
- •Acknowledgments
- •About the Authors
- •About the Technical Editors
- •Contents at a Glance
- •Contents
- •Foreword
- •Introduction
- •Overview of the CISSP Exam
- •The Elements of This Study Guide
- •Study Guide Exam Objectives
- •Objective Map
- •Reader Support for This Book
- •Security 101
- •Confidentiality
- •Integrity
- •Availability
- •Protection Mechanisms
- •Security Boundaries
- •Third-Party Governance
- •Documentation Review
- •Manage the Security Function
- •Alignment of Security Function to Business Strategy, Goals, Mission, and Objectives
- •Organizational Processes
- •Organizational Roles and Responsibilities
- •Security Control Frameworks
- •Due Diligence and Due Care
- •Security Policy, Standards, Procedures, and Guidelines
- •Security Policies
- •Security Standards, Baselines, and Guidelines
- •Security Procedures
- •Threat Modeling
- •Identifying Threats
- •Determining and Diagramming Potential Attacks
- •Performing Reduction Analysis
- •Prioritization and Response
- •Supply Chain Risk Management
- •Summary
- •Exam Essentials
- •Written Lab
- •Review Questions
- •Job Descriptions and Responsibilities
- •Candidate Screening and Hiring
- •Onboarding: Employment Agreements and Policies
- •Employee Oversight
- •Compliance Policy Requirements
- •Privacy Policy Requirements
- •Understand and Apply Risk Management Concepts
- •Risk Terminology and Concepts
- •Asset Valuation
- •Identify Threats and Vulnerabilities
- •Risk Assessment/Analysis
- •Risk Responses
- •Cost vs. Benefit of Security Controls
- •Countermeasure Selection and Implementation
- •Applicable Types of Controls
- •Security Control Assessment
- •Monitoring and Measurement
- •Risk Reporting and Documentation
- •Continuous Improvement
- •Risk Frameworks
- •Social Engineering
- •Social Engineering Principles
- •Eliciting Information
- •Prepending
- •Phishing
- •Spear Phishing
- •Whaling
- •Smishing
- •Vishing
- •Spam
- •Shoulder Surfing
- •Invoice Scams
- •Hoax
- •Impersonation and Masquerading
- •Tailgating and Piggybacking
- •Dumpster Diving
- •Identity Fraud
- •Typo Squatting
- •Influence Campaigns
- •Awareness
- •Training
- •Education
- •Improvements
- •Effectiveness Evaluation
- •Summary
- •Exam Essentials
- •Written Lab
- •Review Questions
- •Planning for Business Continuity
- •Project Scope and Planning
- •Organizational Review
- •BCP Team Selection
- •Resource Requirements
- •Legal and Regulatory Requirements
- •Business Impact Analysis
- •Identifying Priorities
- •Risk Identification
- •Likelihood Assessment
- •Impact Analysis
- •Resource Prioritization
- •Continuity Planning
- •Strategy Development
- •Provisions and Processes
- •Plan Approval and Implementation
- •Plan Approval
- •Plan Implementation
- •Training and Education
- •BCP Documentation
- •Summary
- •Exam Essentials
- •Written Lab
- •Review Questions
- •Categories of Laws
- •Criminal Law
- •Civil Law
- •Administrative Law
- •Laws
- •Computer Crime
- •Intellectual Property (IP)
- •Licensing
- •Import/Export
- •Privacy
- •State Privacy Laws
- •Compliance
- •Contracting and Procurement
- •Summary
- •Exam Essentials
- •Written Lab
- •Review Questions
- •Defining Sensitive Data
- •Defining Data Classifications
- •Defining Asset Classifications
- •Understanding Data States
- •Determining Compliance Requirements
- •Determining Data Security Controls
- •Data Maintenance
- •Data Loss Prevention
- •Marking Sensitive Data and Assets
- •Handling Sensitive Information and Assets
- •Data Collection Limitation
- •Data Location
- •Storing Sensitive Data
- •Data Destruction
- •Ensuring Appropriate Data and Asset Retention
- •Data Protection Methods
- •Digital Rights Management
- •Cloud Access Security Broker
- •Pseudonymization
- •Tokenization
- •Anonymization
- •Understanding Data Roles
- •Data Owners
- •Asset Owners
- •Business/Mission Owners
- •Data Processors and Data Controllers
- •Data Custodians
- •Administrators
- •Users and Subjects
- •Using Security Baselines
- •Comparing Tailoring and Scoping
- •Standards Selection
- •Summary
- •Exam Essentials
- •Written Lab
