
- •Table of Contents
- •Dedication
- •Foreword
- •Introduction
- •What Is FreeBSD?
- •How Did FreeBSD Get Here?
- •The BSD License: BSD Goes Public
- •The Birth of Modern FreeBSD
- •FreeBSD Development
- •Committers
- •Contributors
- •Users
- •Other BSDs
- •NetBSD
- •OpenBSD
- •Other UNIXes
- •Solaris
- •Linux
- •IRIX, HPUX, etc.
- •FreeBSD's Strengths
- •Portability
- •Power
- •Simplified Software Management
- •Optimized Upgrade Process
- •Filesystem
- •Who Should Use FreeBSD
- •FreeBSD as Your Desktop
- •Who Should Run Another BSD
- •Who Should Run a Proprietary Operating System
- •How to Read This Book
- •What Must You Know?
- •How to Think About UNIX
- •Channels of Communication
- •Working with Channels
- •The Command Line
- •Chapter 1: Installation
- •FreeBSD Hardware
- •Processor
- •Memory (RAM)
- •Hard Drives
- •Downloading FreeBSD
- •Installing by FTP
- •Other FTP Install Information
- •Hardware Setup
- •Actually Installing FreeBSD
- •Configuring the Kernel for ISA Cards
- •Sysinstall: The Ugly FreeBSD Installer
- •Disk Usage
- •Partitioning
- •Root
- •Swap Space
- •Swap Splitting
- •/var, /usr, and /home
- •A Second Hard Drive
- •Soft Updates
- •Block Size
- •What to Install
- •Installation Media
- •Committing
- •Root Password
- •Adding Users
- •Time Zone
- •Mouse
- •Configuring Network Cards
- •Xfree86
- •Software
- •Restart
- •A Note on Editors
- •Chapter 2: Getting More Help
- •Why Not Mail First?
- •The FreeBSD Attitude
- •Man Pages
- •The FreeBSD Manual
- •Man Page Headings
- •The FreeBSD Documentation
- •The Mailing List Archives
- •Other Web Sites
- •Checking the Handbook/FAQ
- •Checking the Man Pages
- •Checking the Mailing List Archives
- •Using Your Answer
- •Mailing for Help
- •Chapter 3: Read This Before You Break Something Else! (Backup and Recovery)
- •Overview
- •System Backups
- •Tape Devices
- •How to Read Dmesg.boot
- •Controlling Your Tape Drive
- •Device Nodes
- •Using the TAPE Variable
- •The mt Command
- •Backup Programs
- •Dump/Restore
- •Restoring from an Archive
- •Checking the Contents of an Archive
- •Extracting Data from an Archive
- •Restoring Interactively
- •Recording What Happened
- •Revision Control
- •Getting Older Versions
- •Breaking Locks
- •Viewing Log Messages
- •Reviewing a File's Revision History
- •Ident and ident Strings
- •Going Further
- •The Fixit Disk
- •Chapter 4: Kernel Games
- •Overview
- •What Is the Kernel?
- •Configuring Your Kernel
- •Sysctl
- •Changing Sysctls
- •Setting Sysctls at Boot
- •Kernel Configuration with Loader.conf
- •Manually Configuring the Loader
- •Viewing Loaded Modules
- •Loading and Unloading Modules
- •Customizing the Kernel
- •Preparation
- •Your Backup Kernel
- •Editing Kernel Files
- •Basic Options
- •Multiple Processors
- •Device Entries
- •Building Your Kernel
- •Troubleshooting Kernel Builds
- •Booting an Alternate Kernel
- •Adding to the Kernel
- •LINT
- •Fixing Errors with Options
- •Tweaking Kernel Performance
- •Sharing Kernels
- •Chapter 5: Networking
- •Overview
- •Network Layers
- •The Physical Layer
- •The Physical Protocol Layer
- •The Logical Protocol Layer
- •The Application Layer
- •The Network in Practice
- •Mbufs
- •What Is a Bit?
