
- •Introduction
- •Applications of Real-Time Systems
- •Voltage
- •Figure 7: Conversion of an Analog Signal to a 16 bit Binary Number
- •Figure 11: Schematic Representation of tmr
- •It is relatively simple to design a hardware equipment to be fault-tolerant. The following are two methods that are popularly used to achieve hardware fault-tolerance:
- •Software Fault-Tolerance Techniques
- •Types of Real-Time Tasks
- •Timing Constraints
- •Events in a Real-Time System
- •Figure 16: Delay Constraint Between Two Events el and e2
- •Examples of Different Types of Timing Constraints
- •Figure 19: Classification of Timing Constraints
- •Real-Time Task Scheduling
- •Figure 1: Relative and Absolute Deadlines of a Task
- •Figure 2: Precedence Relation Among Tasks
- •Types of Real-Time Tasks and Their Characteristics
- •Classification of Real-Time Task Scheduling Algorithms
- •Figure 5: An Example Schedule Table for a Cyclic Scheduler
- •Figure 6: Major and Minor Cycles in a Cyclic Scheduler
- •Comparison of Cyclic with Table-Driven Scheduling
- •Hybrid Schedulers
- •Event-driven Scheduling
- •Is edf Really a Dynamic Priority Scheduling Algorithm?
- •Implementation of edf
- •Figure 10: Priority Assignment to Tasks in rma
- •We now illustrate the applicability of the rma schodulability criteria through a few examples.
- •Deadline Monotonic Algorithm (dma)
- •Handling Aperiodic and Sporadic Tasks
- •Dealing With Task Jitter
- •W Good real-time task scheduling algorithms ensure fairness to real-time tasks while scheduling.
- •State whether the following assertions are True or False. Write one or two sentences to justify your choice in each case.
- •Figure 2: Unbounded Priority Inversion
- •Highest Locker Protocol(hlp)
- •Priority Ceiling Protocol (pcp)
- •Comparison of Resource Sharing Protocols
- •Handling Task Dependencies
- •Fault-Tolerant Scheduling of Tasks
- •Clocks in Distributed Real-Time Systems
- •Clock Synchronization
- •Figure 1: Centralized synchronization system
- •Cn Slave clocks
- •Commercial Real-Time Operating Systems
- •Time Services
- •Clock Interrupt Processing
- •Providing High Clock Resolution
- •Figure 2: Use of a Watchdog Tinier
- •Unix as a Real-Time Operating System
- •In Unix, dynamic priority computations cause I/o intensive tasks to migrate to higher and higher priority levels, whereas cpu-intensive tasks are made to seek lower priority levels.
- •Host-Target Approach
- •Preemption Point Approach
- •Self-Host Systems
- •Windows As a Real-Time Operating System
- •Figure 9: Task Priorities in Windows nt
- •Open Software
- •Genesis of posix
- •Overview of posix
- •Real-Time posix Standard
- •Rt Linux
- •7.8 Windows ce
- •Benchmarking Real-Time Systems
- •Figure 13: Task Switching Time Among Equal Priority Tasks
- •Real-Time Communication
- •Figure 2: a Bus Architecture
- •Figure 4: Logical Ring in a Token Bus
- •Soft Real-Time Communication in a lan
- •Figure 6: Priority Arbitration Example
- •Figure 8: Problem in Virtual Time Protocol
- •Figure 9: Structure of a Token in ieee 802.5
- •Figure 10: Frames in the Window-based Protocol
- •Performance Comparison
- •A Basic Service Model
- •Traffic Characterization
- •Figure 16: Constant Bit-Rato Traffic
- •Routing Algorithms
- •Resource Reservation
- •Resource Reservation Protocol (rsvp)
- •Traffic Shaping and Policing
- •Traffic Distortion
- •Traffic Scheduling Disciplines
- •Figure 20: Packet Service in Jittor-edd
- •Differentiated Services
- •Functional Elements of DiffServ Architecture
- •Real Time Databases
- •Isolation: Transactions are executed concurrently as long as they do not interfere in each other’s computations.
- •Real-Time Databases
- •Real-Time Database Application Design Issues
- •Temporal Consistency
- •Concurrency Control in Real-Time Databases
- •It can bo shown that pcp is doadlock froo and single blocking. Rocolloct that single blocking moans that once a transaction starts executing after being blocked, it may not block again.
