
Hackers Beware
.pdf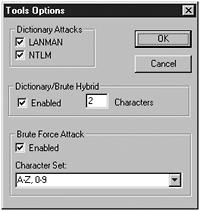
password that the brute force attack has. Figure 9.4 shows the Tools Options dialog box used to configure how L0phtcrack should run during a given session.
Figure 9.4. Tools Option Dialog Box containing L0phtcrack settings for configuring a Session.
This dialog box can be modified based on the user’s preference and the environment in which the program is run. For those using this program for the first time, or those who are not sure what the settings should be, L0phtcrack brings up the dialog box with default settings. L0phtcrack’s default settings are sufficient for most environments. The default configuration is a compromise between finding all passwords and minimizing the time it takes to run the program. Based on my experience with most systems, the default configuration can be run in a couple of days, and it finds most of the passwords on a system. By default, both LANMAN and NTLM dictionary attacks are enabled. The hybrid attack is enabled and is set to two characters. Brute force is also enabled with the character set of letters and numbers.
Window Menu
Because password cracking can be a sensitive issue, you might not want to leave the L0phtcrack program running in the foreground. If a user walks into your office and sees it running, they could get upset and cause a lot of problems. Even if your password policy states that the company can check passwords by cracking them, when a user actually sees it, it usually causes unneeded headaches for the over-worked security staff.
This program gives you two options for controlling the window:
•Minimize to tray
•Hide, Ctrl+Alt+L
It is important to note for both of these options that the program will not interrupt an active crack session. Although you cannot see the screen, the
“Hackers Beware “ New Riders Publishing |
370 |
program will still continue to crack passwords, it will just be harder for others to see. If you are running L0phtcrack on a dedicated machine, then you can just lock the screen, and the window features are not needed. On the other hand, if you are using the machine for other tasks, and you will be running crack for several days, then these features are quite useful. Not only does it protect the program from users seeing it, but it also makes it easier for you to work because it won’t keep getting in the way.
Minimize to Tray This option minimizes the current window and a small icon appears in the tray. The tray is in the lower right side of most systems, and it usually has several icons located in it. To bring the program back up, you just click the icon in the tray. This is good from a convenience standpoint because it will not be active on your screen or get in the way of other programs. From a covert standpoint, a user can still tell it is running, if they see the icon in the tray. To put L0phtcrack in more of a covert mode, use the hide, Ctrl+Alt+L option.
Hide, Ctrl+Alt+L The Minimize to tray feature is beneficial, but if someone looks closely at the machine, they can tell that the program is running because they would see the icon in the tray. In such cases, you want to hide the window completely. By clicking the hide, Ctrl+Alt+L menu option, you do just that—hide the window—so that someone cannot tell it is running. The program does not show up in the tray and does not show up in task manager. The only way to know it is running is by hitting the appropriate key sequence. In this case, after the window is hidden, the only way to get it back is by simultaneously holding down the control key, the alt key, and the letter L.
What makes this feature scary from a security standpoint is if the Packet Capture window is open (this is the feature that pulls passwords off the network when people logon), it will be hidden as well, and it will continue pulling off passwords. If an attacker can gain access to a user’s computer, he can upload the program, start up Packet Capture, and hide it. Unless the user knows the key sequence (which most users do not), she has no way of knowing that it is running unless she looks at process lists, which very few users actually do. The attacker can then come back at a later time and pull off the passwords.
Help Menu
The Help menu gives the user additional guidance in using the program. The three options are:
•About L0phtcrack
•L0phtcrack Web site
•L0pht Web site
“Hackers Beware “ New Riders Publishing |
371 |
About L0phtcrack This item gives general information about the version of L0phtcrack you are running. The information it displays is program version, serial number, and the registration code, if applicable. This is helpful if you are having problems determining which version of the system you are running.
L0phtcrack Web site This option opens up your default Internet web browser and tries to connect you to the L0phtcrack web site. This is useful for finding updates, additional program information, and troubleshooting hints. This might seem obvious, but these features only work if you have an active Internet connection.
L0pht Web site This option opens up your default Internet web browser and tries to connect you to L0pht’s web site to find information about other products and tools they have. If you have not been to their web site, I highly recommend it. L0pht has a lot of useful products and information for the security professional.
