
- •Introduction
- •Applications of Real-Time Systems
- •Voltage
- •Figure 7: Conversion of an Analog Signal to a 16 bit Binary Number
- •Figure 11: Schematic Representation of tmr
- •It is relatively simple to design a hardware equipment to be fault-tolerant. The following are two methods that are popularly used to achieve hardware fault-tolerance:
- •Software Fault-Tolerance Techniques
- •Types of Real-Time Tasks
- •Timing Constraints
- •Events in a Real-Time System
- •Figure 16: Delay Constraint Between Two Events el and e2
- •Examples of Different Types of Timing Constraints
- •Figure 19: Classification of Timing Constraints
- •Real-Time Task Scheduling
- •Figure 1: Relative and Absolute Deadlines of a Task
- •Figure 2: Precedence Relation Among Tasks
- •Types of Real-Time Tasks and Their Characteristics
- •Classification of Real-Time Task Scheduling Algorithms
- •Figure 5: An Example Schedule Table for a Cyclic Scheduler
- •Figure 6: Major and Minor Cycles in a Cyclic Scheduler
- •Comparison of Cyclic with Table-Driven Scheduling
- •Hybrid Schedulers
- •Event-driven Scheduling
- •Is edf Really a Dynamic Priority Scheduling Algorithm?
- •Implementation of edf
- •Figure 10: Priority Assignment to Tasks in rma
- •We now illustrate the applicability of the rma schodulability criteria through a few examples.
- •Deadline Monotonic Algorithm (dma)
- •Handling Aperiodic and Sporadic Tasks
- •Dealing With Task Jitter
- •W Good real-time task scheduling algorithms ensure fairness to real-time tasks while scheduling.
- •State whether the following assertions are True or False. Write one or two sentences to justify your choice in each case.
- •Figure 2: Unbounded Priority Inversion
- •Highest Locker Protocol(hlp)
- •Priority Ceiling Protocol (pcp)
- •Comparison of Resource Sharing Protocols
- •Handling Task Dependencies
- •Fault-Tolerant Scheduling of Tasks
- •Clocks in Distributed Real-Time Systems
- •Clock Synchronization
- •Figure 1: Centralized synchronization system
- •Cn Slave clocks
- •Commercial Real-Time Operating Systems
- •Time Services
- •Clock Interrupt Processing
- •Providing High Clock Resolution
- •Figure 2: Use of a Watchdog Tinier
- •Unix as a Real-Time Operating System
- •In Unix, dynamic priority computations cause I/o intensive tasks to migrate to higher and higher priority levels, whereas cpu-intensive tasks are made to seek lower priority levels.
- •Host-Target Approach
- •Preemption Point Approach
- •Self-Host Systems
- •Windows As a Real-Time Operating System
- •Figure 9: Task Priorities in Windows nt
- •Open Software
- •Genesis of posix
- •Overview of posix
- •Real-Time posix Standard
- •Rt Linux
- •7.8 Windows ce
- •Benchmarking Real-Time Systems
- •Figure 13: Task Switching Time Among Equal Priority Tasks
- •Real-Time Communication
- •Figure 2: a Bus Architecture
- •Figure 4: Logical Ring in a Token Bus
- •Soft Real-Time Communication in a lan
- •Figure 6: Priority Arbitration Example
- •Figure 8: Problem in Virtual Time Protocol
- •Figure 9: Structure of a Token in ieee 802.5
- •Figure 10: Frames in the Window-based Protocol
- •Performance Comparison
- •A Basic Service Model
- •Traffic Characterization
- •Figure 16: Constant Bit-Rato Traffic
- •Routing Algorithms
- •Resource Reservation
- •Resource Reservation Protocol (rsvp)
- •Traffic Shaping and Policing
- •Traffic Distortion
- •Traffic Scheduling Disciplines
- •Figure 20: Packet Service in Jittor-edd
- •Differentiated Services
- •Functional Elements of DiffServ Architecture
- •Real Time Databases
- •Isolation: Transactions are executed concurrently as long as they do not interfere in each other’s computations.
- •Real-Time Databases
- •Real-Time Database Application Design Issues
- •Temporal Consistency
- •Concurrency Control in Real-Time Databases
- •It can bo shown that pcp is doadlock froo and single blocking. Rocolloct that single blocking moans that once a transaction starts executing after being blocked, it may not block again.
- •Speculative Concurrency Control
- •Comparison of Concurrency Control Protocols
- •Commercial Real-Time Databases
- •Figure 16: Uniform Priority Assignment to Tasks of Example 15
- •Version 2 cse, iit Kharagpur
Figure 6: Priority Arbitration Example
Priority arbitration time is divided into fixed sized slots. The duration of each slot duration is typically made equal to end-to-end propagation delay of the medium. If the slot size is made any smaller than this, then the priority arbitration scheme would not work since a collision even when it occurs would not be detected. A slot size larger than this would lead to an increase in channel idle time during every slot. Over these slots, every node transmits the priority value of its highest priority pending message with msb first as shown in Fig. 5. Since simultaneous transmission follows or logic, a node that transmits a 0 and receives a 1, knows that there is at least one node that is having a higher priority pending message, and drops out of the contention.
To illustrate the working of this protocol, transmission of bits by different nodes in a hypothetical example during the arbitration interval has schematically been shown in the Fig. 6. In Fig. 6, three nodes N1, N2, and N3 are participating in the arbitration process. The priorities of highest messages at the nodes N1, N2, and N3 are 10, 16, and 20. As shown, node N1 drops out after transmitting the first bit as it transmits a 0 but listens a 1. Similarly, the node N2 would drop out after transmitting the third bit when it would transmit a 0 and listen to a 1. Finally, after transmitting the last bit, node N3 would conclude that it has the highest priority message and would begin its transmission.
Arbitration
Transmission
Figure
7: Priority Arbitration in Virtual Time Protocol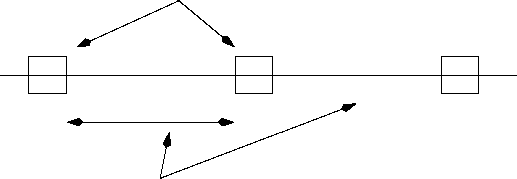
Virtual Time Protocol: In this protocol a node uses the state of the channel to reason about the pending packets residing at other nodes. Each node with a packet to send waits for an interval of time that is inversely proportional to the priority of highest priority message it has. That is the lower is the priority of a message that a node has, the more time it waits. At the expiration of the waiting time, the node senses the status of the channel. If the channel is busy, then this means that a higher priority message is being transmitted and it needs to wait until an idle period. So, if it finds that transmission is already taking place, then it waits for the next, frame, otherwise it starts to transmit.
N2
<- Propagation
Time >-![]()
N1
Figure 8: Problem in Virtual Time Protocol
What should be the difference in wait times of two nodes which have messages whose priorities differ by one? Because of the propagation delay in the network, a node can not instantaneously detect when another node starts transmission during arbitration. As a result, unless the wait time is at least as large as the propagation time, the following problem would occur. Assume that two nodes N1 and N2 have their priorities differ by one. After N1 starts transmitting, if N2 waits for any time lower than the propagation time, then it can not detect the transmission of N1 and would start transmitting. This would lead to collision and incorrect priority arbitration. This bounds the difference between the wait times of two nodes that have consecutive priorities.
5.2 IEEE 802.5:
IEEE 802.5 is a priority based token ring protocol. The header of a token contains two fields: a priority field and a mode field. In this protocol, token alternates between two modes: a reservation mode, and a free mode.
Packet
>
Payload
Header
Mode
bit
