
- •Write down the rsa alg. Step by step in right order without an example. Also show encryption & decryption formulas.
- •Explain the Hash function by using the general formula. Give an example of hash algorithm.
- •Describe the Direct Digital Signature.
- •Kerberos: Give description, short dialogue between user and server.
- •What is the algorithm of message sending in pgp? Number below operations in the right order.
- •What are the types of ‘headers’ that involve in ipSec? Describe these headers in few words.
- •Describe Alert Protocol involving in ssl.
- •Describe the Intrusion Detection System. What is a Statistical Anomaly Detection?
- •What is a Firewall? Name the types of Firewall and describe any one of them.
- •What is Malicious Software? Describe ddos and countermeasures.
- •Information Security
- •Write down aes operations in right order for one round:
- •Write down the Diffie-Hellman Key exchange alg. Step by step in right order without an example and for two sides.
- •Describe the Intrusion Detection System. What is a Rule-based detection?
- •What is a Firewall? Name configurations of Firewall and describe any one of them.
- •What is Malicious Software? Describe Worms and their phases.
Information Security
Final
1-variant
Name, surname: Group:
Good Luck!!!
Questions (1-10 questions are main and q.11 is bonus)
Write the DES operations filling below boxes in right order:

Write down the rsa alg. Step by step in right order without an example. Also show encryption & decryption formulas.
each user generates a public/private key pair by:
selecting two large primes at random - p, q
computing their system modulus n=p.q
note ø(n)=(p-1)(q-1)
selecting at random the encryption key e
where 1<e<ø(n), gcd(e,ø(n))=1
solve following equation to find decryption key d
e.d=1 mod ø(n) and 0≤d≤n
publish their public encryption key: PU={e,n}
keep secret private decryption key: PR={d,n}
to encrypt a message M the sender:
obtains public key of recipient PU={e,n}
computes: C = Me mod n, where 0≤M<n
to decrypt the ciphertext C the owner:
uses their private key PR={d,n}
computes: M = Cd mod n
note that the message M must be smaller than the modulus n (block if needed)
Explain the Hash function by using the general formula. Give an example of hash algorithm.
can be applied to any sized message M
produces fixed-length output h
is easy to compute h=H(M) for any message M
given h is infeasible to find x s.t. H(x)=h
one-way property
given x is infeasible to find y s.t. H(y)=H(x)
weak collision resistance
is infeasible to find any x,y s.t. H(y)=H(x)
strong collision resistance
ex:Bithday algorithm
Describe the Direct Digital Signature.
involve only sender & receiver
assumed receiver has sender’s public-key
digital signature made by sender signing entire message or hash with private-key
can encrypt using receivers public-key
important that sign first then encrypt message & signature
security depends on sender’s private-key
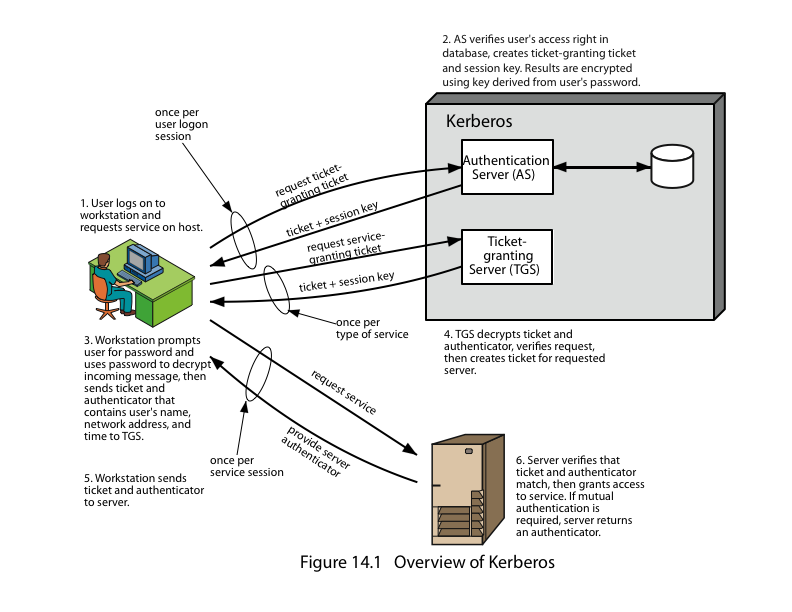
Kerberos: Give description, short dialogue between user and server.
trusted key server system from MIT
provides centralised private-key third-party authentication in a distributed network
allows users access to services distributed through network
without needing to trust all workstations
rather all trust a central authentication server
two versions in use: 4 & 5
obtain ticket granting ticket from AS
once per session
obtain service granting ticket from TGT
for each distinct service required
client/server exchange to obtain service
on every service request
What is the algorithm of message sending in pgp? Number below operations in the right order.
2… PGP prompts the user for the passphrase to recover the unencrypted private key.
6… The session key component of the message is constructed.
1… PGP retrieves the sender's private key from the private-key ring using your_userid as an index. If your_userid was not provided in the command, the first private key on the ring is retrieved.
4… PGP generates a session key and encrypts the message.
5… PGP retrieves the recipient's public key from the public-key ring using her_userid as an index.
3… The signature component of the message is constructed.
What are the types of ‘headers’ that involve in ipSec? Describe these headers in few words.
Support for these features is mandatory for IPv6 and optional for IPv4. In both cases, the security features are implemented as extension headers that follow the main IP header. The extension header for authentication is known as the Authentication header; that for encryption is known as the Encapsulating Security Payload (ESP) header.