- •Speculative Concurrency Control
- •Comparison of Concurrency Control Protocols
- •Commercial Real-Time Databases
- •Figure 16: Uniform Priority Assignment to Tasks of Example 15
- •Version 2 cse, iit Kharagpur
Performance Comparison
At tho dosign timo, a dotailod knowlodgo of tho mossago sot is oft on unavailable. Howovor, tho dosignors of a roal- timo network usually have an estimate of tho traffic generated by tho different roal-timo sources in terms of tho respective channel utilization. Therefore, tho following two utilization-based metrics are meaningful while comparing tho performance of different protocols.
Absolute Breakdown Utilization (ABU): This metric indicates tho expected value of utilization of a message set S at which messages start missing deadlines.
о * zES
where C; is tho size of mossago i £ S, and T is its period. Wo can alternately view this metric to indicate how much traffic can bo accommodated in a network without tho messages having to miss their deadlines.
Guarantee Probability(GP(U)): Tho guarantee probability at channel utilization U (GP(U)) indicates tho probability that a mossago sot with utilization U moots all mossago deadline.
Figure
12: Schematic Representation of Message Sets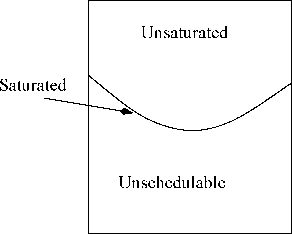
Wo now provide an intuitive explanation of tho metrics. Tho entire population of synchronous messages can bo divided into three classes depending on the schedulability offered as shown in Fig. 12. These three classes of messages are briefly explained in tho following.
Unsaturated Schedulable: Tho mossago sot in this class are schedulable and remain schedulable oven after any message size is slightly increased.
Saturated Schedulable: The message set in this class are schedulable but any increase in the message size of a message would lead to some messages missing their deadlines.
Unschedulable: Unschodulablo set refers to those messages for which deadlines of some messages would be missed.
Wo would expect GP(U) to bo close to 1 for utilization lower than ABU and approach 0 as utilization increases beyond ABU.
In low bandwidth networks, priority-based protocol works bettor; whereas at highor bandwidths, tho bounded access protocol works bettor. Tho performance of tho priority-driven protocol initially improves as tho bandwidth is increased, but starts to drop off beyond a certain point. This is against the intuition that performance of a protocol should improve as the bandwidth is increased.
low
Bandwidth
GP(U)
1
\
1
\
1
1
!
\ 802.5
i
802.4!
1
\ i V 1
1
\
1
\ 1
1
U
Figure
13: GP(U) versus Utilization at Low and High Bandwidths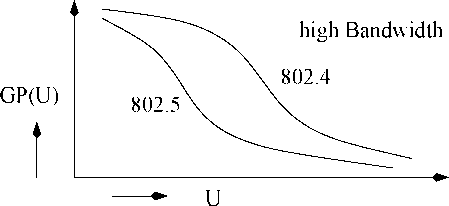
When the bandwidth is increased beyond a certain value, the decrease in transmission time causes the frame transmission time F to be less than the token rotation time в. In this case, before releasing a new token, the transmitting node has to wait for the token to return even after the transmission of the frame is complete to transmit the next packet. Thus, the effective frame transmission time in this case is в and the fraction of the wasted bandwidth is (0-F)/F. The propagation time is independent of the bandwidth and hence can be considered as a constant. The token transmission time decreases with increasing bandwidth. Therefore, the percentage of wasted bandwidth increases with increase in bandwidth.
The timed token protocol does not exhibit this anomaly, because a node is permitted to transmit continuously during its assigned time slot.
In all cases, it can be seen that the guarantee probability remains close to 1 as long as the utilization is less than ABU. There is a sharp drop in the guarantee probability at utilization values close to ABU. This demonstrates that ABU is a robust measure of average performance of real-time networks. Now, we can summarize our observations as follows. At low transmission speeds, the priority inversions caused by the round-robin scheduling approach tends to adversely impact messages with short deadlines. Thus, at low bandwidths priority-driven protocol is better suited than the timed token protocol for real-time applications.
Figure
14: Absolute Breakdown Utilization Versus Bandwidth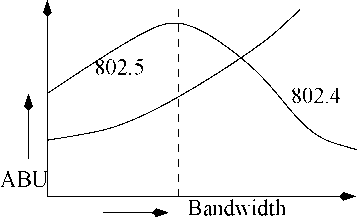
Real-Time Communication Over Internet
From a modest beginning a little over a decade ago, Internet has become a vast repository of information, and enabler of several new applications such as e-commerce. Internet provides best effort service to applications, meaning that traffic is processed as quickly as possible but there is no guarantee of timeliness or actual delivery. With the increasing commercial usage of Internet, there is a need to support soft and firm real-time applications. In this section, we first provide some basic concepts about Internet. Subsequently, we review the recent trends in this area.
