
- •Acknowledgments
- •About the Authors
- •About the Technical Editors
- •Contents at a Glance
- •Contents
- •Foreword
- •Introduction
- •Overview of the CISSP Exam
- •The Elements of This Study Guide
- •Study Guide Exam Objectives
- •Objective Map
- •Reader Support for This Book
- •Security 101
- •Confidentiality
- •Integrity
- •Availability
- •Protection Mechanisms
- •Security Boundaries
- •Third-Party Governance
- •Documentation Review
- •Manage the Security Function
- •Alignment of Security Function to Business Strategy, Goals, Mission, and Objectives
- •Organizational Processes
- •Organizational Roles and Responsibilities
- •Security Control Frameworks
- •Due Diligence and Due Care
- •Security Policy, Standards, Procedures, and Guidelines
- •Security Policies
- •Security Standards, Baselines, and Guidelines
- •Security Procedures
- •Threat Modeling
- •Identifying Threats
- •Determining and Diagramming Potential Attacks
- •Performing Reduction Analysis
- •Prioritization and Response
- •Supply Chain Risk Management
- •Summary
- •Exam Essentials
- •Written Lab
- •Review Questions
- •Job Descriptions and Responsibilities
- •Candidate Screening and Hiring
- •Onboarding: Employment Agreements and Policies
- •Employee Oversight
- •Compliance Policy Requirements
- •Privacy Policy Requirements
- •Understand and Apply Risk Management Concepts
- •Risk Terminology and Concepts
- •Asset Valuation
- •Identify Threats and Vulnerabilities
- •Risk Assessment/Analysis
- •Risk Responses
- •Cost vs. Benefit of Security Controls
- •Countermeasure Selection and Implementation
- •Applicable Types of Controls
- •Security Control Assessment
- •Monitoring and Measurement
- •Risk Reporting and Documentation
- •Continuous Improvement
- •Risk Frameworks
- •Social Engineering
- •Social Engineering Principles
- •Eliciting Information
- •Prepending
- •Phishing
- •Spear Phishing
- •Whaling
- •Smishing
- •Vishing
- •Spam
- •Shoulder Surfing
- •Invoice Scams
- •Hoax
- •Impersonation and Masquerading
- •Tailgating and Piggybacking
- •Dumpster Diving
- •Identity Fraud
- •Typo Squatting
- •Influence Campaigns
- •Awareness
- •Training
- •Education
- •Improvements
- •Effectiveness Evaluation
- •Summary
- •Exam Essentials
- •Written Lab
- •Review Questions
- •Planning for Business Continuity
- •Project Scope and Planning
- •Organizational Review
- •BCP Team Selection
- •Resource Requirements
- •Legal and Regulatory Requirements
- •Business Impact Analysis
- •Identifying Priorities
- •Risk Identification
- •Likelihood Assessment
- •Impact Analysis
- •Resource Prioritization
- •Continuity Planning
- •Strategy Development
- •Provisions and Processes
- •Plan Approval and Implementation
- •Plan Approval
- •Plan Implementation
- •Training and Education
- •BCP Documentation
- •Summary
- •Exam Essentials
- •Written Lab
- •Review Questions
- •Categories of Laws
- •Criminal Law
- •Civil Law
- •Administrative Law
- •Laws
- •Computer Crime
- •Intellectual Property (IP)
- •Licensing
- •Import/Export
- •Privacy
- •State Privacy Laws
- •Compliance
- •Contracting and Procurement
- •Summary
- •Exam Essentials
- •Written Lab
- •Review Questions
- •Defining Sensitive Data
- •Defining Data Classifications
- •Defining Asset Classifications
- •Understanding Data States
- •Determining Compliance Requirements
- •Determining Data Security Controls
- •Data Maintenance
- •Data Loss Prevention
- •Marking Sensitive Data and Assets
- •Handling Sensitive Information and Assets
- •Data Collection Limitation
- •Data Location
- •Storing Sensitive Data
- •Data Destruction
- •Ensuring Appropriate Data and Asset Retention
- •Data Protection Methods
- •Digital Rights Management
- •Cloud Access Security Broker
- •Pseudonymization
- •Tokenization
- •Anonymization
- •Understanding Data Roles
- •Data Owners
- •Asset Owners
- •Business/Mission Owners
- •Data Processors and Data Controllers
- •Data Custodians
