
Internet.Security
.pdf210 |
INTERNET SECURITY |
scheme. The X.509 strong authentication is an example of an authentication scheme that utilises digital signatures.
Careful selection and appropriate protection of the prime numbers p and q, of the primitive element g of p and of the private and public components x and y of each key are at the core of security in digital signatures. Therefore, whoever generates these keys and their parameters is a vital concern for security. PCAs are responsible for defining who should generate these numbers.
When generating the key for itself and its CA, each PCA needs to specify the acceptable algorithms used to generate the prime numbers and parameters. For example, a larger p means more security, but requires more computation in the signing and verification steps. Thus, the size of p allows a trade-off between security and performance. Each PCA must
specify the range of p for itself, its CAs and its end users. The range of p is largest for the PCA and smallest for the end user.
Y L One-way hash functions and digital signatureFalgorithms are used to sign certificates
and CRLs. They are used to identify OIDs for public keys contained in a certificate. SHA-1 is the preferred one-way functionMfor use in the Internet PKI. It was developed by the US government for use withAboth the RSA and DSA signature algorithms. However, MD5 is used in other legacy applications, but it is still reasonable to use MD5 to verify existing signatures. RSA andEDSA are the most popular signature algorithms used in the Internet. They combine TRSA with either MD5 or SHA-1 one-way hash functions; DSA is used in conjunction with the SHA-1 one-way hash function. The signature algorithm with the MD5 and RSA encryption algorithm is defined in PKCS#1 (RFC 2437). The signature algorithm with the SHA-1 and RSA encryption algorithms is implemented using the padding and encoding mechanisms also described in PKCS#1 (RFC 2437).
6.3 Functional Roles of PKI Entities
This section describes the functional roles of the whole entities at all levels within the PKI. It also describes how the PAA, PCAs, CAs and ORAs perform.
6.3.1Policy Approval Authority
The PAA is the root of the certificate management infrastructure. This authority is known to all entities at all levels in the PKI and creates the overall guidelines that all users, CAs and subordinate policy-making authorities must follow.
The PAA approves policies established on behalf of subclasses of users or communities of interest. It is also responsible for supervising other policy-making authorities.
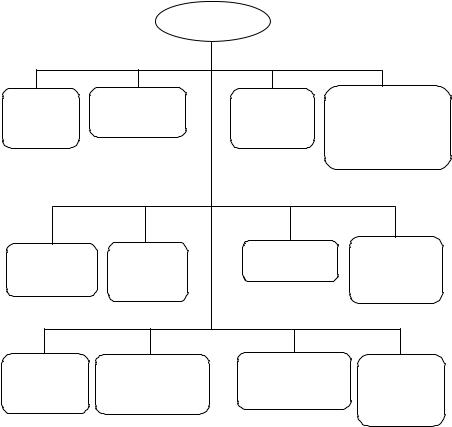
Figure 6.3 illustrates the PAA functions and their performances. Each PAA performs the following functions:
•Publishes the PAA’s public key.
•Sets the policies and procedures that entities (PCAs, CAs, ORAs and users) of the infrastructure should follow.
•Sets the policies and procedures, if any, for a new PCA to join the PKI.
Team-Fly®
PUBLIC-KEY INFRASTRUCTURE |
211 |
PAA functions
Publication |
Policy making |
Procedures |
Authentication of |
of PAA’s |
for all entities |
for joining a |
subordinate PCAs and |
public key |
|
new PCA |
cross - certification of |
|
|
|
international |
|
|
|
infrastructure root |
Generation of |
Locality |
Publication of all |
Specification |
|
PCA’s policies |
for revocation |
|||
PCA’s |
information |
|||
of PCA’s |
||||
certificates |
of PCAs |
|
||
|
certificate |
|||
|
|
|
Authentication |
Generation of CRLs |
Archiving of |
Deposition of |
|
certificates, CRLs |
||||
for revocation |
for all issuing |
certificates |
||
and PCA’s policies |
||||
request |
certification |
and CRLs in |
||
|
||||
|
|
|
the directory |
Figure 6.3 Illustration of PAA functions.
