
- •Introduction
- •Applications of Real-Time Systems
- •Voltage
- •Figure 7: Conversion of an Analog Signal to a 16 bit Binary Number
- •Figure 11: Schematic Representation of tmr
- •It is relatively simple to design a hardware equipment to be fault-tolerant. The following are two methods that are popularly used to achieve hardware fault-tolerance:
- •Software Fault-Tolerance Techniques
- •Types of Real-Time Tasks
- •Timing Constraints
- •Events in a Real-Time System
- •Figure 16: Delay Constraint Between Two Events el and e2
- •Examples of Different Types of Timing Constraints
- •Figure 19: Classification of Timing Constraints
- •Real-Time Task Scheduling
- •Figure 1: Relative and Absolute Deadlines of a Task
- •Figure 2: Precedence Relation Among Tasks
- •Types of Real-Time Tasks and Their Characteristics
- •Classification of Real-Time Task Scheduling Algorithms
- •Figure 5: An Example Schedule Table for a Cyclic Scheduler
- •Figure 6: Major and Minor Cycles in a Cyclic Scheduler
- •Comparison of Cyclic with Table-Driven Scheduling
- •Hybrid Schedulers
- •Event-driven Scheduling
- •Is edf Really a Dynamic Priority Scheduling Algorithm?
- •Implementation of edf
- •Figure 10: Priority Assignment to Tasks in rma
- •We now illustrate the applicability of the rma schodulability criteria through a few examples.
- •Deadline Monotonic Algorithm (dma)
- •Handling Aperiodic and Sporadic Tasks
- •Dealing With Task Jitter
- •W Good real-time task scheduling algorithms ensure fairness to real-time tasks while scheduling.
- •State whether the following assertions are True or False. Write one or two sentences to justify your choice in each case.
- •Figure 2: Unbounded Priority Inversion
- •Highest Locker Protocol(hlp)
- •Priority Ceiling Protocol (pcp)
- •Comparison of Resource Sharing Protocols
- •Handling Task Dependencies
- •Fault-Tolerant Scheduling of Tasks
- •Clocks in Distributed Real-Time Systems
- •Clock Synchronization
- •Figure 1: Centralized synchronization system
- •Cn Slave clocks
- •Commercial Real-Time Operating Systems
- •Time Services
- •Clock Interrupt Processing
- •Providing High Clock Resolution
- •Figure 2: Use of a Watchdog Tinier
- •Unix as a Real-Time Operating System
- •In Unix, dynamic priority computations cause I/o intensive tasks to migrate to higher and higher priority levels, whereas cpu-intensive tasks are made to seek lower priority levels.
- •Host-Target Approach
- •Preemption Point Approach
- •Self-Host Systems
- •Windows As a Real-Time Operating System
- •Figure 9: Task Priorities in Windows nt
- •Open Software
- •Genesis of posix
- •Overview of posix
- •Real-Time posix Standard
- •Rt Linux
- •7.8 Windows ce
- •Benchmarking Real-Time Systems
- •Figure 13: Task Switching Time Among Equal Priority Tasks
- •Real-Time Communication
- •Figure 2: a Bus Architecture
- •Figure 4: Logical Ring in a Token Bus
- •Soft Real-Time Communication in a lan
- •Figure 6: Priority Arbitration Example
- •Figure 8: Problem in Virtual Time Protocol
- •Figure 9: Structure of a Token in ieee 802.5
- •Figure 10: Frames in the Window-based Protocol
- •Performance Comparison
- •A Basic Service Model
- •Traffic Characterization
- •Figure 16: Constant Bit-Rato Traffic
- •Routing Algorithms
- •Resource Reservation
- •Resource Reservation Protocol (rsvp)
- •Traffic Shaping and Policing
- •Traffic Distortion
- •Traffic Scheduling Disciplines
- •Figure 20: Packet Service in Jittor-edd
- •Differentiated Services
- •Functional Elements of DiffServ Architecture
- •Real Time Databases
- •Isolation: Transactions are executed concurrently as long as they do not interfere in each other’s computations.
- •Real-Time Databases
- •Real-Time Database Application Design Issues
- •Temporal Consistency
- •Concurrency Control in Real-Time Databases
- •It can bo shown that pcp is doadlock froo and single blocking. Rocolloct that single blocking moans that once a transaction starts executing after being blocked, it may not block again.
- •Speculative Concurrency Control
- •Comparison of Concurrency Control Protocols
- •Commercial Real-Time Databases
- •Figure 16: Uniform Priority Assignment to Tasks of Example 15
- •Version 2 cse, iit Kharagpur
A Basic Service Model
The basic Internet service model has schematically been shown in Fig. 15.
core
router
Figure
15: A Simple Model of the Internet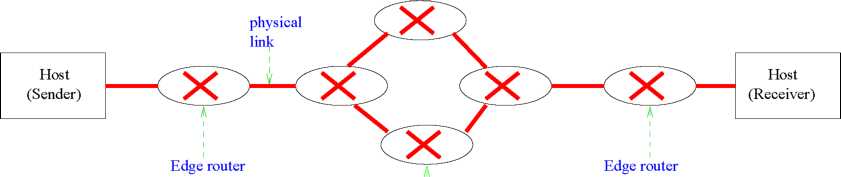
The Ingress router is the router attached at the sender’s end. It is the first interface to the data sent by the sender host. The type of physical link used at a link may be a twisted pair cable, a fiber optic cable, and even wireless link. The Internet service is provided by an Internet Service Provider (ISP). Therefore, the data passes through the ISP’s routers. These are termed as core routers. The density of these routers is very high at the ISP end, since huge amount of data and links typically converge at the ISP. From the core routers, the data is forwarded through the egress routers (at the receiver end) to the corresponding receivers.
Real-Time communication can be supported on the Internet by providing preferential treatment to data of certain senders that have entered into a contract with the ISP. But for that data packets should have been classified before transmission. At the connection set-up time, the sender provides the ISP with two parameters: the traffic specification and the service specification. The ISP uses this to determine whether it can accept or has to refuse the client request. It checks for the resources on the possible routes of that packet data. Alternatively, we can say it tries to find a path (unicast or multicast routing) that has the necessary resources to satisfy the required QoS for the specified traffic pattern to be generated by the source.
If the network accepts the connection request, then it promises that the data transmission service will meet (or exceed) the client-specified performance bounds. However, the given guarantee remains valid only if the clientgenerated traffic remains within the specified traffic bounds. If the client traffic violates the prespecified traffic bounds, then the network may drop packets, or reshape the traffic.
Another important component of this approach is the protection given to the real-time connections. Note that the network service will meet the given performance bounds as long as the client traffic remains within the traffic specification, irrespective of the behavior of other clients. Now, this performance cannot be guaranteed, if the connections are not protected from the misbehaving (or malicious) real-time and non real-time sources. To avoid violating the guarantees made to real-time connections, the network must either explicitly control the input rates on a por-connoction basis i.e. shaping and policing of the data, or adopt scheduling algorithms that will do so automatically in tho nodos (o.g., Fair Queuing, Weighted Fair Queuing, etc.).
Those techniques are a part of integrated software architectures like IntSorv, DiffSorv etc., which have boon designed keeping in mind various issues pertaining to roal-timo communication. Wo discuss those issues in tho following.
