
Hackers Beware
.pdfChapter 8, “Password Security,” the operating system does not store passwords in clear-text. The passwords are encrypted using a one-way hash algorithm and are stored on the system, so that they are protected from unauthorized disclosure. L0phtcrack computes the passwords from a variety of sources using a variety of methods. The end result is a state of the art tool that provides a quick, easy, and efficient way to determine a user’s plain text password. L0phtcrack works on Microsoft NT and has three main modes it uses to crack passwords: dictionary, hybrid, and brute force attacks. For additional details on each of these modes, please see Chapter 8.
L0phtcrack is available from www.l0pht.com and is one of the best NT password cracking programs on the market today. Not only does it have a nice, easy-to-use graphical user interface (GUI), but it also takes advantage of the two design flaws in NT, which enable L0phtcrack to be incredibly fast. Currently, when you download the program, you get a 15day trial version. After that, you can purchase a version for $100 that runs on a single machine. If you work in the NT environment and want your systems to be secure, it is probably the best investment you can make for security. For everything that you get, it is a bargain. I am not affiliated with L0pht, I just feel that they have done a great job on the program, and I have found that it is a necessary tool that any NT security administrator must have in their toolbox.
What makes this program so valuable are all the additional features it has. Most password-cracking programs only crack passwords and assume that the administrator already has the encrypted passwords and the dictionary he wants to use. L0phtcrack does not make any of these assumptions and includes all these utilities in one program. Some of the additional features L0phtcrack offers are the following:
•Password cracking
•Extracting hashes from the password registry
•Loading the password from a file
•Sniffing the passwords off of the network
•Performing a dictionary, hybrid, brute force, or combination attack
As of the writing of this book, the latest version of L0phtcrack is 2.5, and it has several new features:
•Increased speed
•Combination and hybrid cracking
•Accurate cracking status
•Added password capture via sniffing within the GUI
•Custom character set for foreign languages
L0phtcrack Performance
“Hackers Beware “ New Riders Publishing |
360 |
To show how fast the program is, the following statistics were taken from L0pht’s Website for a large high tech company:
•Cracked 90 percent of the passwords in under 48 hours
•18 percent of the passwords cracked in under 10 minutes
•Most domain admin accounts cracked
•These results were from a system with a password policy that required a minimum of 8 characters with one numeric or special character.
Based on my experience, these results are extremely conservative. I usually find the following:
•Cracked 90 percent of the passwords in under 5 hours
•18 percent of the passwords cracked in under 5 minutes
•Most domain admin accounts cracked
•Most companies only require a minimum of 8 character passwords but have no other restrictions.
This data is based on a wide array of companies ranging from Fortune 500 companies to mid-size companies of 500 employees. What is interesting is that the results do not vary much between different types and different sizes of companies. Everyone seems to have a problem with having strong passwords. Whether you are a Fortune 100 company or a 20 person startup, there is a good chance that most of your accounts have vulnerable passwords.
The following is another example that illustrates just how bad the problem of password cracking is. The following are brute force results using a Quad Xeon 400 Mhz computer (this is just a high-end PC containing 4 processors that are extremely quick) from L0pht’s web site:
•Alpha-numeric characters cracked in 5.5 hours
•Alpha-numeric-some symbols cracked in 45 hours
•Alpha-numeric-all symbols cracked in 480 hours
What is important to point out is that these are brute force results, which means it does not matter what the password is. On a high-end quad processor machine, any password that contains alpha and numeric characters, no matter what the password is, can be cracked in under 6 hours. It is important to note that this is based on a default installation of Microsoft NT, which is what most companies use.
Under these circumstances, the philosophy of having the password change interval less than the time it takes to brute force a password, does not work sufficiently. Even under the assumption that in a best case scenario, users’ passwords contain a wide range of letters, numbers, and all special
“Hackers Beware “ New Riders Publishing |
361 |
characters, then the passwords would still have to be changed every 20 days. This is because based on the above numbers, all passwords can be cracked in 480 hours, which if you divide by 24 hours, comes out to 20 days. If the users at your company are anything like the ones I have worked with, having them change their password every month would be totally unacceptable. The key thing to keep in mind is that a Quad Xeon workstation is a fast and expensive machine, but it is not unfeasible for someone to own one. What is scary is computers are only getting faster. So as computers get faster and cheaper, the time it takes to brute force a password will only decrease. Now might be a good time to think about an alternate way to authenticate users on your network. At the end of this chapter, there is a section, “Protecting Against NT Password Crackers”, which gives you additional details on one-time passwords and biometrics.