•Carries out identification and authentication of each of its subordinate PCAs and national or international infrastructure roots and judges the proper measures to be taken for cross-certification.
•Generates certificates of subordinate PCAs and of national or international infrastructure roots to be cross-certified.
•Publishes identification and locality of subordinate PCAs such as directory name, e-mail address, postal address, phone number, fax number, etc.
•Receives and publishes policies of all subordinate PCAs.
•Specifies information required from subordinate PCAs for a revocation request of the PCA’s certificate.
•Receives and authenticates revocation requests concerning certificates it has generated.
•Generates CRLs for all the certificates it has issued.
•Archives certificates, CRLs, audit files and PCA’s policies.
•Deposits the certificates and the CRLs it generates in the directory.
212 |
INTERNET SECURITY |
6.3.2 Policy Certification Authority
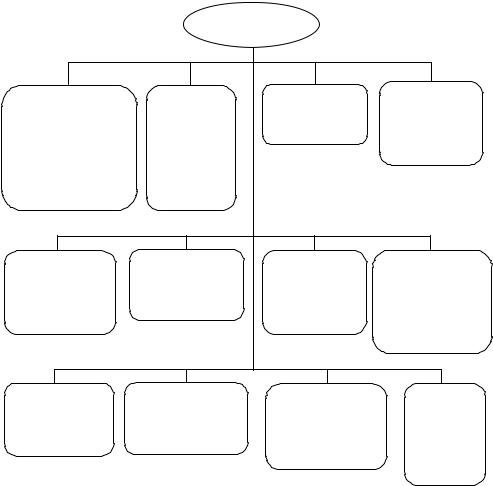
PCAs are formed by all entities at the second level of the infrastructure. Each PCA describes the users whom it serves. All PCAs have both policy and certification responsibilities, and must publish their security policies, procedures, legal issues, fees, or any other subjects they may consider necessary. For PCAs, the users may be people who are affiliated to an organisation or part of a specific community, or a non-human entity. All PCA security policies are published and stored on an end user’s local database. Each PCA performs the following functions as illustrated in Figure 6.4.
•Publishes its identification and locality information, such as directory name, e-mail address, postal address, phone number, fax number, etc.
PCA functions
|
|
Publication of the plans |
Publication of its |
|
Publication of its |
Publication of the |
security policy |
||
for which it serves |
||||
identification and locality |
identification |
|
and procedures |
|
information (directory |
and locality |
|
for related items |
|
name, e-mail address, postal |
information of |
|
|
|
address, phone number, fax |
its subordinate |
|
|
|
number, etc.) |
CAs |
|
|
Carrier role of |
Generate and |
Delivery of its |
Specification of |
|
identification and |
manage certificates |
own public key |
||
procedures and |
||||
authentication of its |
of subordinate CAs |
and that of PAA to |
||
information required to |
||||
subordinates |
|
its subordinates |
||
|
validate certificate |
|||
|
|
|
||
|
|
|
revocation requests |
Receipt and authentication of revocation requests
Generation of CRLs for all the certificates it has issued
Archiving certificates, |
Delivery of |
CRLs, audit fields, |
certificates |
and its signed policy |
and CRLs it |
if changed |
generates to |
|
the directory |
Figure 6.4 Illustration of PCA functions.
PUBLIC-KEY INFRASTRUCTURE |
213 |
•Publishes identification and locality information of its CAs.
•Publishes who it plans to serve.
•Publishes its security policy and procedures which specify the following items:
–Who generates key variables p, q, g, x and y.
–The ranges of allowed sizes of p for itself, its CAs and end users.
–Identification and authentication requirements for the PCA, CAs, ORAs and end users.
–Security controls at the PCA and CA systems that generate certificates and CRLs.