- •Administrators
- •Users and Subjects
- •Using Security Baselines
- •Comparing Tailoring and Scoping
- •Standards Selection
- •Summary
- •Exam Essentials
- •Written Lab
- •Review Questions
- •Cryptographic Foundations
- •Goals of Cryptography
- •Cryptography Concepts
- •Cryptographic Mathematics
- •Ciphers
- •Modern Cryptography
- •Cryptographic Keys
- •Symmetric Key Algorithms
- •Asymmetric Key Algorithms
- •Hashing Algorithms
- •Symmetric Cryptography
- •Cryptographic Modes of Operation
- •Data Encryption Standard
- •Triple DES
- •International Data Encryption Algorithm
- •Blowfish
- •Skipjack
- •Rivest Ciphers
- •Advanced Encryption Standard
- •CAST
- •Comparison of Symmetric Encryption Algorithms
- •Symmetric Key Management
- •Cryptographic Lifecycle
- •Summary
- •Exam Essentials
- •Written Lab
- •Review Questions
- •Asymmetric Cryptography
- •Public and Private Keys
- •ElGamal
- •Elliptic Curve
- •Diffie–Hellman Key Exchange
- •Quantum Cryptography
- •Hash Functions
- •RIPEMD
- •Comparison of Hash Algorithm Value Lengths
- •Digital Signatures
- •HMAC
- •Digital Signature Standard
- •Public Key Infrastructure
- •Certificates
- •Certificate Authorities
- •Certificate Lifecycle
- •Certificate Formats
- •Asymmetric Key Management
- •Hybrid Cryptography
- •Applied Cryptography
- •Portable Devices
- •Web Applications
- •Steganography and Watermarking
- •Networking
- •Emerging Applications
- •Cryptographic Attacks
- •Salting Saves Passwords
- •Ultra vs. Enigma
- •Summary
- •Exam Essentials
- •Written Lab
- •Review Questions
- •Secure Design Principles
- •Objects and Subjects
- •Closed and Open Systems
- •Secure Defaults
- •Fail Securely
- •Keep It Simple
- •Zero Trust
- •Privacy by Design
- •Trust but Verify
- •Techniques for Ensuring CIA
- •Confinement
- •Bounds
- •Isolation
- •Access Controls
- •Trust and Assurance
- •Trusted Computing Base
- •State Machine Model
- •Information Flow Model
- •Noninterference Model
- •Take-Grant Model
- •Access Control Matrix
- •Bell–LaPadula Model
- •Biba Model
- •Clark–Wilson Model
- •Brewer and Nash Model
- •Goguen–Meseguer Model
- •Sutherland Model
- •Graham–Denning Model
- •Harrison–Ruzzo–Ullman Model
- •Select Controls Based on Systems Security Requirements
- •Common Criteria
- •Authorization to Operate
- •Understand Security Capabilities of Information Systems
- •Memory Protection
- •Virtualization
- •Trusted Platform Module
- •Interfaces
- •Fault Tolerance
- •Encryption/Decryption
- •Summary
- •Exam Essentials
- •Written Lab
- •Review Questions
- •Shared Responsibility
- •Hardware
- •Firmware
- •Client-Based Systems
- •Mobile Code
- •Local Caches
- •Server-Based Systems
- •Large-Scale Parallel Data Systems
- •Grid Computing
- •Peer to Peer
- •Industrial Control Systems
- •Distributed Systems
- •Internet of Things
- •Edge and Fog Computing
- •Static Systems
- •Network-Enabled Devices
- •Cyber-Physical Systems
- •Elements Related to Embedded and Static Systems
- •Security Concerns of Embedded and Static Systems
- •Specialized Devices
- •Microservices
- •Infrastructure as Code
- •Virtualized Systems
- •Virtual Software
- •Virtualized Networking
- •Software-Defined Everything
- •Virtualization Security Management
- •Containerization
- •Serverless Architecture
- •Mobile Devices
- •Mobile Device Security Features
- •Mobile Device Deployment Policies
- •Process Isolation
- •Hardware Segmentation
- •System Security Policy
- •Covert Channels
- •Attacks Based on Design or Coding Flaws
- •Rootkits
- •Incremental Attacks
- •Summary
- •Exam Essentials
- •Written Lab
- •Review Questions
- •Apply Security Principles to Site and Facility Design
- •Secure Facility Plan
- •Site Selection
- •Facility Design
- •Equipment Failure
- •Wiring Closets
- •Server Rooms/Data Centers
- •Intrusion Detection Systems
- •Cameras
- •Access Abuses
- •Media Storage Facilities
- •Evidence Storage
- •Restricted and Work Area Security
