
- •Introduction
- •Applications of Real-Time Systems
- •Voltage
- •Figure 7: Conversion of an Analog Signal to a 16 bit Binary Number
- •Figure 11: Schematic Representation of tmr
- •It is relatively simple to design a hardware equipment to be fault-tolerant. The following are two methods that are popularly used to achieve hardware fault-tolerance:
- •Software Fault-Tolerance Techniques
- •Types of Real-Time Tasks
- •Timing Constraints
- •Events in a Real-Time System
- •Figure 16: Delay Constraint Between Two Events el and e2
- •Examples of Different Types of Timing Constraints
- •Figure 19: Classification of Timing Constraints
- •Real-Time Task Scheduling
- •Figure 1: Relative and Absolute Deadlines of a Task
- •Figure 2: Precedence Relation Among Tasks
- •Types of Real-Time Tasks and Their Characteristics
- •Classification of Real-Time Task Scheduling Algorithms
- •Figure 5: An Example Schedule Table for a Cyclic Scheduler
- •Figure 6: Major and Minor Cycles in a Cyclic Scheduler
- •Comparison of Cyclic with Table-Driven Scheduling
- •Hybrid Schedulers
- •Event-driven Scheduling
- •Is edf Really a Dynamic Priority Scheduling Algorithm?
- •Implementation of edf
- •Figure 10: Priority Assignment to Tasks in rma
- •We now illustrate the applicability of the rma schodulability criteria through a few examples.
- •Deadline Monotonic Algorithm (dma)
- •Handling Aperiodic and Sporadic Tasks
- •Dealing With Task Jitter
- •W Good real-time task scheduling algorithms ensure fairness to real-time tasks while scheduling.
- •State whether the following assertions are True or False. Write one or two sentences to justify your choice in each case.
- •Figure 2: Unbounded Priority Inversion
- •Highest Locker Protocol(hlp)
- •Priority Ceiling Protocol (pcp)
- •Comparison of Resource Sharing Protocols
- •Handling Task Dependencies
- •Fault-Tolerant Scheduling of Tasks
- •Clocks in Distributed Real-Time Systems
- •Clock Synchronization
- •Figure 1: Centralized synchronization system
- •Cn Slave clocks
- •Commercial Real-Time Operating Systems
- •Time Services
- •Clock Interrupt Processing
- •Providing High Clock Resolution
- •Figure 2: Use of a Watchdog Tinier
- •Unix as a Real-Time Operating System
- •In Unix, dynamic priority computations cause I/o intensive tasks to migrate to higher and higher priority levels, whereas cpu-intensive tasks are made to seek lower priority levels.
- •Host-Target Approach
- •Preemption Point Approach
- •Self-Host Systems
- •Windows As a Real-Time Operating System
- •Figure 9: Task Priorities in Windows nt
- •Open Software
- •Genesis of posix
- •Overview of posix
- •Real-Time posix Standard
- •Rt Linux
- •7.8 Windows ce
- •Benchmarking Real-Time Systems
- •Figure 13: Task Switching Time Among Equal Priority Tasks
- •Real-Time Communication
- •Figure 2: a Bus Architecture
- •Figure 4: Logical Ring in a Token Bus
- •Soft Real-Time Communication in a lan
- •Figure 6: Priority Arbitration Example
- •Figure 8: Problem in Virtual Time Protocol
- •Figure 9: Structure of a Token in ieee 802.5
- •Figure 10: Frames in the Window-based Protocol
- •Performance Comparison
- •A Basic Service Model
- •Traffic Characterization
- •Figure 16: Constant Bit-Rato Traffic
- •Routing Algorithms
- •Resource Reservation
- •Resource Reservation Protocol (rsvp)
- •Traffic Shaping and Policing
- •Traffic Distortion
- •Traffic Scheduling Disciplines
- •Figure 20: Packet Service in Jittor-edd
- •Differentiated Services
- •Functional Elements of DiffServ Architecture
- •Real Time Databases
- •Isolation: Transactions are executed concurrently as long as they do not interfere in each other’s computations.
- •Real-Time Databases
- •Real-Time Database Application Design Issues
- •Temporal Consistency
- •Concurrency Control in Real-Time Databases
- •It can bo shown that pcp is doadlock froo and single blocking. Rocolloct that single blocking moans that once a transaction starts executing after being blocked, it may not block again.