- •Ethernet
- •Broadcasting
- •Address Resolution
- •Hubs and Switches
- •Netmasks
- •Netmask Tricks
- •Hexadecimal Netmasks
- •Unusable IP Addresses
- •Routing
- •Network Ports
- •Connecting to an Ethernet Network
- •Multiple IP Addresses on One Interface
- •Using Netstat
- •Chapter 6: Upgrading FreeBSD
- •Overview
- •FreeBSD Versions
- •Release
- •Snapshots
- •Security Updates
- •Which Release Should You Use?
- •Upgrade Methods
- •Upgrading via Sysinstall
- •Upgrading via CVSup
- •Simplifying the CVSup Upgrade Process
- •Building a Local CVSup Server
- •Controlling Access
- •Authentication
- •Combining Authentication and Access
- •Chapter 7: Securing Your System
- •Overview
- •Who Is the Enemy?
- •Script Kiddies
- •Disaffected Users
- •Skilled Attackers
- •FreeBSD Security Announcements
- •Subscribing
- •What You'll Get
- •Installation Security Profiles
- •Moderate
- •Extreme
- •Root, Groups, and Permissions
- •The root Password
- •Groups of Users
- •Primary Group
- •Some Interesting Default Groups
- •Group Permissions
- •Changing Permissions
- •Changing File Ownership
- •Assigning Permissions
- •File Flags
- •Viewing a File's Flags
- •Setting Flags
- •Securelevels
- •Setting Securelevels
- •Which Securelevel Do You Need?
- •What Won't Securelevel and File Flags Do?
- •Living with Securelevels
- •Programs That Can Be Hacked
- •Putting It All Together
- •Chapter 8: Advanced Security Features
- •Traffic Control
- •Default Accept vs. Default Deny
- •TCP Wrappers
- •Configuring Wrappers
- •Daemon Name
- •The Client List
- •Putting It All Together
- •Packet Filtering
- •IPFilter
- •IPFW
- •Default Accept and Default Deny in Packet Filtering
- •Basic Concepts of Packet Filtering
- •Implementing IPFilter
- •Configuring Your Server to Use Jail
- •Configuring Your Kernel to Use Jail
- •Client Setup
- •Final Jail Setup
- •Starting the Jail
- •Managing Jails
- •Shutting Down a Jail
- •Monitoring System Security
- •If You're Hacked
- •Chapter 9: Too Much Information About /etc
- •Overview
- •Varieties of /etc Files
- •Default Files
- •/etc/defaults/rc.conf
- •/etc/adduser.conf
- •/etc/crontab
- •/etc/dhclient.conf
- •/etc/fstab
- •/etc/hosts.allow
- •/etc/hosts.equiv
- •/etc/hosts.lpd
- •/etc/inetd.conf
- •/etc/locate.rc
- •/etc/login.access
- •/etc/login.conf
- •Specifying Default Environment Settings
- •/etc/mail/mailer.conf
- •/etc/make.conf and /etc/defaults/make.conf
- •/etc/master.passwd
- •/etc/motd
- •/etc/mtree/*
- •/etc/namedb/*
- •/etc/newsyslog.conf
- •/etc/passwd
- •/etc/periodic.conf and /etc/defaults/periodic.conf
- •/etc/printcap
- •Working with Printcap Entries
- •/etc/profile
- •/etc/protocols
- •/etc/rc.conf and /etc/defaults/rc.conf
- •/etc/resolv.conf
- •/etc/security
- •/etc/services
- •/etc/shells
- •/etc/spwd.db
- •/etc/sysctl.conf
- •/etc/syslog.conf
- •Chapter 10: Making Your System Useful
- •Overview
- •Making Software
- •The Pain and Pleasure of Source Code
- •Debugging
- •The Ports and Packages System
- •Ports
- •Finding Software
- •Legal Restrictions
- •Using Packages
- •Installing via FTP
- •What Does a Package Install?