- •Utility Considerations
- •Fire Prevention, Detection, and Suppression
- •Perimeter Security Controls
- •Internal Security Controls
- •Key Performance Indicators of Physical Security
- •Summary
- •Exam Essentials
- •Written Lab
- •Review Questions
- •OSI Model
- •History of the OSI Model
- •OSI Functionality
- •Encapsulation/Deencapsulation
- •OSI Layers
- •TCP/IP Model
- •Common Application Layer Protocols
- •SNMPv3
- •Transport Layer Protocols
- •Domain Name System
- •DNS Poisoning
- •Domain Hijacking
- •Internet Protocol (IP) Networking
- •IP Classes
- •ICMP
- •IGMP
- •ARP Concerns
- •Secure Communication Protocols
- •Implications of Multilayer Protocols
- •Converged Protocols
- •Voice over Internet Protocol (VoIP)
- •Software-Defined Networking
- •Microsegmentation
- •Wireless Networks
- •Securing the SSID
- •Wireless Channels
- •Conducting a Site Survey
- •Wireless Security
- •Wi-Fi Protected Setup (WPS)
- •Wireless MAC Filter
- •Wireless Antenna Management
- •Using Captive Portals
- •General Wi-Fi Security Procedure
- •Wireless Communications
- •Wireless Attacks
- •Other Communication Protocols
- •Cellular Networks
- •Content Distribution Networks (CDNs)
- •Secure Network Components
- •Secure Operation of Hardware
- •Common Network Equipment
- •Network Access Control
- •Firewalls
- •Endpoint Security
- •Transmission Media
- •Network Topologies
- •Ethernet
- •Sub-Technologies
- •Summary
- •Exam Essentials
- •Written Lab
- •Review Questions
- •Protocol Security Mechanisms
- •Authentication Protocols
- •Port Security
- •Quality of Service (QoS)
- •Secure Voice Communications
- •Voice over Internet Protocol (VoIP)
- •Vishing and Phreaking
- •PBX Fraud and Abuse
- •Remote Access Security Management
- •Remote Connection Security
- •Plan a Remote Access Security Policy
- •Multimedia Collaboration
- •Remote Meeting
- •Instant Messaging and Chat
- •Load Balancing
- •Virtual IPs and Load Persistence
- •Active-Active vs. Active-Passive
- •Manage Email Security
- •Email Security Goals
- •Understand Email Security Issues
- •Email Security Solutions
- •Virtual Private Network
- •Tunneling
- •How VPNs Work
- •Always-On
- •Common VPN Protocols
- •Switching and Virtual LANs
- •Switch Eavesdropping
- •Private IP Addresses
- •Stateful NAT
- •Automatic Private IP Addressing
- •Third-Party Connectivity
- •Circuit Switching
- •Packet Switching
- •Virtual Circuits
- •Fiber-Optic Links
- •Security Control Characteristics
- •Transparency
- •Transmission Management Mechanisms
- •Prevent or Mitigate Network Attacks
- •Eavesdropping
- •Modification Attacks
- •Summary
- •Exam Essentials
- •Written Lab
- •Review Questions
- •Controlling Access to Assets
- •Controlling Physical and Logical Access
- •The CIA Triad and Access Controls
- •Managing Identification and Authentication
- •Comparing Subjects and Objects
- •Registration, Proofing, and Establishment of Identity
- •Authorization and Accountability
- •Authentication Factors Overview
- •Something You Know
- •Something You Have
- •Something You Are
- •Multifactor Authentication (MFA)
- •Two-Factor Authentication with Authenticator Apps
- •Passwordless Authentication
- •Device Authentication
- •Service Authentication
- •Mutual Authentication
- •Implementing Identity Management
- •Single Sign-On
- •SSO and Federated Identities
- •Credential Management Systems
- •Credential Manager Apps
- •Scripted Access
- •Session Management
- •Provisioning and Onboarding
- •Deprovisioning and Offboarding
- •Defining New Roles
- •Account Maintenance
- •Account Access Review
- •Summary
- •Exam Essentials
- •Written Lab
- •Review Questions
- •Comparing Access Control Models
- •Comparing Permissions, Rights, and Privileges
- •Understanding Authorization Mechanisms
- •Defining Requirements with a Security Policy
- •Introducing Access Control Models
- •Discretionary Access Control
- •Nondiscretionary Access Control
- •Implementing Authentication Systems