–Security controls at ORA systems.
–Security controls for every user’s private key.
–The frequency of CRL issuance.
–The constraints it imposes on naming schemes.
–Audit procedures.
•Carries out identification and authentication of each of its subordinates.
•Generates and manages certificates of subordinate CAs.
•Delivers its own public key and that of PAA to its subordinates.
•Specifies procedures and information required to validate certificate revocation requests.
•Receives and authenticates revocation requests concerning certificates it has generated.
•Generates CRLs for all the certificates it has issued.
•Archives certificates, CRLs, audit files, and its signed policy if changed.
•Delivers the certificates and CRLs it generates to the directory.
6.3.3 Certification Authority
CAs form the next level below the PCAs. The PKI contains many CAs with no policymaking responsibilities. The majority are plain CAs. A few are CAs that are associated with PCAs. A CA has any combination of users and ORAs whom it certifies.
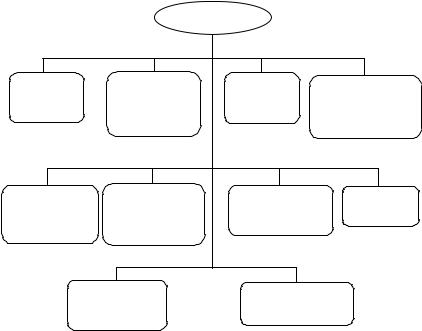
The primary function of the CA is to generate, publish, revoke and archive the publickey certificates that bind the user’s identity with the user’s public key. A better and trusted way of distributing public keys is to use a CA. CAs are expected to certify the public keys of users or of other CAs according to PCA and PAA policies. The CAs ensure that all key parameters are in the range specified by the PCA. Thus, CAs either create key pairs that satisfy the PCA regulations or they examine user-generated keys to ascertain whether they fit within the required range assignment. Referring to Figure 6.5, a CA performs the following functions:
•Publishes and augments PCA policy.
•Carries out identification and authentication of each of its subordinates.
•Generates and manages certificates of subordinates.
•Delivers its own public key and its predecessor’s public keys.
•Verifies ORA certification requests.
•Returns certificate creation confirmations or new certificates to requesting ORA.
•Receives and authenticates revocation requests concerning certificates it has generated.
•Generates CRLs for all the certificates it has issued.
214 |
INTERNET SECURITY |
CA functions
Delivery of |
Carrier role of |
Issuance of |
Delivery of public |
|
identification or |
certificates |
|||
PCA policy |
keys of issuing CA |
|||
authentication for |
for users |
|||
|
and CA’s |
|||
|
users |
|
predecessors |
|
Verification of |
Return of certficate |
Receiving and |
Generation of |
|
ORA certification |
confirmations to |
authenticating |
CRLs |
|
request |
requesting ORA |
revocation requests |
|
|
|
|
Archiving of |
Directory to store |
|
certificates, CRLs |
||
certificate and CRLs |
||
and audit files |
||
|
Figure 6.5 Functions of certificate authority (CA).
•Archives certificates, CRLs and audit files.
•Delivers the certificates and the CRLs it generates to the directory.
6.3.4 Organisational Registration Authority
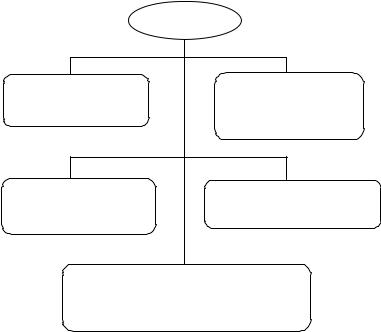
The ORA is the interface between a user and a CA. The prime function that an ORA performs is user identification and authentication on behalf of a CA and it delivers the CA-generated certificate to the end user. After authenticating a user, an ORA transmits a signed request for a certificate to the appropriate CA. In response to an ORA request for key certification, the CA returns a certificate to the ORA. The ORA passes the certificate on to the user. Thus, an ORA’s sole task is to help a user who is far from the user’s CA to register with that CA and to obtain a public-key certificate. ORAs must pass certificate revocation reports timely and accurately to a CA. In order to verify the signature on the information at a future time, ORAs must archive the public key or the certificate associated with the signer. The ORA uses a signed message to inform the CA of the need to revoke the certificate and to issue a new one. Nowadays RA is preferred for simple use rather than ORA. An ORA performs the following functions that are illustrated in Figure 6.6:
•Carries out identification and authentication of users.