Running L0phtcrack
To get the most out of this product, there are some basic steps you should follow when running the program. The following are the key steps:
1.Installation
2.Running L0phtcrack
3.Acquire password hashes
4.Load password hashes
5.Load dictionary file
6.Configure Options
7.Run Program
8.Analyze results
After you load the password file, the main window displays the information. Figure 9.5 shows an uncracked password file.
Figure 9.5. L0phtcrack with an Uncracked Password File loaded.
“Hackers Beware “ New Riders Publishing |
372 |
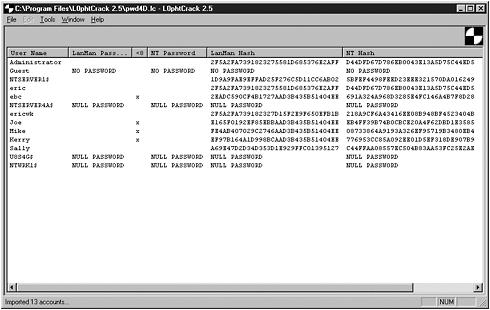
As you can see, the system is using both LANMAN and NT hashes. One important fact to point out is that any accounts that do not have passwords, or Null passwords, are automatically displayed, as well as passwords with less than 8 characters. Remember that LANMAN hashes break the password down into two 7-characters pieces, which means the second half of a password that is 7 characters or less is the same for all passwords. In other words, any password where the second half is AAD3B435B51404EE is less than 8 characters, which is the hash value of all zeros. At this point, you can configure the program and run it.
Just to give you an idea of how fast L0phtcrack is, Figure 9.6 shows the results after running the program for 2 minutes on a 500mhz Pentium with 64MB of RAM. As illustrated, a bulk of the passwords where cracked in a short period of time.
Figure 9.6. L0phtcrack almost halfway through the cracking process.
“Hackers Beware “ New Riders Publishing |
373 |
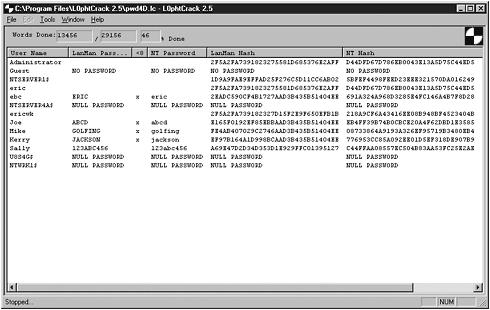
As you can see, L0phtcrack is a feature-rich program that is optimized for the NT environment. It also has a very easy-to-use GUI that is fairly straightforward. If you have an NT environment, I highly recommend that L0phtcrack be part of your security toolbox.
NTSweep
NTSweep is a password-cracking program for NT that takes a different approach than most other password cracking programs. Instead of downloading the encrypted passwords and cracking them off-line, NTSweep takes advantage of the way Microsoft allows users to change their passwords. Basically, any user can attempt to change the password of any other user, but to do so successfully, the user needs to know the other user’s original password. If the user knows the original password for an account, then NT enables the user to change the password, if the user does not know, then the attempted password change fails. NTSweep takes advantage of this fact by trying to change account passwords.
Here is how NTSweep works. Given a word, NTSweep uses that word as the account’s original password and then tries to change the user’s password to that same word. If the primary domain controller (PDC) returns a failure, then you know that is not the password. If the PDC returns a success, then you have just guessed that account’s password. Because you successfully changed the password back to the original value, the user never knows that his password has been changed. This program was written by Dave Roth and can be downloaded from www.packetstorm.securify.com.
NTSweep is very powerful because usually it can be run through a firewall, and it does not require any special privileges to run. With other methods,
“Hackers Beware “ New Riders Publishing |
374 |
you need to have administrator access or some way of accessing the SAM database. NTSweep can be run by any user on the system, and it does not require any special access. Also, because many companies allow this traffic through their firewall, it can be run by anyone on the Internet.
NTSweep does have some limitations, so it is not the ideal tool under all circumstances. First, it is very slow to perform. If you want to perform a dictionary attack, you have to run the program many times, passing it different dictionary words each time. You could easily write a script that would do this, but the program would take a long time to run. Second, this information is logged. Whenever a user attempts to change his password and fails, this information is logged and can be viewed with an event viewer. This makes it easier for an administrator to detect that this type of program is being run. The key thing to remember is that you must have logging turned on, and you must review the log file on a regular basis to detect this type of attack. Thirdly, guessing programs that use this technique do not always give you accurate information. There are cases where a user is not allowed to change his password. In such cases, the program returns a failure even though the password was correct.
