
Hackers Beware
.pdf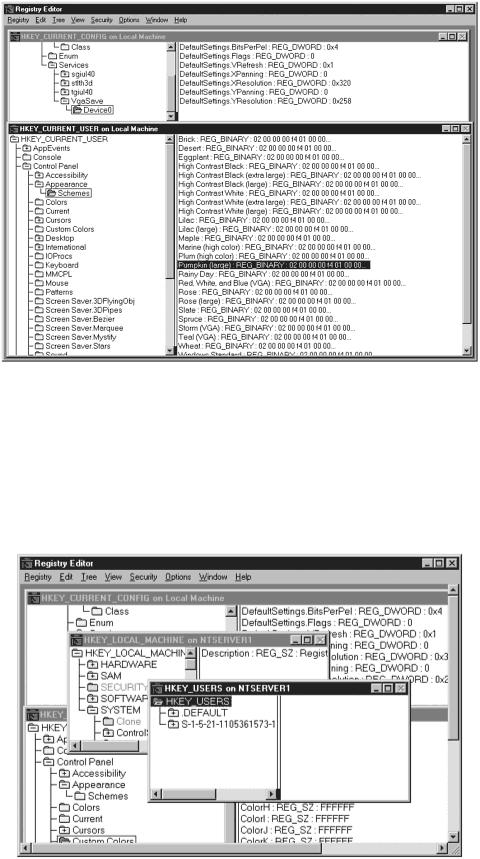
The top portion of the screen shows the VGA settings under CURRENT_CONFIG and the bottom half shows the different schemes for the appearance of the Windows GUI. With this program, you can also connect to a remote machine by clicking Select Computer from the Registry menu. Figure 11.6 shows a connection to a remote machine called NTServer1.
Figure 11.6. Connecting to a remote machine and accessing the Registry.
Now the Registry can be accessed on the remote machine. Pay attention to the titles in the window to tell whether you are accessing the Registry
“Hackers Beware “ New Riders Publishing |
440 |
values on the local or remote machine. To allow remote access, you set permissions on the following key:
HKEY_LOCAL_MACHINE\ SYSTEM\ CurrentControlSet\ Control\
SecurePipeServers\ Winreg
By viewing the permission for this key on the remote machine NTServer1, you can see that anyone in the Administrators group has permission to access the Registry remotely. The permissions for any key can be viewed by selecting Permissions from the Security menu. This is important to control and be aware of, because if these permissions are not set up correctly, an attacker can go in remotely and change critical keys, which could either crash your system or be used to gain additional access.
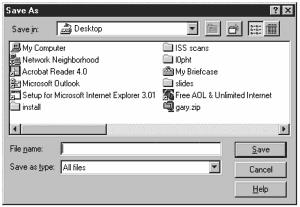
One other useful feature of the Registry that I will highlight is that you can save portions of the Registry to a text file. This is helpful if you are making changes and you are not sure what the effect will be. By saving it, if there is a problem, you can restore the settings at a later time. To save the values of a subtree, select Save Subtree as from the Registry menu. To restore the values, you select Restore from the Registry menu. In either case, you get a dialog box similar to the one shown in Figure 11.7, which allows you to select either the filename you want to save the Registry data to or the file you want to restore from.
Figure 11.7. Dialog box used to save the Registry.
The following is the output from saving the Control Panel/Custom Colors key:
Key Name: |
Control Panel\Custom Colors |
|
Class Name: |
<NO CLASS> |
|
Last Write Time: |
11/24/99 - 8:27 PM |
|
Value 0 |
ColorA |
|
Name: |
|
|
|
“Hackers Beware “ New Riders Publishing |
441 |
Type: |
REG_SZ |
Data: |
FFFFFF |
Value 1 |
ColorB |
Name: |
|
Type: |
REG_SZ |
Data: |
FFFFFF |
Value 2 |
ColorC |
Name: |
|
Type: |
REG_SZ |
Data: |
FFFFFF |
Value 3 |
ColorD |
Name: |
|
Type: |
EG_SZ |
Data: |
FFFFFF |
Saving and restoring the Registry to files is also helpful if you have to make several changes across multiple machines. Instead of going into each machine and manually making the changes, you can create a file that contains the changes, import it into each machine, and you are done in less time.
As you can see, understanding how the Registry works and knowing how to access it plays a key role in securing your machine. You will not become an expert in the Registry overnight, but it is important that you understand the basics of how it works.
