifications to the Registry are required to remedy this vulnerability.
Legion is an effective tool when it is used as a brute force password cracker against NetBIOS shares with share-level access for several reasons. First and foremost, when directed against a Win9x system, the operating system provides no innate capability to detect the attack! No logs or audit trails are written and no alerts are generated that would inform the user of the system that it is under attack. Furthermore, Windows provides no mechanism for locking out access to a NetBIOS share after a given number of failed logon attempts. Additionally, the Windows implementation of NetBIOS file sharing provides no time penalty for an invalid logon attempt. Instead, an invalid logon attempt is immediately acknowledged as such, thus allowing the malicious client to quickly make additional authentication attempts. Finally, users choose poor passwords or no passwords at all too often when establishing shares.
Diagram—Share Enumeration
The following is a diagram of the process that occurs when enumerating shares:
“Hackers Beware “ New Riders Publishing |
495 |

Diagram—Brute Force Password Cracking
The following is a diagram of the process that occurs when cracking passwords:
“Hackers Beware “ New Riders Publishing |
496 |
“Hackers Beware “ New Riders Publishing |
497 |
How to Use Legion
When Legion is started, the initial GUI screen appears and gives the user two primary scan types from which to choose, “Scan Range” and “Scan List.” The Scan Range option enables the user to scan a range of IP addresses up to an entire class B network. To perform this function, the user simply has to check the Scan Range radio button, fill in the starting and ending IP addresses of the range they want to scan, choose a connection speed, and click the Scan button. This is shown in Figure 12.9.
Figure 12.9. The initial screen for Legion.
Similarly, to scan a list of individual IP addresses, the user only needs to check the Scan List radio button, type each target IP address into the Scan List box, click add, select a connection speed, and then begin the scan by clicking the Scan button. This is shown in Figure 12.10. If the user has a large list of target IP addresses to scan, Legion makes it easy to import the list of IP addresses from a standard text file by clicking the Import List button.
Figure 12.10. Providing Legion with the information it needs to run a scan.
“Hackers Beware “ New Riders Publishing |
498 |
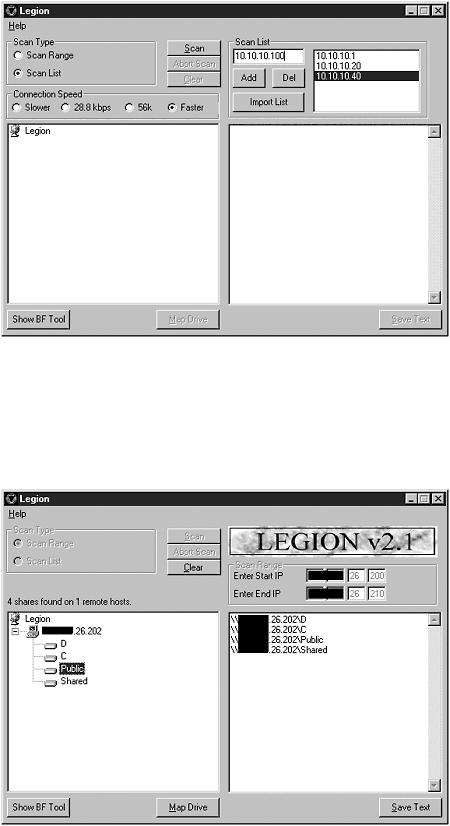
Regardless of the scan type chosen, the results are presented in a familiar Explorer-like tree view, as shown in Figure 12.11. By navigating this tree, the user can now map any share by highlighting it in the left panel and clicking the Map Drive button at the bottom of the screen.
Figure 12.11. Results from running a scan with Legion.
Legion then automatically maps the share to the first available drive letter and notifies the user of the action, as shown in Figure 12.12.
“Hackers Beware “ New Riders Publishing |
499 |