Requirements
NTSweep runs in a DOS Window on any version of Windows. Based on this fact, the requirements are minimal. The program is downloaded from the Internet as a zip file, so an uncompression program is required. NTSweep works by going to the PDC on the network and trying to change each password. Therefore, a network connection is required.
Configuration
Remember with Windows programs, you download executable code, so there is minimal configuration required. The program has a main executable file and several DLL’s it needs to operate. As long as the executable and DLL’s are placed in the same directory, you are ready to run the program.
Running the Program
To run the program, you open up a DOS window, cd to the directory where the files are located, and type: ntsweep password-guess, password-guess is the word you want the program to use when it tries to change the password for each account. This is useful in cases where you know that several people in a company use a particular password, but you just do not know which accounts. By running NTSweep with that password, you can find out the user IDs of those accounts.
When the program runs, the results of the accounts it cracked are displayed on the screen. Basically, if the password change failed, then that
“Hackers Beware “ New Riders Publishing |
375 |
is not the user’s password. If the password change was successful, then you know the password for that account. The following is the output from running the program with a password guess of eric:
NT Password Sweep
A Wiltered Fire Production
Executing "net user /domain" for user list... [26 users loaded]
Checking for password [eric]
Attempting to crack Administrator ... [failed] Attempting to crack cathy ... [failed] Attempting to crack eric ... [success] Attempting to crack frank ... [failed] Attempting to crack john ... [failed] Attempting to crack karen ... [failed] Attempting to crack lucy ... [failed] Attempting to crack mary ... [failed] Attempting to crack mike ... [failed] Attempting to crack pat ... [failed] Attempting to crack sue ... [failed] Attempting to crack tim ... [failed] Attempting to crack tom ... [failed]
The successful results are also stored in a file called ntpass.log. So, in this case, the log file contains the following entry, eric:eric, because that is the only account that has a password of eric.
Results
Because this program does not use a dictionary or brute attack to guess passwords, the results from running this program can be misleading. If I gave the program a word, it will successfully find every account that has that password. Therefore, this program is only effective if you have a good idea that a particular user has a certain password. I guess someone could write a script that feeds this program every word in a dictionary to see which ones it finds. In this case, it would be treated as a slow dictionary password cracker.
NTCrack
NTCrack is a part of the UNIX password cracking program, crack, but in the NT environment. NTCrack works similarly to crack in UNIX, but NTCrack is severely limited in its functionality. Instead of extracting the password hashes, like other password cracking programs do, it works similarly to NTSweep. You have to give NTCrack user IDs and password combinations to try, and it lets you know whether or not it is successful.
“Hackers Beware “ New Riders Publishing |
376 |
Requirements
NTCrack runs in a DOS Window on any version of Windows. Based on this fact, the requirements are minimal. The program is downloaded from the Internet as a zip file, so an uncompressing program is required. NTCrack works by going to the PDC on the network and gathering information for the appropriate account. Therefore, a network connection is required.
Configuration
NTCrack is a single executable that is run from a Windows DOS prompt. The program runs in a DOS window, and the user tells it what account to crack by passing it command-line options. The source code for the program can also be downloaded when you download the executable.
Running the Program
To run the program, you go to a DOS window, cd to the correct directory, and type the following command:
Ntcrack /n=computer-name /u=user /p=password /debug
The computer name is the machine that contains the account database, the user is the name of the account, the password is the password you are trying to guess, and debug turns on verbose mode, so that additional information is provided. When the program runs, it outputs whether or not the password is successful.
Results
As you can see, NTCrack is very similar to NTSweep, in terms of performing an online attack as opposed to downloading the entire SAM database, and it has similar limitations. Because this program is only as good as the words that the user provides it with, NTCrack can be treated as a low-end dictionary attack program.