- •Uninstalling Packages
- •Package Information
- •Controlling Pkg_add
- •Package Problems
- •Forcing an Install
- •Using Ports
- •Installing a Port
- •Using Make Install
- •Uninstalling and Reinstalling
- •Cleaning Up with Make Clean
- •Building Packages
- •Changing the Install Path
- •Setting Make Options Permanently
- •Upgrading Ports and Packages
- •Upgrading the Ports Collection
- •Ports Collection Upgrade Issues
- •Checking Software Versions
- •Hints for Upgrading
- •Chapter 11: Advanced Software Management
- •Overview
- •Startup and Shutdown Scripts
- •Typical Startup Script
- •Using Scripts to Manage Running Programs
- •Managing Shared Libraries
- •Ldconfig
- •Running Software from the Wrong OS
- •Recompilation
- •Emulation
- •ABI Implementation
- •Foreign Software Libraries
- •Installing and Enabling Linux Mode
- •Identifying Programs
- •What Is Linux_base?
- •Adding to Linux_base
- •Configuring Linux Shared Libraries
- •Installing Extra Linux Packages as RPMs
- •What Is SMP?
- •Kernel Assumptions
- •FreeBSD 3.0 SMP
- •FreeBSD 5 SMP
- •Using SMP
- •SMP and Upgrades
- •Chapter 12: Finding Hosts With DNS
- •How DNS Works
- •Basic DNS Tools
- •The Host Command
- •Getting Detailed Information with Dig
- •Looking Up Hostnames with Dig
- •More Dig Options
- •Configuring a DNS Client: The Resolver
- •Domain or Search Keywords
- •The Nameserver List
- •DNS Information Sources
- •The Hosts File
- •The Named Daemon
- •Zone Files
- •A Real Sample Zone
- •named.conf
- •/var/named/master/absolutebsd.com
- •Making Changes Work
- •Starting Named at Boottime
- •Checking DNS
- •Named Configuration Errors
- •Named Security
- •Controlling Information Order
- •More About BIND
- •Chapter 13: Managing Small Network Services
- •Bandwidth Control
- •Configuring IPFW
- •Reviewing IPFW Rules
- •Dummynet Queues
- •Directional Traffic Shaping
- •Certificates
- •Create a Request
- •Being Your Own CA
- •Testing SSH
- •Enabling SSH
- •Basics of SSH
- •Creating Keys
- •Confirming SSH Identity
- •SSH Clients
- •Connecting via SSH
- •Configuring SSH
- •System Time
- •Setting the Time Zone
- •Network Time Protocol
- •Ntpdate
- •Ntpd
- •Inetd
- •/etc/inetd.conf
- •Configuring Programs in Inetd
- •Inetd Security
- •Starting Inetd
- •Changing Inetd's Behavior
- •Chapter 14: Email Services
- •Email Overview
- •Where FreeBSD Fits In
- •The Email Protocol
- •Email Programs
- •Who Needs Sendmail?
- •Replacing Sendmail
- •Installing Postfix
- •Pieces of Postfix
- •Configuring Postfix
- •Email Aliases
- •Email Logging
- •Virtual Domains
- •Postfix Commands
- •Finding the Correct Mail Host
- •Undeliverable Mail
- •Installing POP3
- •Testing POP3
- •POP3 Logging
- •POP3 Modes
- •Qpopper Preconfiguration Questions
- •Default Qpopper Configuration
- •APOP Setup
- •Configuring Pop3ssl
- •Qpopper Security
- •Chapter 15: Web and FTP Services
- •Overview
- •How a Web Server Works
- •The Apache Web Server
- •Apache Configuration Files
- •Configuring Apache
- •Controlling Apache
- •Virtual Hosting
- •Tweaking Virtual Hosts
- •.NET on FreeBSD
- •Installing the SSCLI
- •FTP Security
- •The FTP Client
- •The FTP Server
- •Chapter 16: Filsystems and Disks
- •Device Nodes
- •Hard Disks and Partitions
- •The /etc/fstab File
- •Disk Basics
- •The Fast File System
- •Vnodes
- •FFS Mount Types
- •FFS Mount Options
- •What's Mounted Now?