- •Implementing SSO on the Internet
- •Implementing SSO on Internal Networks
- •Understanding Access Control Attacks
- •Crackers, Hackers, and Attackers
- •Risk Elements
- •Common Access Control Attacks
- •Core Protection Methods
- •Summary
- •Exam Essentials
- •Written Lab
- •Review Questions
- •Security Testing
- •Security Assessments
- •Security Audits
- •Performing Vulnerability Assessments
- •Describing Vulnerabilities
- •Vulnerability Scans
- •Penetration Testing
- •Compliance Checks
- •Code Review and Testing
- •Interface Testing
- •Misuse Case Testing
- •Test Coverage Analysis
- •Website Monitoring
- •Implementing Security Management Processes
- •Log Reviews
- •Account Management
- •Disaster Recovery and Business Continuity
- •Training and Awareness
- •Key Performance and Risk Indicators
- •Summary
- •Exam Essentials
- •Written Lab
- •Review Questions
- •Need to Know and Least Privilege
- •Separation of Duties (SoD) and Responsibilities
- •Two-Person Control
- •Job Rotation
- •Mandatory Vacations
- •Privileged Account Management
- •Service Level Agreements (SLAs)
- •Addressing Personnel Safety and Security
- •Duress
- •Travel
- •Emergency Management
- •Security Training and Awareness
- •Provision Resources Securely
- •Information and Asset Ownership
- •Asset Management
- •Apply Resource Protection
- •Media Management
- •Media Protection Techniques
- •Managed Services in the Cloud
- •Shared Responsibility with Cloud Service Models
- •Scalability and Elasticity
- •Provisioning
- •Baselining
- •Using Images for Baselining
- •Automation
- •Managing Change
- •Change Management
- •Versioning
- •Configuration Documentation
- •Managing Patches and Reducing Vulnerabilities
- •Systems to Manage
- •Patch Management
- •Vulnerability Management
- •Vulnerability Scans
- •Common Vulnerabilities and Exposures
- •Summary
- •Exam Essentials
- •Written Lab
- •Review Questions
- •Conducting Incident Management
- •Defining an Incident
- •Incident Management Steps
- •Basic Preventive Measures
- •Understanding Attacks
- •Intrusion Detection and Prevention Systems
- •Specific Preventive Measures
- •Logging and Monitoring
- •The Role of Monitoring
- •Log Management
- •Egress Monitoring
- •Automating Incident Response
- •Understanding SOAR
- •Threat Intelligence
- •Summary
- •Exam Essentials
- •Written Lab
- •Review Questions
- •The Nature of Disaster
- •Natural Disasters
- •Human-Made Disasters
- •Protecting Hard Drives
- •Protecting Servers
- •Protecting Power Sources
- •Trusted Recovery
- •Quality of Service
- •Recovery Strategy
- •Business Unit and Functional Priorities
- •Crisis Management
- •Emergency Communications
- •Workgroup Recovery
- •Alternate Processing Sites
- •Database Recovery
- •Recovery Plan Development
- •Emergency Response
- •Personnel and Communications
- •Assessment
- •Backups and Off-site Storage
- •Software Escrow Arrangements
- •Utilities
- •Logistics and Supplies
- •Recovery vs. Restoration
- •Testing and Maintenance
- •Structured Walk-Through
- •Simulation Test
- •Parallel Test
- •Lessons Learned
- •Maintenance
- •Summary
- •Exam Essentials
- •Written Lab
- •Review Questions
- •Investigations
- •Investigation Types
- •Evidence
- •Investigation Process
- •Major Categories of Computer Crime
- •Military and Intelligence Attacks
- •Business Attacks
- •Financial Attacks
- •Terrorist Attacks
- •Grudge Attacks
- •Thrill Attacks
- •Hacktivists
- •Ethics
- •Organizational Code of Ethics
- •(ISC)2 Code of Ethics
- •Ethics and the Internet
- •Summary
- •Exam Essentials
- •Written Lab
- •Review Questions
- •Software Development
- •Systems Development Lifecycle
- •Lifecycle Models
- •Gantt Charts and PERT
- •Change and Configuration Management
- •The DevOps Approach
- •Application Programming Interfaces
- •Software Testing
- •Code Repositories
- •Service-Level Agreements
- •Third-Party Software Acquisition