- •Speculative Concurrency Control
- •Comparison of Concurrency Control Protocols
- •Commercial Real-Time Databases
- •Figure 16: Uniform Priority Assignment to Tasks of Example 15
- •Version 2 cse, iit Kharagpur
Traffic Shaping and Policing
As already discussed, some mechanism to regulate the flow of packets in the network is needed, so that the greedy or malicious real-time or non real-time sources do not negatively affect the QoS guarantees given to other connections. Shaping and policing are the mechanisms used to ensure this. Table 6.1 summarizes the key differences between shaping and policing. The choice between which one to use depends on the type of application and its specific QoS requirements.
Shaping
Policing
Objective
Buffers and queues the excess packets above the committed
rates.
Drops the excess packets over the committed rates. Does not
buffer.
Handling
Bursts
Uses a leaky bucket, to delay traffic, achieving a smoothing
effect.
Propagates bursts. Does no smoothing.
Advantage
Avoids retransmission due to dropped packets.
Avoids delay due to qnening.
Disadvantages
Can introduce delays due to qnening.
Can reduce throughput of affected streams.
Table.
6.1: Traffic Shaping versus Policing
Several traffic shaping and policing techniques are available. In the following, we discuss an important traffic shaping and policing technique.
Token Bucket with Leaky Rate Control
3
о
о о 3000
Figure
17: Token Bucket With Leaky Rate Control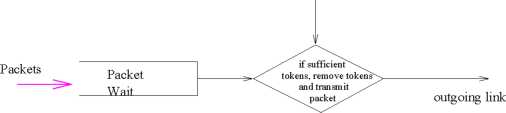
In leaky rate control, a waiting packet is taken for transmission only if there is at least one token in the bucket. If enough tokens are not available in the bucket, then the packet either waits until the bucket has enough tokens in case of a shaper. In case of a policor, the packet is either discarded or is marked down. The token is removed, if transmission of the packet takes place. Because there can be at most b tokens in the bucket, the maximum burst size of a leaky-bucket-policed flow is b packets. Furthermore, because the token generation rate is r, the maximum number of packets that can enter the network of any interval of time of length t is rt + b. Thus, the token generation rate, r, serves to limit the long-term average rate at which the packet can enter the network. This technique can also be used to police the peak rate along with long-term average rate.
Scheduling Mechanisms
Figure
18: A Model of A Packet Switched Network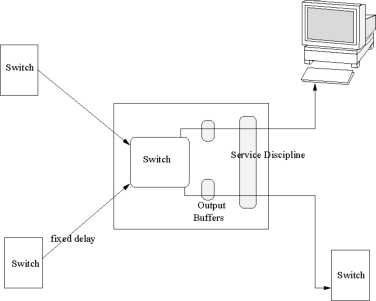
A simple model of an Internet is a collection of sending and receiving nodes and network switches. At every switch, there may be many incoming and many outgoing communication links as shown in Fig. 18. Depending
upon destination of a packet, it is queued on buffer queue of particular outgoing link. A scheduler selects packets to be transmitted from the buffer at the output link based on some scheduling policy. A service discipline schedules incoming packets for transmission. For real time connection, rate based service disciplines are used to protect the guarantees given to connections from network load fluctuations. This guarantees a minimum service rate to individual connections regardless of the traffic generated by other connections.
The Buffer requirements at a switch depends on maximum packet arrival rate, maximum packet size and the expected sojourn time of packets. On the other hand, the buffer requirements at the receiving end is equal to the product of delay jitter, and the maximum packet arrival rate and packet size.
The service discipline at any time decides which output buffers would be taken up for transmission next. The switch/router does the switching of the data packets from its input port to the desired output port, so that it reaches the destination address. Every switch/router can be modeled as a queue, where packets from different flows compete for the switching processing time and output link. There may be many incoming links to a switch, there may be a number of virtual connections for each link, and there may be a number of packets in each connection to be served. These packets may compete for the same output link. The manner in which the queued packets are selected for the transmission on the link is known as link or traffic scheduling discipline. The scheduling discipline at each switch selects which packet to transmit next by discriminating packets based on their QoS requirements.