- •Dirty Disks
- •Fsck
- •Mounting and Unmounting Disks
- •Mounting Standard Filesystems
- •Mounting with Options
- •Mounting All Standard Filesystems
- •Mounting at Nonstandard Locations
- •Unmounting
- •Soft Updates
- •Enabling Soft Updates
- •IDE Write Caching and Soft Updates
- •Virtual Memory Directory Caching
- •Mounting Foreign Filesystems
- •Using Foreign Mounts
- •Foreign Filesystem Types
- •Mount Options and Foreign Filesystems
- •Filesystem Permissions
- •Removable Media and /etc/fstab
- •Creating a Floppy
- •Creating an FFS Filesystem
- •The Basics of SCSI
- •SCSI Types
- •SCSI Adapters
- •SCSI Buses
- •Termination and Cabling
- •SCSI IDs and LUNs
- •FreeBSD and SCSI
- •Wiring Down Devices
- •Adding New Hard Disks
- •Creating Slices
- •Creating Partitions
- •Configuring /etc/fstab
- •Installing Existing Files onto New Disks
- •Temporary Mounts
- •Moving Files
- •Stackable Mounts
- •Chapter 17: RAID
- •Hardware vs. Software RAID
- •RAID Levels
- •Software RAID
- •Vinum Disk Components
- •Vinum Plex Types
- •Preparing Vinum Drives
- •Dedicating Partitions to Vinum
- •Configuring Vinum
- •Concatenated Plex
- •Removing Vinum Configuration
- •Striped Volumes
- •Mirrored Volumes
- •Starting Vinum at Boot
- •Other Vinum Commands
- •Replacing a Failed Mirrored Plex
- •Chapter 18: System Performance
- •Overview
- •Computer Resources
- •Disk Input/Output
- •Network Bandwidth
- •CPU and Memory
- •Using Top
- •Memory Usage
- •Swap Space Usage
- •CPU Usage
- •When Swap Goes Bad
- •Paging
- •Swapping
- •Are You Swapping or Paging?
- •Fairness in Benchmarking
- •The Initial Test
- •Using Both CPUs
- •Directory Caching
- •Moving /usr/obj
- •Lessons Learned
- •Chapter 19: Now What's It Doing?
- •Status Mails
- •Forwarding Reports
- •Logging with Syslogd
- •Facilities
- •Levels
- •Syslog.conf
- •Wildcards
- •Rotating Logs with Newsyslog.conf
- •Reporting with SNMP
- •Basics of SNMP
- •MIBs
- •Snmpwalk
- •Specific Snmpwalk Queries
- •Translating Between Numbers and Names
- •Setting Up Snmpd
- •Index Numbers
- •Configuring MRTG
- •Sample mrtg.cfg Entry
- •Testing MRTG
- •Tracking Other System Values
- •Monitoring a Single MIB
- •Customizing MRTG
- •MRTG Index Page
- •Sample MRTG Configurations
- •Chapter 20: System Crashes and Panics
- •What Causes Panics?
- •What Does a Panic Look Like?
- •Responding to a Panic
- •Prerequisites
- •Crash Dump Process
- •The Debugging Kernel
- •kernel.debug
- •Dumpon
- •Savecore
- •Upon a Crash
- •Dumps and Bad Kernels
- •Using the Dump
- •Advanced Kernel Debugging
- •Examining Lines
- •Examining Variables
- •Apparent Gdb Weirdness
- •Results
- •Vmcore and Security
- •Symbols vs. No Symbols
- •Serial Consoles
- •Hardware Serial Console
- •Software Serial Console
- •Changing the Configuration
- •Using a Serial Console
- •Serial Login
- •Emergency Logon Setup
- •Disconnecting the Serial Console
- •Submitting a Problem Report
- •Problem Report System
- •What's in a PR?