- •Establishing Databases and Data Warehousing
- •Database Management System Architecture
- •Database Transactions
- •Security for Multilevel Databases
- •Open Database Connectivity
- •NoSQL
- •Expert Systems
- •Machine Learning
- •Neural Networks
- •Summary
- •Exam Essentials
- •Written Lab
- •Review Questions
- •Malware
- •Sources of Malicious Code
- •Viruses
- •Logic Bombs
- •Trojan Horses
- •Worms
- •Spyware and Adware
- •Ransomware
- •Malicious Scripts
- •Zero-Day Attacks
- •Malware Prevention
- •Platforms Vulnerable to Malware
- •Antimalware Software
- •Integrity Monitoring
- •Advanced Threat Protection
- •Application Attacks
- •Buffer Overflows
- •Time of Check to Time of Use
- •Backdoors
- •Privilege Escalation and Rootkits
- •Injection Vulnerabilities
- •SQL Injection Attacks
- •Code Injection Attacks
- •Command Injection Attacks
- •Exploiting Authorization Vulnerabilities
- •Insecure Direct Object References
- •Directory Traversal
- •File Inclusion
- •Request Forgery
- •Session Hijacking
- •Application Security Controls
- •Input Validation
- •Web Application Firewalls
- •Database Security
- •Code Security
- •Secure Coding Practices
- •Source Code Comments
- •Error Handling
- •Hard-Coded Credentials
- •Memory Management
- •Summary
- •Exam Essentials
- •Written Lab
- •Review Questions
- •Chapter 2: Personnel Security and Risk Management Concepts
- •Chapter 3: Business Continuity Planning
- •Chapter 4: Laws, Regulations, and Compliance
- •Chapter 5: Protecting Security of Assets
- •Chapter 10: Physical Security Requirements
- •Chapter 11: Secure Network Architecture and Components
- •Chapter 12: Secure Communications and Network Attacks
- •Chapter 17: Preventing and Responding to Incidents
- •Chapter 18: Disaster Recovery Planning
- •Chapter 19: Investigations and Ethics
- •Chapter 20: Software Development Security
- •Chapter 21: Malicious Code and Application Attacks
- •Chapter 3: Business Continuity Planning
- •Chapter 5: Protecting Security of Assets
- •Chapter 6: Cryptography and Symmetric Key Algorithms
- •Chapter 12: Secure Communications and Network Attacks
- •Chapter 15: Security Assessment and Testing
- •Chapter 17: Preventing and Responding to Incidents
- •Chapter 18: Disaster Recovery Planning
- •Chapter 19: Investigations and Ethics
- •Chapter 21: Malicious Code and Application Attacks
- •Index
26 Chapter 1 ■ Security GovernanceThrough Principles and Policies
Threat Modeling
Threat modeling is the security process where potential threats are identified, categorized, and analyzed. Threat modeling can be performed as a proactive measure during design and development or as a reactive measure once a product has been deployed. In either case, the process identifies the potential harm, the probability of occurrence, the priority of concern, and the means to eradicate or reduce the threat.
Threat modeling isn’t meant to be a single event. Instead, it’s meant to be initiated early in the design process of a system and continue throughout its lifecycle. For example, Microsoft uses a Security Development Lifecycle (SDL) (www.microsoft.com/en-us/securityengi- neering/sdl) with the motto of “Secure by Design, Secure by Default, Secure in Deployment and Communication” (also known as SD3+C). It has two goals in mind with this process:
■■To reduce the number of security-related design and coding defects
■■To reduce the severity of any remaining defects
A defensive approach to threat modeling takes place during the early stages of systems development, specifically during initial design and specifications establishment. This method is based on predicting threats and designing in specific defenses during the coding and crafting process. In most cases, integrated security solutions are more cost-effective and more successful than those shoehorned in later. While not a formal term, this concept could be considered a proactive approach to threat management.
