
Internet.Security
.pdf110 INTERNET SECURITY
Example 3.22 Compute (57) • (13) = (fe)
(57) = (01010111)
(57) • (02) = xtime(57) = (10101110) = (ae)
(57) • (04) = xtime(ae) = (01011100) (00011011)
= (01000111) = (47)
(57) • (08) = xtime(47) = (10001110) = (8e)
(57) • (10) = xtime(8e) = (00011100) (00011011) = (07)
Thus, it follows that
|
|
|
L |
|
(57) • (13) = (57) • {(01) (02) (10)} |
F |
|||
= (57) (57) • (02) (57) • (10) |
|
Y |
||
= (57) (ae) (07) |
A |
|
|
|
|
|
|
||
= (01010111) (10101110) (00000111) |
||||
E |
|
|
|
|
= (11111110) = (fe) |
M |
|
||
Polynomials with finiteTfield elements in GF(28)
A polynomial a(x) with byte-coefficient in GF(28) can be expressed in word form as: a(x) = a3x3 + a2x2 + a1x + a0 a = (a0, a1, a2, a3)
To illustrate the addition and multiplication operations, let b(x) = b3x3 + b2x2 + b1x + b0 b = (b0, b1, b2, b3)
be a second polynomial.
Addition is performed by adding the finite field coefficients of like powers of x such that
a(x) + b(x) = (a3 b3)x3 + (a2 b2)x2 + (a1 b1)x + (a0 b0)
This addition corresponds to an XOR operation between the corresponding bytes in each of the words. Multiplication is achieved as shown below:
The polynomial product c(x) = a(x) • b(x) is expanded and like powers are collected to give
c(x) = a(x) • b(x) = c6x6 + c5x5 + c4x4 + c3x3 + c2x2 + c1x + c0
= (c6, c5, c4, c3, c2, c1, c0)
Team-Fly®
|
SYMMETRIC BLOCK CIPHERS |
111 |
||
where |
|
|
|
|
c0 = a0b0 |
c4 = a3b1 a2b2 a1b3 |
|
||
c1 = a1b0 a0b1 |
c5 = a3b2 a2b3 |
|
||
c2 = a2b0 a1b1 a0b2 |
c6 = a3b3 |
|
||
c3 = a3b0 a2b1 a1b2 a0b3 |
|
|
|
|
The next step is to reduce c(x) mod (x4 |
+ |
1) for the AES algorithm, so that xi |
mod |
|
(x4 + 1) = ximod4. |
|
|
|
|
The modular product, a(x) b(x), of two four-term polynomials a(x) and b(x), is given by
d(x) = a(x) b(x) = d3x3 + d2x2 + d1x + d0
where
d0 = a0b0 a3b1 a2b2 a1b3 d1 = a1b0 a0b1 a3b2 a2b3 d2 = a2b0 a1b1 a0b2 a3b3 d3 = a3b0 a2b1 a1b2 a0b3
Thus, d(x) in matrix form is written as:
d1 |
a1a0a3a2 |
b1 |
||||||||
d0 |
|
a0a3a2a1 |
b0 |
|
||||||
d2 |
|
= a2a1a0a3 |
b2 |
|
||||||
d |
3 |
|
a |
a |
a |
a |
0 |
b |
3 |
|
|
|
3 |
2 |
1 |
|
|
|
|||
The AES algorithm also defines the inverse polynomials as:
a(x) = (03)x3 + (01)x2 + (01)x1 + (02)
a−1(x) = (0b)x3 + (0d)x2 + (09)x1 + (0e)
3.5.3 AES Algorithm Specification
For the AES algorithm, Nb denotes the number of 32-bit words with respect to the 128-bit block of the input, output, or state (128 = N b × 32, from which N b = 4).
Nk represents the number of 32-bit words with respect to the cipher-key length of 128, 192 or 256 bits:
128 = N k × 32, |
N k = 4 |
196 = N k × 32, |
N k = 6 |
256 = N k × 32, |
N k = 8 |
The number of rounds are 10, 12 and 14, respectively.