- •Filling Out the Form
- •PR Results
- •Chapter 21: Desktop FreeBSD
- •Overview
- •Accessing File Shares
- •Prerequisites
- •Character Sets
- •Kernel Support for CIFS
- •SMB Tools
- •Configuring CIFS
- •Minimum Configuration: Name Resolution
- •Other smbutil Functions
- •Mounting a Share
- •Other mount_smbfs Options
- •Sample nsmb.conf Entries
- •CIFS File Ownership
- •Serving Windows File Shares
- •Accessing Print Servers
- •Running a Local Lpd
- •Printer Testing
- •Local Printers
- •X: A Graphic Interface
- •X Prerequisites
- •X Versions
- •Configuring X
- •Making X Look Decent
- •Desktop Applications
- •Web Browsers
- •Email Readers
- •Office Suites
- •Music
- •Graphics
- •Desk Utilities
- •Games
- •Afterword
- •Overview
- •The Community
- •What Can You Do?
- •Getting Things Done
- •Second Opinions
- •Appendix: Some Useful SYSCTL MIBs
- •List of Figures
- •Chapter 1: Installation
- •Chapter 5: Networking
- •Chapter 6: Upgrading FreeBSD
- •Chapter 19: Now What's It Doing?
- •List of Tables
- •Chapter 4: Kernel Games
- •Chapter 5: Networking
- •Chapter 8: Advanced Security Features
- •Chapter 9: Too Much Information About /etc
- •List of Sidebars
- •Chapter 15: Web and FTP Services
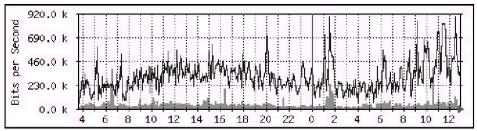
Figure 19−1: Sample MRTG graph
Get MRTG measuring traffic on one of your machines, and then we'll measure some other interesting things by choosing our SNMP MIBs.
Tracking Other System Values
By default, MRTG measures network traffic, but you can use it to measure any information available via SNMP. All you need are the MIBs for the information you want to measure. To make MRTG monitor these MIBs instead of network traffic, add them to the Target entry like so:
...............................................................................................
Target[label]:mibnumber1&mibnumber2:GetLostLoser@localhost
...............................................................................................
For example, to measure system CPU time (MIB .1.3.6.1.4.1.2021.11.9.0) and user CPU time (MIB .1.3.6.1.4.1.2021.11.10.0), use this line:
...............................................................................................
Target[cpu]:1.3.6.1.4.1.2021.11.9.0&1.3.6.1.4.1.2021.11.10.0.:GetLostLoser@localhost
...............................................................................................
Remember, MRTG charts MIBs in pairs, so pick values to monitor accordingly. Sensible choices are things like "available swap and total swap" or "system CPU usage and user CPU usage." Measuring combinations such as available swap versus the percentage of disk available would give you difficult−to−understand charts.
How do we know which MIBs to use? Well, digging through the snmpwalk output, and translating the system and user CPU times (enterprises.ucdavis.systemStats.ssCpuUser.0 and enterprises.ucdavis.systemStats.ssCpuSystem.0, respectively), we find that they translate to .1.3.6.1.4.1.2021.11.9.0 and .1.3.6.1.4.1.2021.11.10.0. You don't want to go digging through the MIB tree to find this sort of thing, however, so I'll make it a little easier for you.
Useful Net−snmp MIBs
Here are some net−snmp MIBs worth monitoring by name, with their corresponding numerical values in parentheses. All of these can be found under .1.3.6.1.4.1.2021. For example, the M e m o r y . M e m T o t a l S w a p M I B c a n b e d e t e r m i n e d b y q u e r y i n g
1.3.6.1.4.1.2021.Memory.MemTotalSwap.
Note Before using any MIB, be sure to test it at snmpwalk. Each query should return a single line. If it returns multiple lines, there's probably an index on the end of it that you should include before entering that MIB in MRTG.
445
Without further ado, here are some useful MIBs:
memory.memTotalSwap (4.3) |
The total swap on the system. Check this value |
|
before assigning limits involving swap in other |
|
MRTG graphs. |
memory.memAvailSwap (4.4) |
The amount of swap remaining. |
memory.memTotalReal (4.5) |
The total memory actually available on the system. |
|
While you don't need to monitor this value (after all, |
|
the RAM in a system rarely changes), you should |
|
check it before setting limits in MRTG. |
memory.memAvailReal (4.6) memory.memBuffer (4.14) memory.memCached (4.15) dskTable.dskEntry.dskTotal (9.1.6)
dskTable.dskEntry.dskAvail (9.1.7)
dskTable.dskEntry.dskPercent
(9.1.9) systemStats.ssCpuUser (11.9)
The amount of unused real memory.