Services Running
One of the general rules of thumb of security is the only way you can protect a system is if you know what services and applications are running on the system. Most people use an out-of-the-box install of an operating system and fail to realize that there are a lot of extraneous services that are running—services they do not need. I have seen several cases where a company’s NT server was compromised through a service that it was running either by accident, or the company did not know it was running in the first place. It is bad enough to have a compromise; it is worse if you get compromised because of an extraneous service running on your system that you did not know about.
To see what services are running, select Start, Settings, Control Panel, and click on the Services icon. This displays the screen shown in Figure 11.8.
Figure 11.8. Services screen showing what services are running on the system.
“Hackers Beware “ New Riders Publishing |
442 |

You can scroll down this list and see what services are running. When looking, it is important to note that even if a service is not started, it can still be a vulnerability. If the service is not installed at all and an attacker wants to exploit the service, he first must install the service on the machine, which is a lot of work. On the other hand, if the service is installed but not started, it is easy for an attacker to start it up—and all of a sudden your system becomes unsecure. When it comes to services, anything that is not needed should not only be stopped but also removed from the system.
An NT administrator needs to spend enough time with the systems to understand what services are essential for their environment and which ones are not. After this is done, clear configuration control procedures should be put in place so that all systems are built with the least amount of services running on the systems. Configuration control procedures also guarantee that as updates are made to the systems, they are done in a consistent manner across the organization.
It is also good practice that the administrator of a box periodically checks what services are running and make sure they do not change. All of a sudden, if three new services are running, it could be a good indication that a system has been compromised. It could also mean that an attacker loaded software on the system that required these services to be running, without the administrator’s knowledge. Therefore, it is critical that proper configuration controls be put in place so that the administrator and all key personnel have knowledge of what is being done to each system.
Account Manager
Not only is it important to know what services are running on your system, but also it is important to know what users have accounts on your system. A common point of compromise is when an attacker gains access, he creates a back door account that allows him to get back in at a later time. If you do not check what users have accounts on your system, you could have rogue accounts that allow access. To check who has an
“Hackers Beware “ New Riders Publishing |
443 |

account on your system, select User Manager for Domains under Administrator Tools. Figure 11.9 shows the main window that appears.
Figure 11.9. User Manager for Domains main screen.
The top of the screen shows the users and the bottom shows the various groups. It is also important to check what the account policy is for the accounts. The account policy controls things like how often a user has to change his password, the length of a password, and account lockout policies. Figure 11.10 shows the account policy screen.
Figure 11.10. Account policy screen.
“Hackers Beware “ New Riders Publishing |
444 |
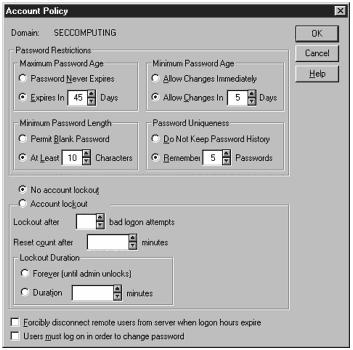
I have seen several cases where none of these policies are set, which means that a user can have an account for however long he wants with an extremely weak password. This means that it is simple for an attacker to crack a password, and when he does, he has access to the account for as long as he wants. As I stated earlier, the only way you can secure your system is if you know what is on it. Ignorance is deadly when it comes to security. Make sure you know who has access to your system and what the restrictions are.
For additional details on password policies and proper setting for NT passwords, please see Chapter 8, “Password Security,” and Chapter 9, “Microsoft NT Password Crackers.”
Network Settings
As with services and user accounts, you need to know what network services and protocols are running on your system. I have seen a lot of sites that just load all of the network protocols on their systems so they do not have to worry about any network services not running. The problem with this is that it provides additional avenues for an attacker to get into the system. To see what is happening from a network standpoint, select the Network icon from Control Panel. The screen shown in Figure 11.11 appears.
Figure 11.11. Network information for a Windows computer.