112 INTERNET SECURITY
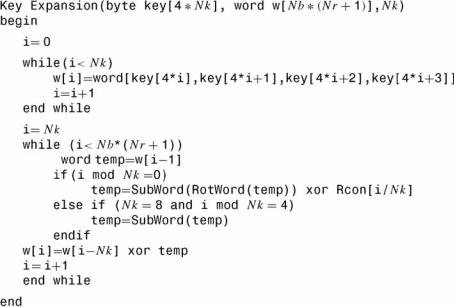
Key expansion
The AES algorithm takes the cipher key K and performs a key expansion routine to generate a key schedule. The key expansion generates a total of Nb(N r + 1) words: an initial set of Nb words for Nr = 0, and 2Nb for Nr = 1, 3Nb for Nr = 2, . . . , 11Nb for Nr = 10. Thus, the resulting key schedule consists of a linear array of four-byte words
[wi ], 0 ≤ i < N b(N r + 1).
RotWord() takes a four-byte input word [a0, a1, a2, a3] and performs a cyclic permutation such as [a1, a2, a3, a0].
SubWord() takes a four-byte input word and applies the S-box (Figure 3.15) to each of the four bytes to produce an output word.
Rcon[i] represents the round constant word array and contains the values given by [xi−1, {00}, {00}, {00}] with xi−1 starting i at 1.
Example 3.23 Compute the round constant words Rcon [i]:
Rcon[i] = [xi−1, {00}, {00}, {00}]
Rcon[1] = [x0, {00}, {00}, {00}] = [{01}, {00}, {00}, {00}] = 01000000
|
|
|
|
|
|
|
|
|
|
y |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
0 |
1 |
2 |
3 |
4 |
5 |
6 |
7 |
|
8 |
9 |
a |
b |
c |
d |
e |
f |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
0 |
63 |
7c |
77 |
7b |
f2 |
6b |
6f |
c5 |
|
30 |
01 |
67 |
2b |
fe |
d7 |
ab |
76 |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
1 |
ca |
82 |
c9 |
7d |
fa |
59 |
47 |
f0 |
|
ad |
d4 |
a2 |
af |
9c |
a4 |
72 |
c0 |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
2 |
b7 |
fd |
93 |
26 |
36 |
3f |
f7 |
cc |
|
34 |
a5 |
e5 |
f1 |
71 |
d8 |
31 |
15 |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
3 |
04 |
c7 |
23 |
c3 |
18 |
96 |
05 |
9a |
|
07 |
12 |
80 |
e2 |
eb |
27 |
b2 |
75 |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
4 |
09 |
83 |
2c |
1a |
1b |
6e |
5a |
a0 |
|
52 |
3b |
d6 |
b3 |
29 |
e3 |
2f |
84 |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
5 |
53 |
d1 |
00 |
ed |
20 |
fc |
b1 |
5b |
|
6a |
cb |
be |
39 |
4a |
4c |
58 |
cf |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
6 |
d0 |
ef |
aa |
fb |
43 |
4d |
33 |
85 |
|
45 |
f9 |
02 |
7f |
50 |
3c |
9f |
a8 |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
x |
7 |
51 |
a3 |
40 |
8f |
92 |
9d |
38 |
f5 |
|
bc |
b6 |
da |
21 |
10 |
ff |
f3 |
d2 |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
8 |
cd |
0c |
13 |
ec |
5f |
97 |
44 |
17 |
|
c4 |
a7 |
7e |
3d |
64 |
5d |
19 |
73 |
|
|
|
|||||||||||||||||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
9 |
60 |
81 |
4f |
dc |
22 |
2a |
90 |
88 |
|
46 |
ee |
b8 |
14 |
de |
5e |
0b |
db |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
a |
e0 |
32 |
3a |
0a |
49 |
06 |
24 |
5c |
|
c2 |
d3 |
ac |
62 |
91 |
95 |
e4 |
79 |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
b |
e7 |
c8 |
37 |
6d |
8d |
d5 |
4e |
a9 |
|
6c |
56 |
f4 |
ea |
65 |
7a |
ae |
08 |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
c |
ba |
78 |
25 |
2e |
1c |
a6 |
b4 |
c6 |
|
e8 |
dd |
74 |
1f |
4b |
db |
8b |
8a |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
d |
70 |
3e |
b5 |
66 |
48 |
03 |
f6 |
0e |
|
61 |
35 |
57 |
b9 |
86 |
c1 |
1d |
9e |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
e |
e1 |
f8 |
98 |
11 |
69 |
d9 |
8e |
94 |
|
9b |
1e |
87 |
e9 |
ce |
55 |
28 |
df |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
f |
8c |
a1 |
89 |
0d |
bf |
e6 |
42 |
68 |
|
41 |
99 |
2d |
0f |
b0 |
54 |
bb |
16 |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Figure 3.15 AES S-box (FIPS Publication, 2001).