The amount of memory in the system buffer.
The amount of memory in the system cache.
The total size of a partition. Like the other totals, this is just for reference. This MIB will almost certainly have indexes.
The amount of space remaining on the disk, in blocks.
The percentage of the disk in use.
The percentage of the CPU time spent in non−kernel programs.
systemStats.ssCpuSystem (11.10) |
The percentage of CPU time spent running the |
|
kernel. |
There are many, many more MIBs you could monitor, and entire books have been written about SNMP and monitoring. Still, these select few should cover the basic system services, and give you those important pretty pictures for your staff meeting.
Monitoring a Single MIB
Although MRTG is designed to monitor things in pairs, you can monitor a single MIB by listing it twice:
...............................................................................................
Target[localhost.memAvail]:.1.3.6.1.4.1.2021.4.6.0&.1.3.6.1.4.1.2021.4.6.0:GetLostLo
ser@localhost
...............................................................................................
This will work just fine to show only one MIB on the MRTG graph.
Note Be sure to pick a separate label for the target, and use it for all configuration statements for that target. If you don't, MRTG will either complain or overwrite the log files from other targets.
446
Customizing MRTG
Once you have a working MRTG setup, be careful testing new configurations. I generally test a new MRTG configuration in a separate WorkDir, so that any mis−configurations won't damage existing log files or production status pages.
The mrtg.cfg file contains a wide variety of options that allows you to customize almost every aspect of MRTG's appearance and functionality. Here you'll find some of the most useful MRTG configuration options, and how they can be used in production environments.
WithPeak[label]: wmy
MRTG's log format condenses older entries into average values, which tends to decrease values over time. The WithPeak option forces MRTG to keep and graph the maximum values over time. While your graphs will be more complex as a result, they will contain more useful information. This option can be set for the weekly, monthly, and yearly graphs, or a combination.
MaxBytes[label]: number
This is the maximum value that a MIB can reach. (The label is misleading if the MIB doesn't measure bytes.) MRTG uses this value to decide if it got a sensible answer from the device.
Both MIBs being measured use MaxBytes, so be sure you're measuring sensible pairs! If you're doing something particularly weird and need different MaxBytes variables, use MaxBytes1 and
MaxBytes2.
YLegend[label]: text
MRTG will put this text along the side of the graph. Put whatever you're measuring here, such as "% CPU Time".
LegendI[label] & LegendO[label]: text
MRTG always measures two MIBs. The first MIB is the traditional "In" value, and the second the "Out". You can put short descriptions of what you're measuring here to have them appear beneath the graph.
Legend1[label] & Legend2[label]: text
Legend1 is the label for the first MIB you measure; Legend2, the second. Both will appear at the bottom of your chart, in the key.
Legend3[label] & Legend4[label]: text
These labels will be used if you're recording maximums (with the WithPeak option). If you're not recording maximums, these labels will have no effect.
Directory[label]: directoryname
Large MRTG setups can generate a lot of files. The directory keyword allows you to put the files for a particular label in a subdirectory of the WorkDir.
447
Options[label]: option−names
Options allow you to handle special cases. All options are specified on one line, after the target. Some good examples follow:
growright |
By default, MRTG draws graphs from right to left. Use this option to make it draw |
|
graphs from left to right. |
bits |
This changes the graphs from measuring bytes to bits. Bits are not only more |
|
impressive, but they may also be more accurate, depending on what you're |
|
measuring. For example, many people measure bandwidth in bits, not kilobytes. |
gauge |
SNMP generally retains information in counter form. MRTG subtracts the previous |
|
reading from the current reading to get the change in the last five minutes. Use the |
|
gauge option for SNMP MIBs that don't change, such as disk capacity. |
unknaszero When a target is not reachable for any reason (including power failure or network problems), the system will assume the last known value for the charts. Whether or not this is more accurate is a matter of some controversy. This option causes MRTG to assume a value of zero when it cannot reach a target.