“Hackers Beware “ New Riders Publishing |
445 |
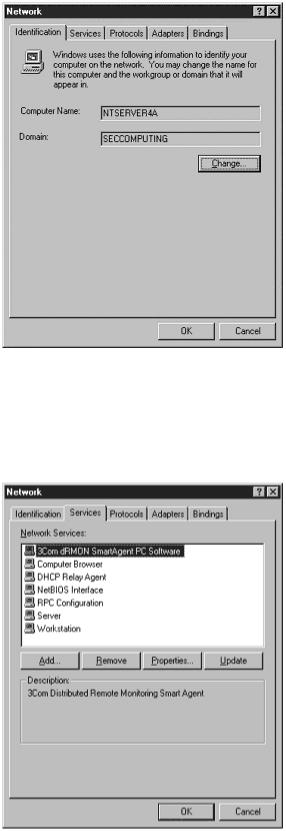
This tells you general information about your machine and what domain it belongs to. To see what network services are running, select the Services tab, shown in Figure 11.12.
Figure 11.12. Information about what network services are running.
Again, I know a lot of people who just load all of the services because they think it’s better to be safe than sorry—until they have a breach and then they are sorry they loaded all of the services. The same thing goes
“Hackers Beware “ New Riders Publishing |
446 |

for network protocols, which you get to by selecting the Protocols tab from the Network dialog box (see Figure 11.13).
Figure 11.13. Network protocols information.
In this case, only NetBEUI and TCP/IP are running—nothing else. On some systems that I set up, I only run TCP/IP. Remember that the fewer protocols, the less vulnerable the system. In most current environments, you can run only TCP/IP, but you should test it in your environment before removing any other protocols.
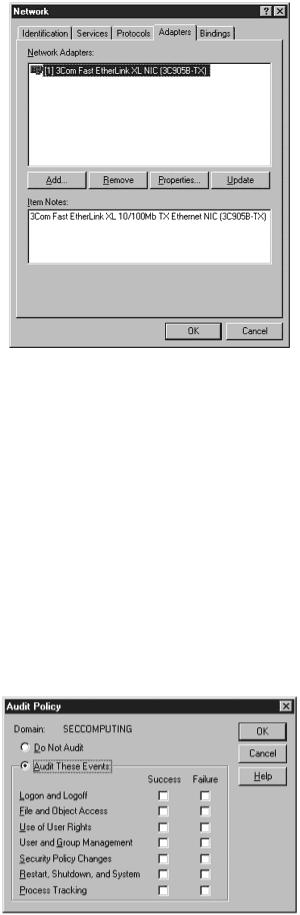
The last thing to look at is the adapters or network interface cards (NIC) that are connected to your system. Many people put multiple NICs in a server to bypass a firewall or other controls and the administrator has no idea that they are there. It is a good idea to periodically check and verify the number of network connections your server has by selecting the Adaptors tab, as shown in Figure 11.14.
Figure 11.14. Information on the number and type of network adapters.
“Hackers Beware “ New Riders Publishing |
447 |
Auditing
Remember our motto: prevention is ideal but detection is a must. No matter how good your security is, if you are connected to the Internet, you will never be able to prevent all attacks. Therefore, detection is critical. The only way you can detect what is going on with a system is with auditing. In this context, auditing refers to keeping track of everything that occurs on your system. These events are usually stored in an audit log or log file. This is different than security auditing, where you periodically check your system for vulnerabilities. If auditing is turned off, which it is by a lot of companies, you are flying blind, which is extremely dangerous. To enable auditing, select User Manager for Domains from the Administrators group, and under Policies, select Audit, as shown in Figure 11.15.
Figure 11.15. Audit Policy screen for turning auditing on.
“Hackers Beware “ New Riders Publishing |
448 |
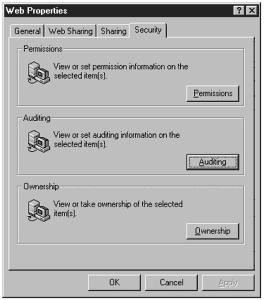
Figure 11.15 allows you to select which events are audited and under what conditions. The important thing to remember is this turns on auditing; however, if you want to audit the access of specific files or directories, you have to go into each object and turn auditing on. A lot of people turn on file and object access and then complain that their audit logs do not show access of specific files. You must go in and set it on each file or group of files. To turn on auditing for an object, right-click on the object, select Properties, and then select the Security tab, as shown in Figure 11.16.
Figure 11.16. Screen used to turn auditing on for specific files.
By selecting auditing, you can go in and set the properties for that object, as shown in Figure 11.17.
Figure 11.17. Setting auditing for a specific file or directory.
“Hackers Beware “ New Riders Publishing |
449 |