Using L0phtcrack
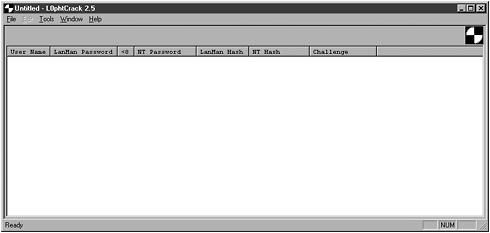
After L0phtcrack is installed, running it is very straightforward. You double-click the icon or select it from the Start menu. After the program starts up, you get the initial screen, as shown in Figure 9.1.
Figure 9.1. Initial User Interface for L0phtcrack.
Let’s briefly run through the interface, and then we can cover the steps you need to perform to run the program. The main window has columns for the different information to be displayed. The first column contains the user name followed by the LANMAN password and NT password. These two columns get filled in after the password has been cracked. The reason there are two columns is that in several cases, the LANMAN password is easier to crack because it breaks it into two 7-character pieces and ignores case sensitivity. The next column indicates whether a password is less than seven characters. Because LANMAN breaks the password into two 7-character pieces, you can easily tell if the second piece is blank, which means the password is 7 characters or less. Remember, because Microsoft takes any password less than 14 characters and pads it with zeros, if your password is 7 characters or less, the second 7 character
“Hackers Beware “ New Riders Publishing |
362 |
string hashed is all zeros. So, any account that has the second half of its LAN Manager hash stored with the hash value of encrypting 7 zeros can be flagged as being less than 8 characters.
The next two columns contain the hashes for both LANMAN and NT, which is what the program uses to crack the password. The main window has four main menus:
•File
•Tools
•Window
•Help
File Menu
Under the file menu are five options:
•Open password file
•Open wordlist file
•Import SAM file
•Save and Save As
•Exit
Open Password File To crack passwords, the encrypted password hashes need to be obtained. One way to do this is to open a file containing the password hashes. This file can either be in the format that programs, such as PWDump create, or it can be a prior saved session of L0phtcrack, in which case the file should end in .lc. One beneficial feature of L0phtcrack is that the entire password does not have to be cracked during one sitting. It can run for 3 hours and then be shutdown after the initial results were saved, and when it is turned on again, it loads the file from the previous session, and L0phtcrack continues where it left off.
PWDump (actually the latest version, PWDump2), is discussed in detail later in this section.
Open Wordlist File If you want to run a dictionary attack, you need to load a dictionary file that contains the words you want to look for. You can use any dictionary that you would like, but the program also comes with a dictionary file called words-english. This dictionary is sufficient as a starting point, but should be customized to an organization’s needs. To customize the dictionary, you could either open up the file and add whatever entries you would like, or you can download additional dictionaries off the Internet and combine them together.
The dictionary that comes with L0phtcrack contains approximately 29,000 words and most English words with several variations. The file is an ASCII text file that contains one word or combination of characters per line. The
“Hackers Beware “ New Riders Publishing |
363 |
file starts off with combination of numbers, then symbols, and then words, in alphabetical order. The file can be customized with any text editor by adding additional lines with the words or adding combinations of characters you want the program to look for. Because the file does not end in an extension, if you double-click it, you get “open with dialog” because Windows does not know what format it is in, and you have to choose a text editor to view the file. The following is a small excerpt from the file:
888888
1234567 !@#$%^& !@#$%^&* 123abc 123go 4runner a
A&M
A&P
a12345 Aaron aaron AAU
As illustrated, the dictionary covers a wide range of words and combinations of characters. Because dictionary attacks are much faster than brute force attacks, if there is a remote possibility that someone is using a word as a password, then include it in your dictionary.
Import SAM File Another way to obtain the password hashes is to import a SAM file and load the hashes from the file. The SAM file is where Microsoft stores the password hashes. It is important to note that the operating system puts a lock on the SAM while the system is running, so it is not possible just to read them from the file while the operating system is active. Microsoft usually makes a copy of the SAM when the system is backed up, and it also puts a copy on the emergency repair disk, if the SAM is small enough to fit. So, if you are creative, there are several places where you can find a copy of it. Another option is to boot from a floppy disk into another operating system, such as DOS or Linux. Because the NT operating system would not be active, the file can be read directly from the system. This is only useful if you have physical access to a machine and it has a floppy disk drive.