PWDump2
PWDump2 is not a password-cracking program, but it is used to extract the password hashes from the SAM database. Because L0phtcrack has this feature built in, you might be wondering how such a program is useful. First, it provides a small, easy, command-line tool that can be used to extract the password hashes. Second, there are cases when the current version of L0phtcrack cannot extract the hashes. SYSKEY is a program that can be run on NT to provide strong encryption of the SAM database. If SYSKEY is in use, then L0phtcrack can no longer extract the password hashes, but PWDump2 can. Also, to extract the password hashes with
“Hackers Beware “ New Riders Publishing |
377 |
Windows 2000, you must use PWDump2. L0phtcrack cannot extract the hashes because a stronger encryption scheme is being used to protect the information. So, as you can see, there are some cases where PWDump2 is very helpful to have.
PWDump2 works by performing DLL injection, which is used to execute certain code, that can then extract the password hashes from the SAM database. Source code is also available, so it can be customized to meet an administrator’s needs. PWDump2 is also available from www.packetstorm.securify.com.
Running PWDump2
PWDump2 runs in DOS Windows, and the pwdump2.exe and corresponding DLLs must be in the same directory. You can then run PWDump2 on the local machine, and it will dump out the user IDs and corresponding password hashes. The following are the results from running PWDump2 on an NT 4.0 system:
Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16
ae931b73c59d7e0c089c
0:::
eric:1000:2eadc590cf4b1727aad3b435b51404ee:691a324a968d3285e4f
c146a4b7f8d28:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73
c59d7e0c089c0:::
This information can then be imported into L0phtCrack.
Comparison
As we have covered previously, there are several different tools that can be used to crack NT passwords. Table 9.1 is a summary chart to help you pick the tool that is right for your environment:
Table 9.1. Comparison of the Effectiveness of NT Password Cracking Tools. |
|
||||
Features |
|
L0phtCrack |
NTSweep |
NTCrack |
PWDump2 |
Platforms they run on |
|
NT |
NT |
NT |
NT |
|
|
|
|
|
|
Passwords they crack |
|
NT |
NT |
NT |
NT |
Dictionary attack |
|
Yes |
No |
No |
N/A |
Brute force attack |
|
Yes |
Yes |
Yes |
N/A |
Hybrid attack |
|
Yes |
No |
No |
N/A |
|
|
|
|
|
|
Distributed |
|
No |
No |
No |
N/A |
Time to perform dictionary attack |
|
240 seconds |
N/A |
N/A |
N/A |
Ease of install (1 easiest, 4 most difficult) |
|
1 |
1 |
1 |
1 |
Ease of use (1 easiest, 4 most difficult) |
|
1 |
2 |
3 |
4 |
“Hackers Beware “ |
New Riders Publishing |
|
378 |
||

Most features (1 most features, 4 least features) |
1 |
2 |
3 |
4 |
|
|
|
|
|
As you can see, in terms of power and functionality, L0phtcrack is the tool of choice for cracking NT passwords. With NTSweep and NTCrack, the user has to provide the user ID and password.
Extracting Password Hashes
To crack passwords, one must be able to obtain a copy of the password hashes from the NT PDC. This section looks at some of the ways a copy of the hashes can be obtained. If the person running the password-cracking program is an administrator, then it is very easy, he can just dump the password hashes from the PDC. An administrator can do this either by using L0phtcrack or by running the PWDump2 utility. If the person running the program is not an administrator, then he could obtain the password hashes in one of the following ways:
•Sniffing passwords off of the network
•Booting into another operating system and copying the SAM
•Using LINNT to obtain administrator access
•Obtaining a copy from c:\winnt\repair or backup directory
•Obtaining a copy from a tape or emergency repair disk
As you can see from an administrator’s standpoint, there are plenty of ways an attacker can obtain a copy of your company’s password file. Therefore, it is critical that you read the next section and implement as many of the safeguards as possible to protect your passwords from being cracked.
Protecting Against NT Password Crackers
There is no practical way to completely prevent password cracking. As long as you have a network, and you are connected to the Internet, attackers or insiders will be able to find some way to extract or capture password hashes and crack them. The goal of this section is to make it a lot harder for attackers to perform password cracking and to make it take a lot longer for them to run their programs. For example, if someone can extract your password hashes, but it would take them 100 years to brute force the passwords, and all users have to change their password every 90 days, then you are in very good shape. By the time the attacker cracks the passwords, the usefulness of the information has expired because the password is no longer valid.
The following are some ways to increase the security of NT passwords:
•Disable LAN Manager authentication
•Enforce the use of strong passwords
“Hackers Beware “ New Riders Publishing |
379 |
