
Hackers Beware
.pdf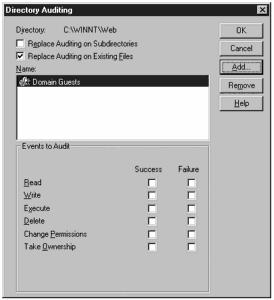
As you can see, you do not have to go in and select auditing for each file. By selecting the Replace Auditing on Subdirectories option, you can set the auditing at a higher-level directory and have it inherited by all the children underneath. To set auditing, you click Add, select the accounts or groups you want to have access, and then select which events are audited. If you want to know when a file is accessed no matter who it was who accessed it, you set the auditing for the Everyone group.
For example, to set auditing for the entire D drive where there is a proprietary database, you open up My Computer and select the D drive icon. You then right-click the icon and select Properties. Under Properties, you select Security, Auditing. At this point, a screen similar to the one shown in Figure 11.15 appears, where you go in and select the auditing policy for this object. After you are done, if you want it to apply to all objects on the D drive, you select the Replace Auditing on Subdirectories option and then the audit policy is applied to the entire drive.
To actually view the audit log, you select Event Viewer from the Administrators Tools group, as shown in Figure 11.18.
Figure 11.18. Event viewer for viewing the audit logs.
“Hackers Beware “ New Riders Publishing |
450 |
The thing to remember with NT is that there are three audit logs—system, application, and security—and each one is displayed in a different window. To switch between them, under the Log menu, select the corresponding log you want to view.
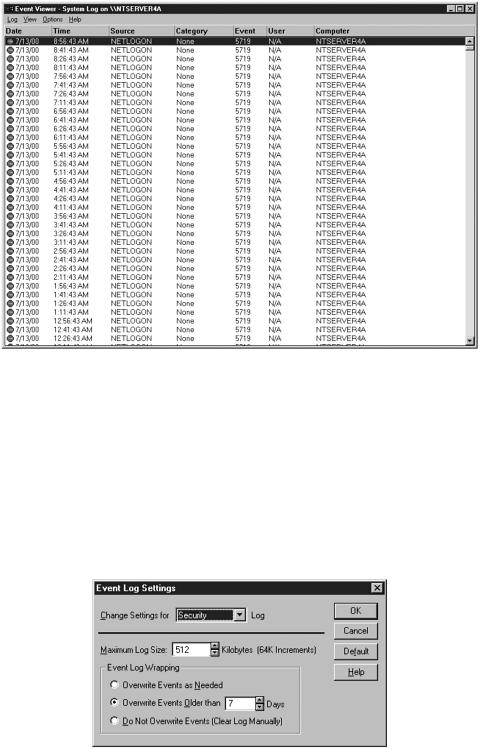
To determine how much space is used for the logs and when they are overwritten, you select Log Settings from the Log menu, as shown in Figure 11.19.
Figure 11.19. Settings for adjusting the audit logs.
If you overwrite your log files, remember that you might not have the data you need to determine if your systems have been compromised. Also, if you set the event log wrapping to Do Not Overwrite Events and you forget to save and clean up your logs, the logging could fill up all of your hard drive space and crash your system. I recommend using the setting Overwrite Events Older Than 7 Days and have an automated script that backs up the logs on a weekly basis to another drive. It is critical that a copy of the audit logs be made before they are overwritten; otherwise,
“Hackers Beware “ New Riders Publishing |
451 |
you lose important information that is required to either troubleshoot your systems or investigate an incident.
I was called to a client’s site because unusual processes were running on its server. It had auditing turned on and the setting was to overwrite every 15 days. I went through the audit logs and noticed that there seemed to be a pattern, but I needed to look at the logs from the last couple of months. I asked the administrator and he told me they do not back up their log files. They figure after 15 days they no longer need the information. In this case, I could not determine the cause of the problem because I did not have the proper information.
NetBIOS
NetBIOS (Network Basic Input/Output System) is a protocol that allows applications on different computers to communicate within a local area network. It does not support routing, so it cannot be used for a wide area network. Because it does not have a lot of extra features added, it is a nice lightweight protocol. It was created by IBM for its early PC Network, was adopted by Microsoft, and has since become a de facto industry standard. NetBIOS is used in various types of networks including Ethernet and Token Ring. NetBIOS frees the application from having to understand the details of the network, including error recovery (in session mode). A NetBIOS request is provided in the form of a Network Control Block (NCB), which, among other things, specifies a message location and the name of a destination. NetBIOS provides the session and transport services but does not provide a standard frame or data format for transmission.
NetBIOS provides two communication modes: session or datagram. Session mode lets two computers establish a connection for a conversation, allows larger messages to be handled, and provides error detection and recovery. Datagram mode is connectionless (each message is sent independently), messages must be smaller, and the application is responsible for error detection and recovery. Datagram mode also supports the broadcast of a message to every computer on the LAN.