|
SYMMETRIC BLOCK CIPHERS |
113 |
Rcon[2] = [x1 |
, {00}, {00}, {00}] = 02000000 |
|
Rcon[3] = [x2 |
, {00}, {00}, {00}] = 04000000 |
|
Rcon[4] = [x3 |
, {00}, {00}, {00}] = 08000000 |
|
Rcon[5] = [x4 |
, {00}, {00}, {00}] = 10000000 |
|
Rcon[6] = [x5 |
, {00}, {00}, {00}] = 20000000 |
|
Rcon[7] = [x6 |
, {00}, {00}, {00}] = 40000000 |
|
Rcon[8] = [x7 |
, {00}, {00}, {00}] = 80000000 |
|
Rcon[9] = [x8 |
, {00}, {00}, {00}] = [x7 • x, {00}, {00}, {00}] = 1b000000 |
|
x7 • x = xtime(x7) = xtime(80) = {leftshift(80)} {1b} = 1b |
|
|
Rcon[10] = [x9 |
, {00}, {00}, {00}] = [x8 • x, {00}, {00}, {00}] = 36000000 |
|
Rcon[11] = [x10, {00}, {00}, {00}] = [x9 • x, {00}, {00}, {00}] = 6c000000 |
|
|
Rcon[12] = [x11, {00}, {00}, {00}] = [x10 • x, {00}, {00}, {00}] = d8000000 |
|
|
Rcon[13] = [x12, {00}, {00}, {00}] = [x11 • x, {00}, {00}, {00}] = ab000000 x11 • x = xtime(x11) = xtime(d8) = {leftshift(d8)} {1b} = ab
Rcon[i] is a useful component for the round constant ward array in order to compute the key expansion routine.
The input key expansion into the key schedule proceeds as shown in Figure 3.16.
Example 3.24 Suppose the cipher key K is given as |
||
K = 36 8a c0 f4 ed cf 76 a6 08 a3 b6 78 31 31 |
27 |
6e |
The first four words of K for N k = 4 results |
in |
w[0] = 368ac0f4, w[1] = edcf76a6, |
w[2] = 08a3b678, w[3] = 3131276e. |
|
|
Computation of w[4] for i = 4 is as follows:
Temp = w[3] = 3131276e
A cyclic permutation of w[3] by one byte produces
RotWord(w[3]) = 31276e31
Taking each byte of RotWord(w[3]) at a time and applying to the S-box yields SubWord(31276e31) = c7cc9fc7
Compute a round constant Rcon[i/N k]:
Rcon[4/4] = Rcon[1] = 01000000
XORing SubWord() with Rcon[1] yields
114 |
INTERNET SECURITY |
|
|
|
|
|
|
|
Figure 3.16 Pseudocode for key expansion (FIPS Publication, 2001).
SubWord() Rcon[1] = c6cc9fc7
w[i − N k] = w[0] = 368ac0f4
Finally, w[4] is computed as:
w[4] = c6cc9fc7 368ac0f4 = f0465f33.
Continuing in this fashion, the remaining w[i], 4 ≤ i ≤ 43, can be computed as shown in Table 3.16.