•Sends user identification information and the user’s public key to the CA in a signed message.
•Receives and verifies certificate creations or new certificates from the CA.
PUBLIC-KEY INFRASTRUCTURE |
215 |
ORA functions
Carry out identification |
Send user’s identification |
and authentication of users |
information and public key to |
|
the CA |
Receive and verify certificate creations or new certificates from the CA
Deliver CA’s public key and its Predecessor’s public key to the user
Receive certificate revocation requests, verify the validity of the requests, and if valid, send the request to the CA
Figure 6.6 Illustration of ORA functions.
•Delivers the CA’s public key and its predecessor’s public keys as well as the certificate to the user if returned.
•Receives certificate revocation requests, verifies the validity of the requests, and if valid, sends the request to the CA.
6.4 Key Elements for PKI Operations
This section describes operational concepts of the PKI. In order to comprehend the overall PKI operation, one must understand how it conducts its various activities. Each activity is broken down into functional steps. The resources required for each functional step within each activity must be defined. The resources required for an activity are presented in relation to the entities such as User, KG, CA, ORA, PCA or Directory. The steps associated with PKI activities are applied to all PKI relationships: User – CA, User – ORA, ORA – CA, CA – PCA and PCA – PAA.
This section also presents the architectural structures for the PKI certificate management infrastructure. These structures should allow users to establish chains of trust that contain no more than a few certificates in length. The functions and responsibilities of the CAs and PCAs are briefly reviewed and then how the CAs are interconnected to permit establishment of reliable certification paths. Some major activities associated with the PKI operations are presented subsequently.
216 |
INTERNET SECURITY |
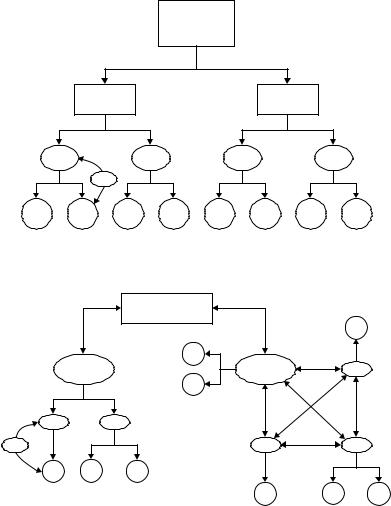
6.4.1 Hierarchical Tree Structures
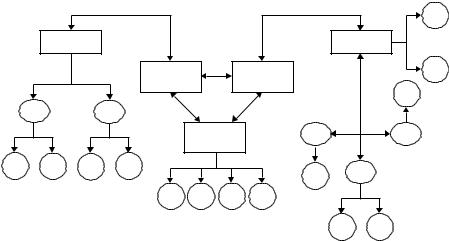
Chains of trust follow a strict tree hierarchy with a root CA (PAA or PCA) to which all trust is referenced. Each CA certifies the public keys of its users and the public key of the root CA is distributed to all PKI entities. Thus every entity is linked to the root CA via a unique trust path. Figure 6.7 depicts such a tree structure. A number of hierarchies may be joined together by cross-certifying their root CA directly or using bridge CAs. Figure 6.8 illustrates a bridge-type scheme joining a hierarchical tree structure to a mesh structure.