NetBIOS is used by NT to communicate and uses the following ports:
loc-srv |
135/tcp |
Location Service |
|
loc-srv |
135/udp |
Location Service |
|
profile |
136/tcp |
PROFILE Naming System |
|
profile |
136/udp |
PROFILE Naming System |
|
netbios-ns |
137/tcp |
NETBIOS Name Service |
|
netbios-ns |
137/udp |
NETBIOS Name Service |
|
netbios-dgm |
138/tcp |
NETBIOS Datagram Service |
|
netbios-dgm |
138/udp |
NETBIOS Datagram Service |
|
|
“Hackers Beware “ New Riders Publishing |
452 |
|
netbios-ssn |
139/tcp |
NETBIOS |
Session |
Service |
netbios-ssn |
139/udp |
NETBIOS |
Session |
Service |
It is important to have a basic understanding of NetBIOS, because several of the exploits that we will cover in the next chapter exploit NetBIOS and attack ports 135 through 139. Therefore, unless it is critical, these ports should not be open through the firewall.
Service Packs
As we all know, there is no perfect operating system. After an operating system is released, security vulnerabilities and other problems are found. If Microsoft finds a bug or vulnerability that is a major problem in its system, it comes up with a patch. A patch usually fixes a single problem and is either a small program the user runs or is a sequence of steps a user performs to fix the problem. If it is a minor problem, Microsoft either releases a patch or waits for a service pack to be released. Service packs, or SPs, are released periodically and are meant to fix any bug or problem that has been found since the original operating system came out. In a lot of cases, people do not have time to apply every single patch that comes out, so they wait for a new service pack to come out and they apply that.
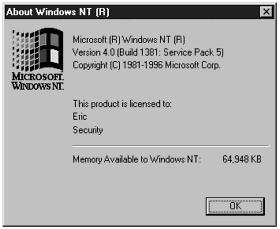
Usually, people refer to the version of the operating system and the service pack they are running. For example, I am running NT 4.0 with SP5. It is important to know what service pack you are running, because you could be vulnerable to a lot of security holes if you are running an old service pack. To find out what service pack you are running, you type the command winver from a DOS prompt, and the message shown in Figure 11.20 appears.
Figure 11.20. Message box showing what service pack a system is running.
This tells you a lot of information about the version and revision or service pack level you are running. It is important to keep up-to-date on the service packs, but it is especially important to test them before you apply
“Hackers Beware “ New Riders Publishing |
453 |
them to a production system. I know of several cases where applying a service pack actually caused other programs to stop working. For additional information on service packs, please see Microsoft’s web site at http://www.microsoft.com.
Resource Kits
As we all know, having the right tool to solve a problem is critical. Many times I have worked with NT and thought it would be nice if there were a tool that did such and such. If you haven’t used Microsoft’s resource kits, you might be missing out on the tool that will solve all of your problems— okay, I’ll be realistic—some of your problems. But even if it solves just one problem, it is worth it. Microsoft sells resource kits for its operating systems that provide a lot of useful tools and utilities that can help you be more productive. It has one for NT workstation and one for NT server. Because we are concentrating on NT server, we will focus on the Server Resource Kit.
The following is a breakdown of the category of tools, and under each category is a brief description of some of the tools and how they work. In security, having the right tool to fix a problem or even check for the problem in the first place is key. This list is meant to give you an idea of some of the additional tools that can be used to secure your NT systems (because the resource kit has more than 100 tools, they cannot all be covered):
•Computer/network setup
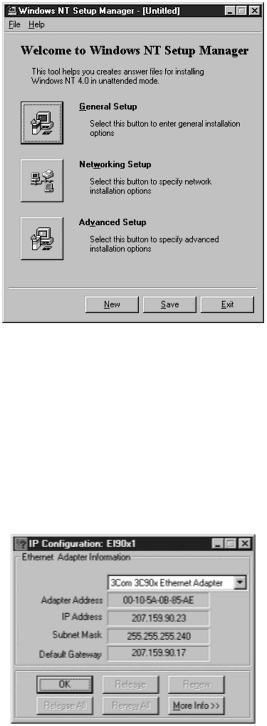
Windows NT Setup Manager helps you create answer files for installing NT in unattended mode, as shown in Figure 11.21.
Figure 11.21. Windows NT Setup Manager.
“Hackers Beware “ New Riders Publishing |
454 |
•NT network set up Design
SYSDIFF creates a snapshot of your system, before you install an application and after, to tell you what files or settings have changed.
WNTIPCFG is a graphical version of ipconfig, as shown in Figure 11.22.
Figure 11.22. Graphical display of IP information.