MRTG Index Page
The last bit of configuration we'll need to do is to create a single HTML index page for our MRTG setup. MRTG includes an indexmaker tool that automagically does this for us. Just run this:
...............................................................................................
# indexmaker mrtg.cfg > index.html
...............................................................................................
You'll probably want to edit this, but it's a nice starting place.
Sample MRTG Configurations
This section contains some sample MRTG configurations. To use them, insert the correct hostname and community name. Also, note that the Target statements are supposed to be all on one line; the printed page simply isn't wide enough to handle this at a type size you can see without a magnifying glass. In each example, you will need to edit the Target statement to give the proper hostname and community name, and you'll probably want to edit the PageTop setting so your graph displays the correct information for your host.
User and System CPU Usage
This first sample compares user CPU usage with system CPU usage as percentages. (Note that we use the gauge option.)
...............................................................................................
Title[myhost.AbsoluteBSD.com.cpu]: myhost.AbsoluteBSD.com CPU usage YLegend[myhost.AbsoluteBSD.com.cpu]: CPU usage WithPeak[myhost.AbsoluteBSD.com.cpu]: wmy MaxBytes[myhost.AbsoluteBSD.com.cpu]: 100
Target[myhost.AbsoluteBSD.com.cpu]:.1.3.6.1.4.1.2021.11.9.0&.1.3.6.1.4.1.2021.11.10.
0:public@myhost.AbsoluteBSD.com ShortLegend[myhost.AbsoluteBSD.com.cpu]: CPU LegendI[myhost.AbsoluteBSD.com.cpu]: User CPU
448
LegendO[myhost.AbsoluteBSD.com.cpu]: System CPU Legend1[myhost.AbsoluteBSD.com.cpu]: User Processor Usage Legend2[myhost.AbsoluteBSD.com.cpu]: System Processor Usage Legend3[myhost.AbsoluteBSD.com.cpu]: Maximal 5 Minute User Processor Usage Legend4[myhost.AbsoluteBSD.com.cpu]: Maximal 5 Minute System Processor Usage Options[myhost.AbsoluteBSD.com.cpu]: growright, gauge PageTop[myhost.AbsoluteBSD.com.cpu]: <H1>CPU usage for myhost.AbsoluteBSD.com </H1>
...............................................................................................
Swap Usage
Before you can measure swap space, you'll need to know how much swap your system has. You can get that information by doing an snmpwalk to get the total swap available, or snmpwalk hostname community .1.3.6.1.4.1.2021.4.3. Put that value in the MaxBytes space, and under the PageTop, so it will show up on your graph.
...............................................................................................
Title[myhost.AbsoluteBSD.com.swap]: myhost.AbsoluteBSD.com Available Swap YLegend[myhost.AbsoluteBSD.com.swap]: swap WithPeak[myhost.AbsoluteBSD.com.swap]: wmy MaxBytes[myhost.AbsoluteBSD.com.swap]: 128000 Target[myhost.AbsoluteBSD.com.swap]:
.1.3.6.1.4.1.2021.4.4.0&.1.3.6.1.4.1.2021.4.4.0:public@myhost.AbsoluteBSD.com ShortLegend[myhost.AbsoluteBSD.com.swap]: Swap LegendI[myhost.AbsoluteBSD.com.swap]: Available Swap LegendO[myhost.AbsoluteBSD.com.swap]: Available Swap Legend1[myhost.AbsoluteBSD.com.swap]: Available Swap Legend2[myhost.AbsoluteBSD.com.swap]: Available Swap Legend3[myhost.AbsoluteBSD.com.swap]: Maximal 5 Minute Available Swap Legend4[myhost.AbsoluteBSD.com.swap]: Maximal 5 Minute Available Swap Options[myhost.AbsoluteBSD.com.swap]: growright, gauge PageTop[myhost.AbsoluteBSD.com.swap]: <H1>Available Swap (out of 128M) for myhost.AbsoluteBSD.com </H1>
...............................................................................................