PAA
(root CA)
|
|
PCA |
|
|
|
PCA |
|
|
CA |
|
CA |
|
CA |
|
CA |
|
|
RA |
|
|
|
|
|
U1 |
U2 |
U3 |
U4 |
U5 |
U6 |
U7 |
U8 |
Figure 6.7 Hierarchical tree structure.
|
|
Bridge CA |
|
|
|
|
|
U9 |
|
|
|
U4 |
|
|
|
Root |
Root |
CA |
|
|
CA |
CA |
|
|
|
|
|
||
|
|
U5 |
|
|
CA |
CA |
|
|
|
RA |
|
CA |
CA |
|
U1 |
U2 |
U3 |
|
|
|
|
U6 |
U7 |
U8 |
Hierarchical structure |
|
Mesh structure |
|
|
Figure 6.8 A mixed structure using a bridge CA.
PUBLIC-KEY INFRASTRUCTURE |
217 |
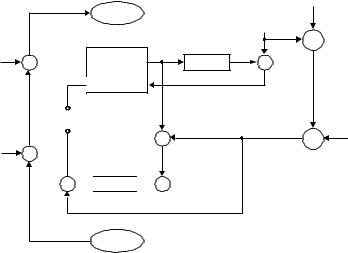
With a mesh structure, entities may be connected via several chains of trust. PGP is a PKI that uses a mesh structure, with every entity acting as their own CA. Gateway structures are new structure appearing in VPN applications. In a gateway structure, each domain is separated and relies on its gateway to provide external PKI services. Figure 6.9 depicts a gateway structure with three cross-certified gateways through which the trust of the network is channelled. Horizontal structures offer improved robustness to penetration by distributing the trust path horizontally. Multiple platform structures can be used to introduce redundancy into a PKI structure and thus reduce risk. The public key of each user is authenticated in each platform. This is a particular advantage with hierarchical structures because it can remove a single point of failure.
6.4.2 Policy-making Authority
Chains of trust are based on appropriate policies at all levels in the infrastructure. Associated with the entire PKI is a policy-establishing authority which will create the overall guidelines and security policies that all users, CAs and subordinate policy-making authorities must follow.
•The PAA has the responsibility of supervising other policy-making authorities. The PAA will approve policies established on behalf of subclasses of users or of communities of interest.
•The PCAs will create policy details that expand or extend the overall PAA policies. Each PCA establishes policy for a single organisation or for a single community of interest. PCAs must publish their security policies, procedures, any legal issues, any fees or any other subjects that they consider necessary.
•The CAs are expected to certify the public key of end users or of other CAs in accordance with PCA and PAA policies. The CA must ensure that all key parameters
|
|
|
|
|
|
|
U5 |
|
Root CA |
|
|
|
Root CA |
||
|
|
|
Gateway 1 |
|
Gateway 2 |
U6 |
|
|
|
|
|
|
|||
|
|
|
|
|
|
|
U10 |
|
CA |
|
CA |
|
|
|
|
|
|
|
|
Gateway 3 |
CA |
CA |
|
|
|
|
|
|
|
||
U1 |
U2 |
U3 |
U4 |
|
|
U7 |
CA |
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
|
|
U11 |
U12 |
U13 |
U14 |
|
|
|
|
|
|
|
U8 |
U9 |
Figure 6.9 A gateway structure.
218 |
INTERNET SECURITY |
are in the range specified by the PCA. Therefore, the CA either creates key pairs according to the PCA regulations or examines the user-generated keys to ascertain that they satisfy the requirements of the range. A few CAs are associated with PCAs, but the majority are plain CAs at all points in the infrastructure.
•The ORA submits a certificate request on behalf of an authenticated entity. The CA returns the signed certificate or an error message to the ORA. The ORA or certificate holder requests revocation of a certificate to the issuing CA. The CA responds with acceptance or rejection of the revocation request. Certificate Revocation Lists (CRLs) contain all revoked certificates that CAs have issued and have not expired. The CA returns the signed certificate and its certificate or an error message to the end user. The CA posts a new certificate and CRL to the repository.