Unfortunately, not all threats can be predicted during the design phase, so a reactive approach to threat management is still needed to address unforeseen issues. This concept is often call threat hunting or may be referred to as an adversarial approach.
An adversarial approach to threat modeling takes place after a product has been created and deployed.This deployment could be in a test or laboratory environment or to the general marketplace.This technique of threat hunting is the core concept behind ethical hacking, penetration testing, source code review, and fuzz testing. Although these processes are often useful in finding flaws and threats, they unfortunately result in additional effort in coding to add in new countermeasures, typically released as patches.This results in less effective security improvements (over defensive threat modeling) at the cost of potentially reducing functionality and user-friendliness.
Fuzz testing is a specialized dynamic testing technique that provides many different types of input to software to stress its limits and find previously undetected flaws. See Chapter 15
for more on fuzz testing.
Identifying Threats
There’s an almost infinite possibility of threats, so it’s important to use a structured approach to accurately identify relevant threats. For example, some organizations use one or more of the following three approaches:
Threat Modeling |
27 |
Focused on Assets This method uses asset valuation results and attempts to identify threats to the valuable assets.
Focused on Attackers Some organizations are able to identify potential attackers and can identify the threats they represent based on the attacker’s motivations, goals, or tactics, techniques, and procedures (TTPs).
Focused on Software If an organization develops software, it can consider potential threats against the software.
It’s common to pair threats with vulnerabilities to identify threats that can exploit assets and represent significant risks to the organization. An ultimate goal of threat modeling is to prioritize the potential threats against an organization’s valuable assets.
When attempting to inventory and categorize threats, it is often helpful to use a guide or reference. Microsoft developed a threat categorization scheme known as the STRIDE threat model. STRIDE is an acronym standing for the following:
■■Spoofing: An attack with the goal of gaining access to a target system through the use of a falsified identity. When an attacker spoofs their identity as a valid or authorized entity, they are often able to bypass filters and blockades against unauthorized access.
■■Tampering: Any action resulting in unauthorized changes or manipulation of data, whether in transit or in storage.
■■Repudiation: The ability of a user or attacker to deny having performed an action or activity by maintaining plausible deniability. Repudiation attacks can also result in innocent third parties being blamed for security violations.
■■Information disclosure: The revelation or distribution of private, confidential, or controlled information to external or unauthorized entities.
■■Denial of service (DoS): An attack that attempts to prevent authorized use of a resource. This can be done through flaw exploitation, connection overloading, or traffic flooding.
■■Elevation of privilege: An attack where a limited user account is transformed into an account with greater privileges, powers, and access.
Process for Attack Simulation and Threat Analysis (PASTA) is a seven-stage threat modeling methodology. PASTA is a risk-centric approach that aims at selecting or developing countermeasures in relation to the value of the assets to be protected. The following are the seven steps of PASTA:
■■Stage I: Definition of the Objectives (DO) for the Analysis of Risks
■■Stage II: Definition of the Technical Scope (DTS)
■■Stage III: Application Decomposition and Analysis (ADA)
■■Stage IV: Threat Analysis (TA)
■■Stage V: Weakness and Vulnerability Analysis (WVA)
■■Stage VI: Attack Modeling & Simulation (AMS)
■■Stage VII: Risk Analysis & Management (RAM)
Each stage of PASTA has a specific list of objectives to achieve and deliverables to produce in order to complete the stage. For more information on PASTA, please see Risk Centric

28 Chapter 1 ■ Security GovernanceThrough Principles and Policies
Threat Modeling: Process for Attack Simulation and Threat Analysis (Wiley, 2015), by Tony UcedaVelez and Marco M. Morana.
Visual, Agile, and Simple Threat (VAST) is a threat modeling concept that integrates threat and risk management into an Agile programming environment on a scalable basis (see Chapter 20, “Software Development Security,” regarding Agile).
These are just a few in the vast array of threat modeling concepts and methodologies available from community groups, commercial entities, government agencies, and international associations.