Disk Partition
Measuring the amount of space used on a disk partition is similarly easy, though you'll need to know the MIB index for the disk partition first. (See the examples in "Index Numbers" earlier in this chapter.) Be sure to give the correct size in the PageTop space.
...............................................................................................
Target[myhost.AbsoluteBSD.com.root]:.1.3.6.1.4.1.2021.9.1.9.1&.1.3.6.1.4.1.2021.9.1.
9.1:public@myhost.AbsoluteBSD.com
Title[myhost.AbsoluteBSD.com.root]: Myhost.AbsoluteBSD.com Root partition % used MaxBytes[myhost.AbsoluteBSD.com.root]: 100 WithPeak[myhost.AbsoluteBSD.com.root]: wmy Suppress[myhost.AbsoluteBSD.com.root]: y
LegendI[myhost.AbsoluteBSD.com.root]: % used Legend1[myhost.AbsoluteBSD.com.root]: % used YLegend[myhost.AbsoluteBSD.com.root]: percent used ShortLegend[myhost.AbsoluteBSD.com.root]: used Options[myhost.AbsoluteBSD.com.root]: gauge, growright PageTop[myhost.AbsoluteBSD.com.root]: <H1>myhost Root partition (% of 128M) used </H1>
449
...............................................................................................
Network Traffic
Just for completeness, let's look at a sample of how to measure network traffic. This assumes a 10Mbps network connection; if you're using 100BaseT, multiply MaxBytes by 10.
...............................................................................................
Title[myhost.AbsoluteBSD.com.traffic]: myhost.AbsoluteBSD.com network traffic MaxBytes[myhost.AbsoluteBSD.com.traffic]: 125000 WithPeak[myhost.AbsoluteBSD.com.traffic]: wmy Target[myhost.AbsoluteBSD.com.traffic]: public@myhost.AbsoluteBSD.com Options[myhost.AbsoluteBSD.com.traffic]: growright, bits PageTop[myhost.AbsoluteBSD.com.traffic]: <H1>Network traffic on myhost.AbsoluteBSD.com </H1>
...............................................................................................
Monitoring Non−BSD Systems
MRTG can monitor any system that uses SNMP; it is a standard spoken by almost every network−equipment and operating−system vendor. To do so, all you need is the list of MIBs that the product supports and what they mean. Tables of MIB interpretations—simple text files containing tables of how to read the vendor's MIB tree–are generally available from vendors. Each file starts something like this:
...............................................................................................
IPV6−MIB DEFINITIONS ::= BEGIN
IMPORTS
MODULE−IDENTITY, OBJECT−TYPE, NOTIFICATION−TYPE, mib−2, Counter32, Unsigned32, Integer32,
Gauge32 |
FROM SNMPv2−SMI |
DisplayString, PhysAddress, TruthValue, TimeStamp, |
|
VariablePointer, RowPointer |
FROM SNMPv2−TC |
MODULE−COMPLIANCE, OBJECT−GROUP, |
|
NOTIFICATION−GROUP |
FROM SNMPv2−CONF |
Ipv6IfIndex, Ipv6Address, Ipv6AddressPrefix, |
|
Ipv6AddressIfIdentifier, |
|
Ipv6IfIndexOrZero |
FROM IPV6−TC; |
...............................................................................................
Copy these definition files to a directory on your system. Next, set the environment variable MIBDIRS to point to that directory, and snmptranslate will recognize them.
You can even install SNMP on your NT systems; this makes them easy to monitor, at a fraction of the cost of commercial systems. The only difference between MRTG and a commercial system is that you must know what you're doing to use MRTG. I highly recommend Garth Williams’ "SNMP for the Public Community" site (http://www.wtcs.org/snmp4tpc/) for SNMP on other platforms. Be warned in advance: To call Microsoft's implementation of SNMP "skeletal" would leave you without an adequate description of its error messages. Windows 2000 and XP are better than NT, but not
450

by a huge amount.
451