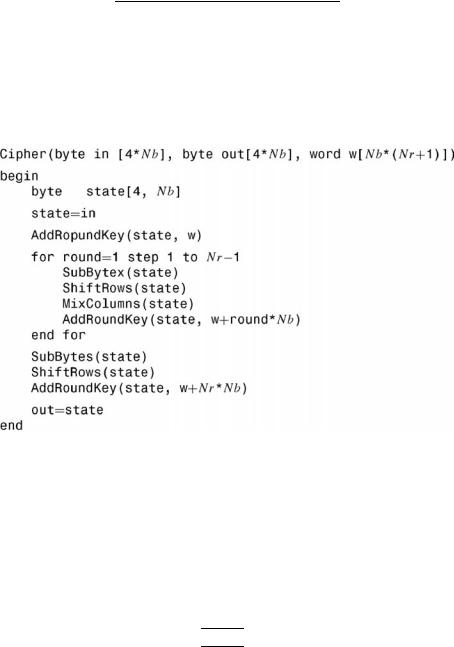
Cipher
The 128-bit cipher input is fed in a column-by-column manner, comprising each column with a four-byte word. In other words, the input is copied to the state array as shown in Table 3.17.
The cipher is described in the pseudocode in Figure 3.17.
Individual transformations for the pseudocode computation consist of SubBytes(), ShiftRows(), MixColumns() and AddRoundKey(). These transformations play a role in processing the state and are briefly described below.
|
|
|
SYMMETRIC BLOCK CIPHERS |
|
115 |
|
Table 3.16 AES key expansion |
|
|
|
|
||
|
|
|
|
|
|
|
i |
Temp. |
After |
After |
Rcon[i/Nk ] |
After XOR |
w[i] = temp |
|
|
RotWord |
SubWord |
|
with Rcon |
w[i − Nk] |
4 |
3131276e |
31276e31 |
c7cc9fc7 |
01000000 |
c6cc9fc7 |
f0465f33 |
5 |
f0465f33 |
|
|
|
|
1d892995 |
6 |
1d892995 |
|
|
|
|
152a9fed |
7 |
152a9fed |
|
|
|
|
241bb883 |
8 |
241bb883 |
1bb88324 |
af6cec36 |
02000000 |
ad6cec36 |
5d2ab305 |
9 |
5d2ab305 |
|
|
|
|
40a39a90 |
10 |
40a39a90 |
|
|
|
|
5589057d |
11 |
5589057d |
|
|
|
|
7192bdfe |
12 |
7192bdfe |
92bdfe71 |
4f7abba3 |
04000000 |
4b7abba3 |
165008a6 |
13 |
165008a6 |
|
|
|
|
56f39236 |
14 |
56f39236 |
|
|
|
|
037a974b |
15 |
037a974b |
|
|
|
|
72e82ab5 |
16 |
72e82ab5 |
e82ab572 |
9be5d540 |
08000000 |
93e5d540 |
85b5dde6 |
17 |
85b5dde6 |
|
|
|
|
d3464fd0 |
18 |
d3464fd0 |
|
|
|
|
d03cd89b |
19 |
d03cd89b |
|
|
|
|
a2d4f22e |
20 |
a2d4f22e |
d4f22ea2 |
4889313a |
10000000 |
5889313a |
dd3cecdc |
21 |
dd3cecdc |
|
|
|
|
0e7aa30c |
22 |
0e7aa30c |
|
|
|
|
de467b97 |
23 |
de467b97 |
|
|
|
|
7c9289b9 |
24 |
7c9289b9 |
9289b97c |
4fa75610 |
20000000 |
6fa75610 |
b29bbacc |
25 |
b29bbacc |
|
|
|
|
bce119c0 |
26 |
bce119c0 |
|
|
|
|
62a76257 |
27 |
62a76257 |
|
|
|
|
1e35ebee |
28 |
1e35ebee |
35ebee1e |
96e92872 |
40000000 |
d6e92872 |
647292be |
29 |
647292be |
|
|
|
|
d8938b7e |
30 |
d8938b7e |
|
|
|
|
ba34e929 |
31 |
ba34e929 |
|
|
|
|
a40102c7 |
32 |
a40102c7 |
0102c7a4 |
7c77c649 |
80000000 |
fc77c649 |
980554f7 |
33 |
980554f7 |
|
|
|
|
4096df89 |
34 |
4096df89 |
|
|
|
|
faa236a0 |
35 |
faa236a0 |
|
|
|
|
5ea33467 |
36 |
5ea33467 |
a334675e |
0a188558 |
1b000000 |
11188558 |
891dd1af |
37 |
891dd1af |
|
|
|
|
c98b0e26 |
38 |
c98b0e26 |
|
|
|
|
33293886 |
39 |
33293886 |
|
|
|
|
6d8a0ce1 |
40 |
6d8a0ce1 |
8a0ce16d |
7efef83c |
36000000 |
48fef83c |
c1e32993 |
41 |
c1e32993 |
|
|
|
|
086827b5 |
42 |
086827b5 |
|
|
|
|
3b411f33 |
43 |
3b411f33 |
|
|
|
|
56cb13d2 |
|
|
|
|
|
|
|
116 INTERNET SECURITY
Table 3.17 A 16-byte cipher input array
|
Row No. |
Mapping of input block into |
|
|||
|
|
|
column-by-column array |
|
||
|
|
|
|
|
|
|
|
0 |
a0 |
a4 |
a8 |
a12 |
|
|
1 |
a1 |
a5 |
a9 |
a13 |
|
|
2 |
a2 |
a6 |
a10 |
a14 |
|
|
3 |
a3 |
a7 |
a11 |
a15 |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Figure 3.17 Pseudocode for the cipher (FIPS Publication, 2001).