•Computer configuration
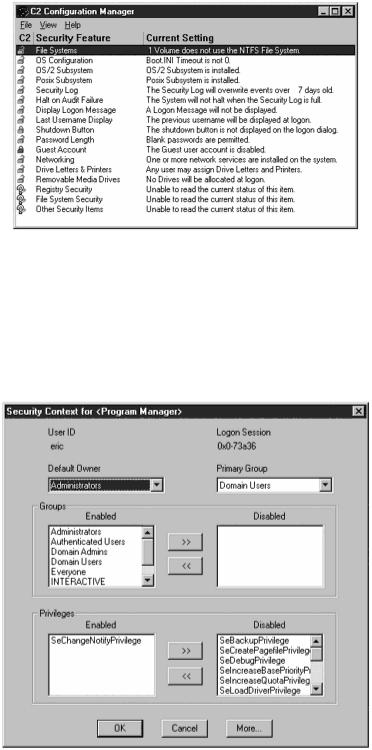
C2CONFIG (C2 Configuration Manager) helps bring your NT system up to a C2 level of compliance, as shown in Figure 11.23.
Figure 11.23. C2 Configuration Manager.
“Hackers Beware “ New Riders Publishing |
455 |
FLOPLOCK locks floppy disk drives for security reasons.
SECEDIT is a security context editor that allows you to modify security privileges and list the security contexts that are in use, as shown in Figure 11.24.
Figure 11.24. A graphical security context editor.
•Server/user management
ADDUSERS allows you to add users from the command line. Useful for running batch programs.
DELPROF deletes user profile information. GETSID returns the SID of a user account.
“Hackers Beware “ New Riders Publishing |
456 |
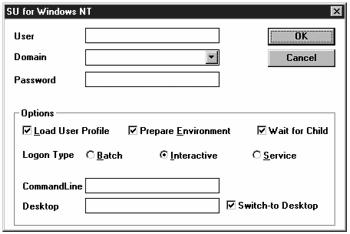
SU is a utility for Windows NT, which allows a user to become an administrator without logging off and logging back in again as a different user, as shown in Figure 11.25.
Figure 11.25. SU for Windows NT.
•Computer diagnostics
AUDITCAT helps in setting up auditing.
DUMPEL dumps audit log to a text readable file that can be incorporated into a database.
GETMAC gets the MAC address for a computer. KILL kills a running task.
TLIST shows all active tasks running on the computer.
•Network diagnostics
BROWMON is a browser monitor. DOMMON is a domain monitor.
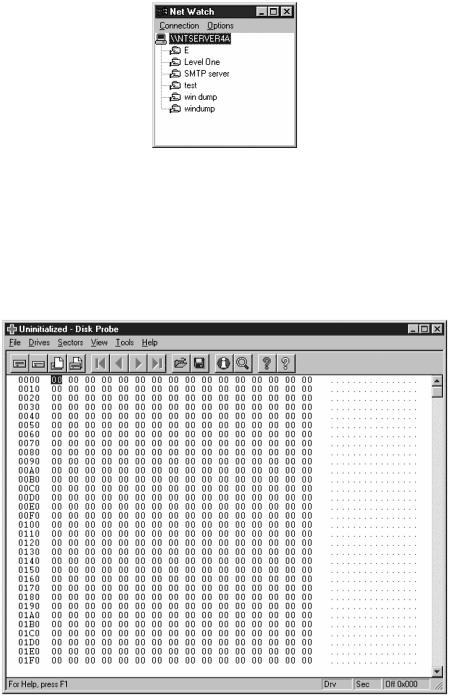
NETWATCH is a network watcher, as shown in Figure 11.26.
Figure 11.26. Net Watch, a network watcher.
“Hackers Beware “ New Riders Publishing |
457 |
•Disk/fault tolerance tools
BREAKFTM is an automated mirror break and restore utility.
DSKPROBE probes the hard disks, as shown in Figure 11.27.
Figure 11.27. Disk probe utility for probing the hard disk.
•Internet and TCP/IP
DHCPCMD is a DHCP administrator’s tool. DHCPLOC is a DHCP locator utility.
NTUUCODE is a 32-bit UUDECODE and UUENCODE utility.
•File/Batch tools
“Hackers Beware “ New Riders Publishing |
458 |
COMPRESS is a file compression utility.
FREEDISK checks to see if there is enough free disk. Useful to see if rogue programs are eating up your disk space.
SCOPY is a File copy with security.
•Registry tools
REGBACK is a Registry backup utility.
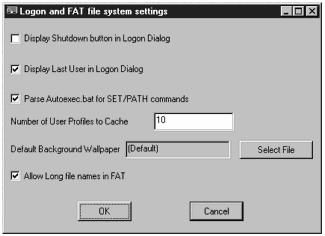
REGKEY gives logon and file system settings, as shown in Figure 11.28.
Figure 11.28. Logon and FAT file system settings.
•Desktop tools
WINEXIT is a Windows exit screen saver.
•Administration tools KERNPROF is a kernel profiler.
PASSPROP utility enables strong passwords. SHUTDOWN is a remote shutdown script.
•Developer tools
APIMON is an API monitor.
PULIST tracks what processes are running on the local system.
•Online documentation
“Hackers Beware “ New Riders Publishing |
459 |