In some cases, Microsoft compresses the SAM database file if it is a backup or archive copy of the SAM. In these cases, the file extension is the underscore character, so the file would be SAM. _ . In cases where importing a compressed SAM file is necessary, the SAM is expanded
“Hackers Beware “ New Riders Publishing |
364 |
automatically, if you are running L0phtcrack on NT. However, if you are running L0phtcrack on Windows 95/98, then you have to manually do it. You manually uncompress the file by using the expand sam._sam utility, which comes with NT. So, even if you are running the program on a Windows 95/98 machine, you still need an NT machine to uncompress the SAM.
Save and Save As As we stated earlier, there are several cases where you want to save an uncracked, partially-cracked, or cracked password file for later use or archival. In these cases, you can use the Save and Save As menu to save the data to a file of your choice. The file is saved with an
.lc extension, however it is an ASCII file that can be viewed, edited, modified, or imported into various editors and database programs. The file can be loaded back into the program to either view the results or to continue cracking the file. The file can also be loaded to start a new crack session, which has different options.
The following is a portion of a partially-cracked file:
User name: LanMan Password: NT Password: LanMan Hash: NT Hash ebc:"ERIC":"eric":2EADC590CF4B1727AAD3B435B51404EE:691A324A968 D3285E4FC146A4B7F8D2
8
NTSERVER4A$:"NULL PASSWORD":"NULL PASSWORD":NULL PASSWORD:NULL PASSWORD ericwk:"":"":2F5A2FA739182327D15F2E9F650EFB1B:218A9CF6A43416EE 08B948BF4523404B
This file contains all of the data that L0phtcrack needs to crack the passwords. It basically consists of the user ID and the NT and LANMAN password and hashes. The first line shows you what each field contains, and each field is separated by a colon.
In most cases, it makes more sense to view this file with L0phtcrack than to bring it up in an editor. However, it is ASCII text, so you can create a script to modify the information or process the data in a different format. This could also be useful for importing the data into a database program for further analysis.
For the file previously listed, the first line contains information on an account that has been successfully cracked. The user ID for the account is ebc, next is the LAN manager password, which is ERIC (remember the LAN Manager converts all characters to uppercase), then the NT password, which is eric. If the password was not cracked, such as in the last entry ericwk, then the password fields would contain empty parenthesis. After the two passwords is the LAN Manager hash, which is
“Hackers Beware “ New Riders Publishing |
365 |

followed by the NT hash. Each field is separated by a colon, so it is easy to import into a database, and track the results over time.
Exit This menu option is fairly obvious—it terminates an active crack session and closes the program.
Tools Menu
The tools menu contains the following options:
•Dump passwords from registry
•SMB Packet Capture
•Run Crack
•Stop Crack
•Options
The tools menu is where you spend most of your time when working with L0phtcrack. This is where you can dump the passwords, sniff them off the network, configure the program, and start and stop the program.
Dump Passwords from Registry This menu option opens a dialog box, which allows the user to enter either the IP address or the Net BIOS name of a computer. The specific computer is then queried by remote registry calls to extract the password hashes located in the SAM database of the registry. To perform this action, administrator privileges are required. Figure 9.2 shows the screen that appears to dump the passwords from the registry.
Figure 9.2. Dump Passwords from Registry Dialog Box.
In most cases, the computer information that you enter should refer to the primary domain control (PDC) because this is where all the accounts for the domain are located. In the dialog box, you either enter the Net BIOS computer name or the IP address of the machine. Because this feature pulls password hashes over the network and requires network bandwidth, it is recommended that this be performed early in the morning
“Hackers Beware “ New Riders Publishing |
366 |
or in the evening, especially if there are large numbers of accounts on the system. If you run the program during the day when there is a lot of network traffic, it could take a while for the results to come back.
I was running L0phtcrack once during the day, when there was a lot of traffic, and after about 10 minutes there was still no response. While using NT, I hit Ctrl-Alt-Del to look at the task and it stated L0phtcrack has stopped responding. I let the program sit for another hour, and the results finally came back. The key point is that if there are a lot of things running on your network, it could take a while to get the results. Another factor to consider is that L0phtcrack has a limit that it can only extract and open a maximum of 65,000 users. Therefore, this program will not work sufficiently if you have an extremely large number of users.
SMB Packet Capture Another way to capture password hashes is to sniff them from the network as people log on. If someone can compromise a machine that is connected to the network, and they can sniff traffic between 8:00-10:00 am, they can acquire a large number of passwords because that is when most people logon to the system. A key thing to remember is that this only works in a hub environment, thus, another reason to upgrade your network to a switched environment. For a computer to sniff traffic off of a network, the network interface card (NIC) must be put in promiscuous mode. This feature, included with L0phtcrack, puts the network card in promiscuous mode, which means it can see all network traffic. In a typical Ethernet, network packets are sent to all machines on the local segment, and if it is addressed to that machine, it accepts it, and if it is not addressed to that machine, it drops it. In promiscuous mode, the card accepts all traffic whether it is addressed to the local machine or not. Reminder, this only works if you are using a hub environment. In a switched environment, traffic is sent only to the machine it is destined for, and it is not received by all systems on the network. Therefore, if you are running this program in a switched environment, you only see the logons occurring at the local machine.