SubBytes() Transformation
The SubBytes() transformation is a nonlinear byte substitution that operates independently on each byte of the state using a S-box (see Figure 3.18).
For example, if s2,1 = {8f}, then the substitution value is determined by the intersection
of the row with index 8 and the column with index f in Figure 3.15. The resulting s ,
2 1
would be a value of {73}.
Sr,c 
 S-box
S-box 
 S′r,c
S′r,c
0 ≤ r ≤ 3, 0 ≤ c ≤ Nb − 1
Figure 3.18 SubBytes() transformation by the S-box.
SYMMETRIC BLOCK CIPHERS |
117 |
ShiftRows() Transformation
In the ShiftRows(), the first row (row 0) is not shifted and the remaining rows proceed as follows:
s |
|
= |
s |
|
, for 0 < r < 4 and 0 |
≤ |
c < N b |
|
r,c |
|
r,(c+shift(r,Nb)) mod Nb |
|
|
where the shift value shift (r, N b) = shift (r, 4) depends on the row number r as follows:
shift (1, 4) = 1; shift (2, 4) = 2; shift (3, 4) = 3;
This has the effect of shifting the leftmost bytes around into the rightmost positions over different numbers of bytes in a given row.
MixColumns() Transformation
The MixColumns() transformation operates on the state column-by-column, treating each column as a four-term polynomial over GF(28) and multiplied modulo x4 + 1 with a fixed polynomial a(x) as:
s (x) = a(x) s(x)
where a(x) = {03}x3 + {01}x2 + {01}x + {02}, s(x) is the input polynomial and s (x) is the corresponding polynomial after the MixColumns() transformation.
The matrix multiplication of s (x) is
s |
,c |
|
|
01 |
02 |
03 |
01 |
s1,c |
|
s1 |
|||||||||
0,c |
|
|
02 |
03 |
01 |
01 |
s0,c |
|
|
s2 |
,c |
|
= |
01 |
01 |
02 |
03 |
s2,c |
for 0 ≤ c < N b |
|
|
|
|
03 |
01 |
01 |
02 |
s3,c |
|
s3,c |
|
|
|
|
|
|
|
|
|
The four bytes in a column after the matrix multiplication are
s ,c = ({02} • s0,c) ({03} • s1,c) s2,c s3,c
0
s ,c = s0,c ({02} • s1,c) ({03} • s2,c) s3,c
1
s ,c = s0,c s1,c ({02} • s2,c) ({03} • s3,c)
2
s ,c = ({03} • s0,c) s1,c s2,c ({02} • s3,c)
3
AddRoundKey() Transformation
In AddRoundKey() transformation, a round key is added to the state by a simple bitwise XOR operation. Each round key consists of Nb words from the key schedule. These Nb words are added into the columns of the state such that
[s |
|
, s |
|
, s |
|
, s |
|
] |
= |
[s0,c, s1,c, s2,c, s3,c] |
|
[wround Nb |
+ |
c]for 0 |
≤ |
c < N b |
|
0,c |
|
1,c |
|
2,c |
|
3,c |
|
|
|
|
|
where [wi ] are the key schedule words, and round is a value in the range 0 ≤ round ≤ N r. The initial round key addition occurs when round = 0, prior to the first application of the round function. The application of the AddRoundKey() transformation to the Nr rounds of the cipher occurs when 1 ≤ round ≤ N r.