6.4.3 Cross-certification
Suppose the CA has its private/public-key pair and the X.509 certificate issued by the CA. If a user knows the CA’s public key, then the user can decrypt the certificate with the CA’s public key and verify the X.509 certificate signed by the CA. Thus the user can recover his or her public key contained in the X.509 certificate; the user’s public key is verified as illustrated in Figure 6.10.
|
(ID, KPu) |
|
|
|
|
Ke |
|
|
CA |
|
|
|
|
|
|
|
|
|
|
|
KSc |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Ep |
RSA encryption |
KPu |
D |
X.509 |
m |
SHA-1 |
h |
E |
|
|
|
|
|||||
certificate |
|
|
|
||||
|
|
Signature |
|
|
|
|
|
|
|
Compare |
|
|
KSc |
|
|
|
|
|
E |
|
Dp |
Kd |
|
|
|
|
|
|
|||
KSu |
E |
|
|
|
|
|
RSA decryption |
hm
E 
 SHA-1
SHA-1  D
D  KPc
KPc
USER
(ID, KPu) |
|
|
|
KPu |
: User’s public key |
KPc |
: CA’s public key |
KSu |
: User’s private key |
KSc |
: CA’s private key |
Ke |
: RSA public key |
Kd |
: RSA private key |
SHA-1 : One-way hash function |
h |
: Certificate message digest |
|
E/D |
: Public-key encryption/decryption |
Ep/Dp : RSA encryption/decryption |
|
m |
: X.509 certificate |
ID |
: User ID |
Figure 6.10 Certification of the user’s public key.
PUBLIC-KEY INFRASTRUCTURE |
219 |
The signature algorithm and one-way hash function used to sign a certificate are indicated by use of an algorithm identifier or OID. The one-way hash functions commonly used are SHA-1 and MD5. RSA and DSA are the most popular signature algorithms used in the X.509 Public-Key Infrastructure (PKIX).
Because no one can modify the certificate, it can be placed in a directory without any special effort made to protect the certificate. A user can transmit his or her certificate directly to other users. In the case when a CA encompasses several users, there must be a common trust of that CA. These users’ certificates can be stored in the directory for access by all users.
When all users in a large community subscribe to the same CA, it may not be practical for these users. With many users, it is more desirable to have a limited number of participating CAs, each CA securely providing its public key to the subordinate users. Since the CA signs the certificates, each user must have a copy of the CA’s public key to verify signatures. The CA should provide its public key to each user in an absolutely secure way so that the user has confidence in the associated certificates.
Suppose there are two users A and B. A certificate is defined in the following notation:
X << A >>
which means the certificate of user A issued by certification authority X. Consider Figure 6.11(a) which depicts a simple example, where X1 and X2 represent two CAs. User A uses a chain of certificates to obtain user B’s public key. The chain of certificates is expressed as:
X1 X2 X2 B
Similarly, user B can obtain A’s public key with the reverse chain such that:
X2 X1 X1 A
This scheme need not be limited to a chain of two certificates. An arbitrarily long path of CAs can produce a chain. All the certificates of CAs by CAs need to appear in the directory, and the user needs to know how they are linked to follow a path to another user’s public-key certificate. X.509 suggests that CAs be arranged in a hierarchy so that tracing is straightforward.
Figure 6.11(b) is an example of such a hierarchy. The connected ellipses circles indicate the hierarchical relationship among CAs; the associated boxes indicate certificates maintained in the directory for each CA entry. Four users are indicated by circles. In this example, user A can acquire the following certificates from the directory to establish a certification path to user B:
X Y Y W W U U V V B
When A has obtained these certificates, A can unwrap the certification path in sequence to recover a trusted copy of B’s public key. Using this public key, A can send encrypted messages to B. If A wishes to receive encrypted messages back from B, or to sign