Be Alert for IndividualThreats
Competition is often a key part of business growth, but overly adversarial competition can increase the threat level from individuals. In addition to criminal hackers and disgruntled employees, adversaries, contractors, employees, and even trusted partners can be a threat to an organization if relationships go sour.
Potential threats to your business are broad and varied. A company faces threats from nature, technology, and people. Always consider the best and worst possible outcomes of your organization’s activities, decisions, and interactions. Identifying threats is the first step toward designing defenses to help reduce or eliminate downtime, compromise, and loss.
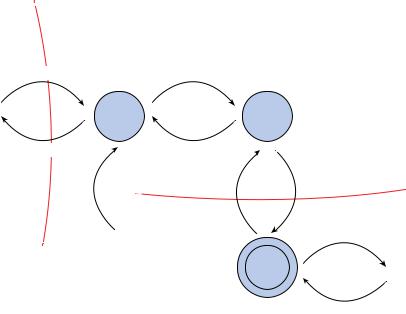
Determining and Diagramming Potential Attacks
The next step in threat modeling is to determine the potential attack concepts that could be realized. This is often accomplished through the creation of a diagram of the elements involved in a transaction along with indications of data flow and privilege boundaries (Figure 1.4). This image shows each major component of a system, the boundaries between security zones, and the potential flow or movement of information and data.
This is a high-level overview and not a detailed evaluation of the coding logic. However, for more complex systems, multiple diagrams may need to be created at various focus points and at varying levels of detail magnification.
Once a diagram has been crafted, identify all of the technologies involved. Next, identify attacks that could be targeted at each element of the diagram. Keep in mind that all forms of attacks should be considered, including logical/technical, physical, and social. This process will quickly lead you into the next phase of threat modeling: reduction analysis.
Performing Reduction Analysis
The next step in threat modeling is to perform reduction analysis. Reduction analysis is also known as decomposing the application, system, or environment. The purpose of this task is
|
|
|
|
|
|
|
|
Threat Modeling |
29 |
||
FIGURE 1. 4 An example of diagramming to reveal threat concerns |
|
|
|||||||||
|
|
|
User/Web Server |
|
|
|
|
|
|
||
|
|
|
Boundary |
|
|
|
|
|
|
|
|
|
Login |
Request |
|
Authenticate User |
|
|
|
|
|
||
|
|
|
|
|
Web Servlet |
|
Login |
|
|
|
|
Users |
|
|
|
|
Authenticate User |
|
|
|
|
||
|
|
|
|
Process |
|
|
|
|
|||
|
|
|
|
|
|
|
|
|
|
||
|
Login |
Response |
|
Result |
|
Authenticate |
|
|
|||
|
|
|
|
|
|
||||||
|
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
Authenticate |
|
User SQL |
|
|
|
|
|
|
|
|
Pages |
User SQL |
|
Query |
|
|
|
|
|
|
|
|
Query Result |
|
|
|
|
|
|
|
|
|
|
|
|
|
Web Server/ |
|
|
||
|
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
Database Boundary |
|
|
|
|
|
|
|
|
|
|
|
Data |
|
|
|
|
|
|
|
|
Web |
|
|
|
|
||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Pages |
|
College |
|
|
|
|
|
|
|
|
|
|
|
Library |
|
Database |
|
|
|
|
|
|
|
|
|
Database |
|
Files |
|
|
Data
to gain a greater understanding of the logic of the product, its internal components, as well as its interactions with external elements. Whether an application, a system, or an entire environment, it needs to be divided into smaller containers or compartments. Those might be subroutines, modules, or objects if you’re focusing on software, computers, or operating systems; they might be protocols if you’re focusing on systems or networks; or they might be departments, tasks, and networks if you’re focusing on an entire business infrastructure. Each identified element should be evaluated in order to understand inputs, processing, security, data management, storage, and outputs.
In the decomposition process, you must identify five key concepts:
Trust Boundaries Any location where the level of trust or security changes Dataflow Paths The movement of data between locations
Input Points Locations where external input is received
Privileged Operations Any activity that requires greater privileges than of a standard user account or process, typically required to make system changes or alter security
Details about Security Stance and Approach The declaration of the security policy, security foundations, and security assumptions