118 |
INTERNET SECURITY |
Example 3.25 Assume that the input block and a cipher key whose length of 16 bytes each are given as:
Plaintext = a3 c5 08 08 78 a4 ff d3 00 ff 36 36 28 5f 01 02
Cipherkey = 36 8a c0 f4 ed cf 76 a6 08 a3 b6 78 31 31 27 6e
Using the algorithm for the pseudocode computation described in Figure 3.17, the intermediate values in the state array are given in the following table. The round key values w[i] are taken from Example 3.24.
Cipher (Encrypt)
r Start of round |
|
After |
|
|
After |
|
|
After |
|
After XOR |
|||||||||||
|
|
|
|
|
|
SubByte |
|
|
ShiftRows |
|
MixColumns |
|
with w[] |
|
|||||||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
a3 |
78 |
00 |
28 |
|
|
|
|
|
|
|
|
|
|
|
|
95 |
95 |
08 |
19 |
|
0 |
c5 |
a4 |
ff |
5f |
|
|
|
|
|
|
|
|
|
|
|
|
4f |
6b |
5c |
6e |
|
08 |
ff |
36 |
01 |
|
|
|
|
|
|
|
|
|
|
|
|
c8 |
89 |
80 |
26 |
||
|
|
|
|
|
|
|
|
|
|
|
|
|
|||||||||
|
08 |
d3 |
36 |
02 |
|
|
|
|
|
|
|
|
|
|
|
|
fc |
75 |
4e |
6c |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
95 |
95 |
08 |
19 |
2a |
2a |
30 |
d4 |
2a |
2a |
30 |
d4 |
48 |
cd |
af |
ac |
b8 |
d0 |
ba |
88 |
|
1 |
4f |
6b |
5c |
6e |
84 |
7f |
4a |
9f |
7f |
4a |
9f |
84 |
c8 |
0c |
ab |
1a |
8e |
85 |
81 |
01 |
|
c8 |
89 |
80 |
26 |
e8 |
a7 |
cd |
f7 |
cd |
f7 |
e8 |
a7 |
24 |
5e |
d8 |
74 |
7b |
77 |
47 |
cc |
||
|
|||||||||||||||||||||
|
fc |
75 |
4e |
6c |
b0 |
9d |
2f |
50 |
50 |
b0 |
9d |
2f |
6c |
b8 |
06 |
1a |
5f |
2d |
eb |
99 |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
b8 |
d0 |
ba |
88 |
6c |
70 |
f4 |
c4 |
6c |
70 |
f4 |
c4 |
34 |
70 |
8e |
a4 |
69 |
30 |
db |
d5 |
|
2 |
8e |
85 |
81 |
01 |
19 |
97 |
0c |
7c |
97 |
0c |
7c |
19 |
4c |
7a |
b7 |
1b |
66 |
d9 |
3e |
89 |
|
7b |
77 |
47 |
cc |
21 |
f5 |
a0 |
4b |
a0 |
4b |
21 |
f5 |
89 |
a0 |
b9 |
0c |
3a |
3a |
bc |
b1 |
||
|
|||||||||||||||||||||
|
5f |
2d |
eb |
99 |
cf |
d8 |
e9 |
ee |
ee |
cf |
d8 |
e9 |
44 |
52 |
f1 |
72 |
41 |
c2 |
8c |
8c |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
69 |
30 |
db |
d5 |
f9 |
04 |
b9 |
03 |
f9 |
04 |
b9 |
03 |
b7 |
8e |
3e |
b7 |
a1 |
d8 |
3d |
c5 |
|
3 |
66 |
d9 |
3e |
89 |
33 |
35 |
b2 |
a7 |
35 |
b2 |
a7 |
33 |
58 |
bb |
52 |
9a |
08 |
48 |
28 |
72 |
|
3a |
3a |
bc |
b1 |
80 |
80 |
65 |
c8 |
65 |
c8 |
80 |
80 |
aa |
a3 |
6a |
87 |
a2 |
31 |
fd |
ad |
||
|
|||||||||||||||||||||
|
41 |
c2 |
8c |
8c |
83 |
25 |
64 |
64 |
64 |
83 |
25 |
64 |
88 |
