- •Contents
- •Introductory discussion
- •1. Answer the question.
- •2. This quiz will help you "hack" terms you may encounter while surfing the Internet.
- •Topic I. Computer systems
- •1. Answer the following questions:
- •2. Match each component in column a with its function in column b:
- •3. Complete the table:
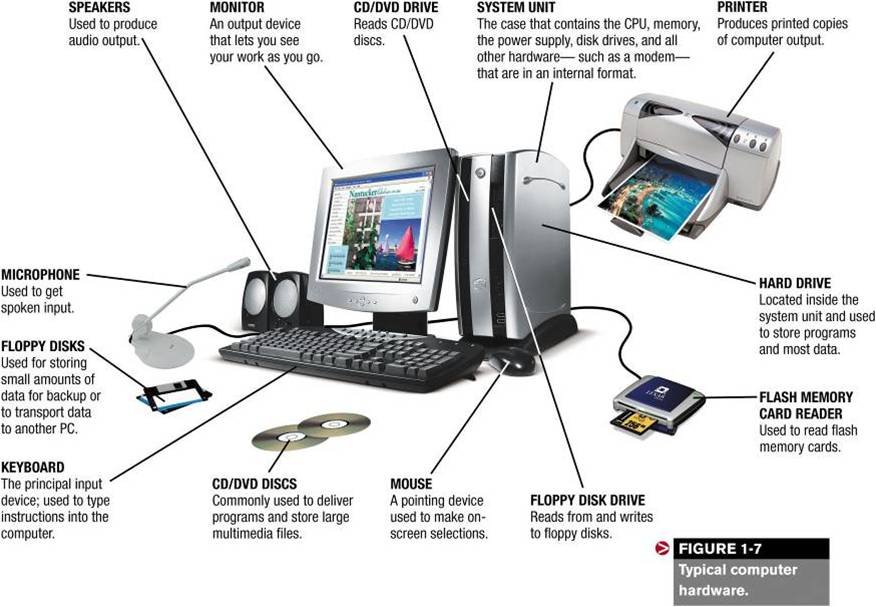
- •4. Label the diagram of a computer system using these terms:
- •Topic II. Prehistory of the computer
- •Vocabulary list
- •1. True or false?
- •Give synonyms to:
- •3. Give antonyms to:
- •Topic III. The analytical engine
- •1. Find in the text the English equivalents to:
- •Answer the following questions:
- •3. Put the proper words into sentences:
- •Topic IV. Babbage's dream comes true
- •1. Find in the text the English equivalents to:
- •2. Give synonyms to:
- •3. Give antonyms to:
- •4. Put the proper words into sentences:
- •5. Answer the following questions:
- •6. Translate into English:
- •Topic V. The early years of pc
- •Vocabulary list
- •1. Find in the text the English equivalents to:
- •2. True or false?
- •3. Give a synonym for words in parentheses;
- •5. Describe the relationship between each of the following pairs of words (antonyms, synonyms, neither):
- •6. Choose the word to complete each of the following sentences:
- •7. Cross out the one word that does not have the same meaning as the other three words:
- •8. Complete the paragraph below:
- •Topic VI. Computer crimes
- •1. Find in the text the English equivalents to:
- •2. True or false?
- •3. Give synonyms to:
- •4. Give antonyms to:
- •Topic VII. Security: playing it safe
- •Vocabulary list
- •1. Give synonyms to:
- •2. Give antonyms to:
- •3. Answer the questions:
- •4. Put the proper words into sentences:
- •Topic VIII. Checking your own security
- •1. Find in the text the English equivalents to:
- •2. Answer the following questions:
- •3. Translate into English:
- •Topic IX. Viruses and vaccines
- •Topic X. Strap on some eyephones and you are virtually there
- •Vocabulary list
- •1. True or false?
- •2. Read the words as they are used in the following sentences and try to come up with your own definition:
- •3. Put the proper words into sentences:
- •4. Guess the meaning of the italicized words:
- •Topic XI. Surfing the net
- •Vocabulary list
- •8. Put the proper words into sentences:
- •Topic XII. The language of e-mail
- •1. Answer the questions:
- •4. Discuss:
- •5. Write an e-mail message to your friend (on paper). Use an appropriate format and a chatty style. Try to use at least one smiley and some abbreviations. Topics for essays, oral or written reports
- •English computer glossary
- •Reference literature
1. Answer the questions:
What major problems are there with the e-mail? Are they opinions or facts? Would it be a problem for you?
What do you think is the reason for the various bits of netiquette which are mentioned?
Find at least 5 examples of a very colloquial and chatty style used in the text. Why are they used?
For which of the following types of writing is it necessary to be brief?
Instructions, love letters, news reports, business proposals, faxes, adverts, insurance claims, curriculum vitae, short stories, scientific reports, e-mail, poems.
Write a summary of the text. Include only the information, ignore any extra remarks. Write in a neutral rather than an informal style.
2. E-mail messages usually have the following format:
To: (Name and e-mail address of recipient) From: (Name and e-mail address of sender) Subject: (Identification of main point of message) Here is an example of an e-mail address: smith@cup.ac.uk
Note that the symbol @ in e-mail address is read at and that the full stops are read as dot. Thus the example address would be read as Smith at С - U - P dot A - С dot U - K.
The ac.uk in the example address tells you that the address is based at a university in the United Kingdom.
Do you know anyone with an e-mail address? If so, dictate it to other students in the class. If not, then your teacher will give you some addresses for dictation.
E-mailers also keep their message brief by abbreviating frequently used phrases. Complete these common phrases:
AAMOF |
as am... off... |
AFAIK |
as f... as I k... |
FYI |
for your i... |
FYA |
f... y... am... |
IMO |
in my o... |
IOW |
in o... words |
NRN . |
not r... necessary |
TTYL |
talk to у... 1... |
FAQ |
f... a... question(s) |
BTW |
by t... w... |
LOL |
la... o... loud |
KHYF |
k... ho... y... fe... |
IMHO |
in my h... o... |
WYSIWYG |
what y... see is w... y... g... |
RTFM |
read the f... m... |
4. Discuss:
Do faxes, electronic mail and papers offer an escape from human interaction?
Could all these topography symbols such as e-smiles supplant the more emotive ingredients of two-way communication?
How can we balance the use of technology and real-life conversation?
5. Write an e-mail message to your friend (on paper). Use an appropriate format and a chatty style. Try to use at least one smiley and some abbreviations. Topics for essays, oral or written reports
To be or not to be computer literate?
Pluses and minuses of computers.
How will computers affect our lives in future?
Discoveries, inventions, new products, and their effects (good and evil).
From the abacus to the computer.
The evolution of computers in terms of generations.
Computer – a God's gift or a Devil's toy?
If I were the inventor of computer ...
If there were no computers they had to be thought out.
Science fiction: serving the science.
How has the world benefited from the invention of the PC? What problems have accompanied the computer revolution?
Of all advantages that the computer has brought to the modern world, which is the most beneficial?
Describe the invention that has had the greatest effect on the 20th century.
Hackers of today.
If I were a hacker.
Hacking for fun or running for life?
Do we need hackers?
Which of user identifications is best?
Common means of protecting data:
securing waste;
separating employee functions;
implementing passwords, internal controls, audit checks.
Cryptography.
Copyprotection;
What are computer viruses and how do they differ?
What makes a perfect virus?
A day in the life of the virus hunter.
Professional ethical behavior.
Virtual reality, a reality?
Is it possible to create a perfect virtual reality?
Virtual reality as the way of exploring the world.
The perspectives of the virtual reality development.
APPENDIX A