SMB packet capture launches the window shown in Figure 9.3, which captures password hashes as people logon to the system. As passwords are pulled off the network, they appear in the dialog box in real time.
Figure 9.3. SMB Packet Capture output window.
“Hackers Beware “ New Riders Publishing |
367 |
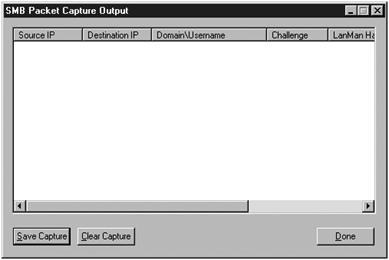
The packet capture feature scans all traffic looking for an authentication session. When it finds one, it displays the following information in the window: username, IP information, and the password hashes. As soon as the window is opened, the packet capture session starts, and it terminates when you close the window. To save a session, you click the save capture button, and to clear the current passwords in the window, you hit the clear capture button.
It is important to point out that this window only captures password hashes; it does not actually crack the passwords. After the password hashes have been captured, they should be saved into a file with an .lc extension. The passwords can then be pulled into L0phtcrack and cracked to obtain the plain text passwords. I would also recommend running the password capture on a Windows 95/98 machine. When I tried running it on an NT machine, it only periodically captured all the password hashes, and sometimes it missed several sessions.
Also, if you have a previous version of L0phtcrack installed, you must remove the DNIS packet driver from the protocols tab in the network section of the Control Panel for the system to work properly. It is important to note that if you have other low-level packet drivers installed, it could cause problems with the Packet Capture. This is an important note: To use the packet capture feature, you have to go under Control Panel, click network, and load the low-level driver that L0phtcrack needs to sniff the passwords.
To give you an example, I was using a commercial vulnerability scanner on one of my systems, which required a low-level packet driver to be installed. I then installed L0phtcrack on the system and could not get it to sniff packets off of the network. Only after I went in and removed the packet driver for the vulnerability scanner and rebooted, was I able to get L0phtcrack to successfully sniff passwords off of the network. So, it is very
“Hackers Beware “ New Riders Publishing |
368 |
important that you know what other services and protocols are loaded on your system.
Run Crack This option is fairly self-explanatory; it starts the program that cracks passwords. For it to work properly, you must have password hashes loaded and the system configured correctly. If you have never run this program before, I highly recommend watching the screen, and scrolling up and down, when the cracking starts. You will be amazed by how many passwords it cracks and how quickly they flash up on the screen.
Stop Crack This option stops the current cracking session. Because the system is updated in real time, any passwords that were cracked can be saved. Another beneficial feature is that the file can be saved and restarted at any time. When you restart the cracking on a partiallycracked file, it does not start from the beginning, it continues where it left off.
Options The Options dialog box is where you configure the different types of password attacks and the features for each type. There are three main sections to this dialog box, each corresponding to one of three types of attacks: dictionary, brute force, and the dictionary/brute force hybrid.
The first section is on the dictionary attack. In this section, you can pick whether you want the program to do an attack on the LANMAN hashes, the NTLM hashes, just one, or both. Unless you know for sure that LANMAN hashes are disabled on your system, I recommend keeping both selected.
The second section is on the brute force attack. It shows you how to turn brute force attacking on and off and how to select the character set you want to use to brute force the passwords. Remember, the larger the character set is, the longer it takes to run. I usually start off with just letters, or letters and numbers, and then whatever passwords it did not find, I add additional symbols and rerun crack. Another feature is that you can enter a custom character set, which is useful for cracking foreign language passwords.
The third section is on the dictionary/brute force hybrid attack. This combines a dictionary attack with a partial brute force attack by combining dictionary words with other characters. In other words, a password of password57 would not be found with a dictionary attack, but it would be found faster with a hybrid attack than with a brute force attack. The hybrid attack enables you to pick the number of numbers and symbols to append to each word. One word of caution, when you go above three characters, you start loosing the benefit of a hybrid attack because it takes longer to run, without the guarantee of finding every
“Hackers Beware “ New Riders Publishing |
369 |