6b |
bd |
7e |
2e |
5d |
f6 |
cb |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
a1 |
d8 |
3d |
c5 |
32 |
61 |
27 |
a6 |
32 |
61 |
27 |
a6 |
d9 |
3a |
f8 |
82 |
5c |
e9 |
28 |
20 |
|
4 |
08 |
48 |
28 |
72 |
30 |
52 |
34 |
40 |
52 |
34 |
40 |
30 |
75 |
9c |
a5 |
d6 |
c0 |
da |
99 |
02 |
|
a2 |
31 |
fd |
ad |
3a |
c7 |
54 |
95 |
54 |
95 |
3a |
c7 |
e9 |
37 |
c7 |
c5 |
34 |
78 |
1f |
37 |
||
|
|||||||||||||||||||||
|
2e |
5d |
f6 |
cb |
31 |
4c |
42 |
1f |
1f |
31 |
4c |
42 |
6e |
60 |
8b |
82 |
88 |
b0 |
10 |
ac |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
5c |
e9 |
28 |
20 |
4a |
1e |
34 |
b7 |
4a |
1e |
34 |
b7 |
3c |
4b |
0e |
d6 |
e1 |
45 |
d0 |
aa |
|
5 |
c0 |
da |
99 |
02 |
ba |
57 |
ee |
77 |
57 |
ee |
77 |
ba |
2e |
a8 |
15 |
cd |
12 |
d2 |
53 |
5f |
|
34 |
78 |
1f |
37 |
18 |
bc |
c0 |
9a |
c0 |
9a |
18 |
bc |
2e |
88 |
41 |
2b |
c2 |
2b |
3a |
a2 |
||
|
|||||||||||||||||||||
|
88 |
b0 |
10 |
ac |
c4 |
e7 |
ca |
91 |
91 |
c4 |
e7 |
ca |
70 |
c5 |
e6 |
4b |
ac |
c9 |
71 |
f2 |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
e1 |
45 |
d0 |
aa |
f8 |
6e |
70 |
ac |
f8 |
6e |
70 |
ac |
26 |
5b |
52 |
51 |
94 |
e7 |
30 |
4f |
|
6 |
12 |
d2 |
53 |
5f |
c9 |
b5 |
ed |
cf |
b5 |
ed |
cf |
c9 |
9b |
70 |
47 |
8e |
00 |
91 |
e0 |
bb |
|
c2 |
2b |
3a |
a2 |
25 |
f1 |
80 |
3a |
80 |
3a |
25 |
f1 |
d6 |
5f |
89 |
62 |
6c |
46 |
eb |
89 |
||
|
|||||||||||||||||||||
|
ac |
c9 |
71 |
f2 |
91 |
dd |
a3 |
89 |
89 |
91 |
dd |
a3 |
2f |
5c |
db |
8a |
e3 |
9c |
8c |
64 |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|

SYMMETRIC BLOCK CIPHERS |
119 |
r Start of round |
|
After |
|
|
After |
|
|
After |
|
After XOR |
|||||||||||
|
|
|
|
|
|
SubByte |
|
|
ShiftRows |
|
MixColumns |
|
with w[] |
|
|||||||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
94 |
e7 |
30 |
4f |
22 |
94 |
04 |
84 |
22 |
94 |
04 |
84 |
76 |
bd |
a3 |
88 |
12 |
65 |
19 |
2c |
|
7 |
00 |
91 |
e0 |
bb |
63 |
81 |
e1 |
ea |
81 |
e1 |
ea |
63 |
58 |
ae |
e5 |
c8 |
2a |
3d |
d1 |
c9 |
|
6c |
46 |
eb |
89 |
50 |
5a |
e9 |
a7 |
e9 |
a7 |
50 |
5a |
af |
13 |
37 |
ff |
3d |
98 |
de |
fd |
||
|
|||||||||||||||||||||
|
e3 |
9c |
8c |
64 |
11 |
de |
64 |
43 |
43 |
11 |
de |
64 |
88 |
c3 |
11 |
66 |
36 |
bd |
38 |
a1 |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
12 |
65 |
19 |
2c |
c9 |
4d |
d4 |
71 |
c9 |
4d |
d4 |
71 |
cf |
89 |
92 |
97 |
57 |
c9 |
68 |
c9 |
|
8 |
2a |
3d |
d1 |
c9 |
e5 |
27 |
3e |
dd |
27 |
3e |
dd |
e5 |
92 |
c8 |
66 |
6d |
97 |
5e |
c4 |
ce |
|
3d |
98 |
de |
fd |
27 |
46 |
1d |
54 |
1d |
54 |
27 |
46 |
82 |
d4 |
c9 |
11 |
d6 |
0b |
ff |
25 |
||
|
|||||||||||||||||||||
|
36 |
bd |
38 |
a1 |
05 |
7a |
07 |
32 |
32 |
05 |
7a |
07 |
1e |
b7 |
69 |
3e |
e9 |
3e |
c9 |
59 |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
57 |
c9 |
68 |
c9 |
5b |
dd |
45 |
dd |
5b |
dd |
45 |
dd |
83 |
a4 |
48 |
d4 |
0a |
6d |
7b |
b9 |
|
9 |
97 |
5e |
c4 |
ce |
88 |
58 |
1c |
8b |
58 |
1c |
8b |
88 |
1a |
ba |
fb |
76 |
07 |
31 |
d2 |
fc |
|
d6 |
0b |
ff |
25 |
f6 |
2b |
16 |
3f |
16 |
3f |
f6 |
2b |
69 |
9d |
f4 |
7f |
b8 |
93 |
cc |
73 |
||
|
|||||||||||||||||||||
|
e9 |
3e |
c9 |
59 |
1e |
b2 |
dd |
cb |
cb |
1e |
b2 |
dd |
2e |
63 |
cd |
7e |
81 |
45 |
4b |
9f |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
0a |
6d |
7b |
b9 |
67 |
3c |
21 |
56 |
67 |
3c |
21 |
56 |
|
|
|
|
a6 |
34 |
1a |
00 |
|
10 |
07 |
31 |
d2 |
fc |
c5 |
c7 |
b5 |
b0 |
c7 |
b5 |
b0 |
c5 |
|
|
|
|
24 |
dd |
f1 |
0e |
|
b8 |
93 |
cc |
73 |
6c |
dc |
4b |
8f |
4b |
8f |
6c |
dc |
|
|
|
|
62 |
a8 |
73 |
cf |
||
|
|
|
|
|
|||||||||||||||||
|
81 |
45 |
4b |
9f |
0c |
6e |
b3 |
db |
db |
0c |
6e |
b3 |
|
|
|
|
48 |
b9 |
5d |
61 |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Inverse cipher
The Cipher transformation can be implemented in reverse order to produce a Inverse Cipher for the AES algorithm. The individual transformations used in the Inverse Cipher are InvShiftRows(), InvSubBytes(), InvMixColumns() and AddRoundKey(). These inverse transformations process the state as described in the following.
InvShiftRows() Transformation
InvShiftRows() is the inverse of the ShiftRows() transformation. The first row (Row 0) is not shifted. The bytes in the last three rows (Row 1, Row 2, Row 3) are cyclically shifted over different numbers of bytes as follows:
shift (r, N b): shift values, where ris a row number and N b = 4.
shift (1, 4) = 1, shift (2, 4) = 2, shift (3, 4) = 3, respectively.
Specifically, the InvShiftRows() transformation proceeds as:
s |
|
= |
s |
r,c |
, for 0 < r < 4 and 0 |
≤ |
c < N b |
|
r,(c+shift(r,Nb))modNb |
|
|
|
InvSubBytes() Transformation
InvSubBytes() is the inverse of the byte substitution transformation, in which the inverse S-box is applied to each byte of the state. The inverse S-box used in the InvSubBytes() transformation is presented in Figure 3.19.