- •Review Questions
- •Cryptographic Foundations
- •Goals of Cryptography
- •Cryptography Concepts
- •Cryptographic Mathematics
- •Ciphers
- •Modern Cryptography
- •Cryptographic Keys
- •Symmetric Key Algorithms
- •Asymmetric Key Algorithms
- •Hashing Algorithms
- •Symmetric Cryptography
- •Cryptographic Modes of Operation
- •Data Encryption Standard
- •Triple DES
- •International Data Encryption Algorithm
- •Blowfish
- •Skipjack
- •Rivest Ciphers
- •Advanced Encryption Standard
- •CAST
- •Comparison of Symmetric Encryption Algorithms
- •Symmetric Key Management
- •Cryptographic Lifecycle
- •Summary
- •Exam Essentials
- •Written Lab
- •Review Questions
- •Asymmetric Cryptography
- •Public and Private Keys
- •ElGamal
- •Elliptic Curve
- •Diffie–Hellman Key Exchange
- •Quantum Cryptography
- •Hash Functions
- •RIPEMD
- •Comparison of Hash Algorithm Value Lengths
- •Digital Signatures
- •HMAC
- •Digital Signature Standard
- •Public Key Infrastructure
- •Certificates
- •Certificate Authorities
- •Certificate Lifecycle
- •Certificate Formats
- •Asymmetric Key Management
- •Hybrid Cryptography
- •Applied Cryptography
- •Portable Devices
- •Web Applications
- •Steganography and Watermarking
- •Networking
- •Emerging Applications
- •Cryptographic Attacks
- •Salting Saves Passwords
- •Ultra vs. Enigma
- •Summary
- •Exam Essentials
- •Written Lab
- •Review Questions
- •Secure Design Principles
- •Objects and Subjects
- •Closed and Open Systems
- •Secure Defaults
- •Fail Securely
- •Keep It Simple
- •Zero Trust
- •Privacy by Design
- •Trust but Verify
- •Techniques for Ensuring CIA
- •Confinement
- •Bounds
- •Isolation
- •Access Controls
- •Trust and Assurance
- •Trusted Computing Base
- •State Machine Model
- •Information Flow Model
- •Noninterference Model
- •Take-Grant Model
- •Access Control Matrix
- •Bell–LaPadula Model
- •Biba Model
- •Clark–Wilson Model
- •Brewer and Nash Model
- •Goguen–Meseguer Model
- •Sutherland Model
- •Graham–Denning Model
- •Harrison–Ruzzo–Ullman Model
- •Select Controls Based on Systems Security Requirements
- •Common Criteria
- •Authorization to Operate
- •Understand Security Capabilities of Information Systems
- •Memory Protection
- •Virtualization
- •Trusted Platform Module
- •Interfaces
- •Fault Tolerance
- •Encryption/Decryption
- •Summary
- •Exam Essentials
- •Written Lab
- •Review Questions
- •Shared Responsibility
- •Hardware
- •Firmware
- •Client-Based Systems
- •Mobile Code
- •Local Caches
- •Server-Based Systems
- •Large-Scale Parallel Data Systems
- •Grid Computing
- •Peer to Peer
- •Industrial Control Systems
- •Distributed Systems
- •Internet of Things
- •Edge and Fog Computing
- •Static Systems
- •Network-Enabled Devices
- •Cyber-Physical Systems
- •Elements Related to Embedded and Static Systems
- •Security Concerns of Embedded and Static Systems
- •Specialized Devices
- •Microservices
- •Infrastructure as Code
- •Virtualized Systems
- •Virtual Software
- •Virtualized Networking
- •Software-Defined Everything
- •Virtualization Security Management
- •Containerization
- •Serverless Architecture
- •Mobile Devices
- •Mobile Device Security Features
- •Mobile Device Deployment Policies
- •Process Isolation
- •Hardware Segmentation
- •System Security Policy
- •Covert Channels
- •Attacks Based on Design or Coding Flaws
- •Rootkits
- •Incremental Attacks
- •Summary
- •Exam Essentials
- •Written Lab
- •Review Questions
- •Apply Security Principles to Site and Facility Design
- •Secure Facility Plan
- •Site Selection
- •Facility Design
- •Equipment Failure
- •Wiring Closets
- •Server Rooms/Data Centers
- •Intrusion Detection Systems
- •Cameras
- •Access Abuses
- •Media Storage Facilities
- •Evidence Storage
- •Restricted and Work Area Security
- •Utility Considerations
- •Fire Prevention, Detection, and Suppression
- •Perimeter Security Controls
- •Internal Security Controls
- •Key Performance Indicators of Physical Security
- •Summary
- •Exam Essentials
- •Written Lab
- •Review Questions
- •OSI Model
- •History of the OSI Model
- •OSI Functionality
- •Encapsulation/Deencapsulation
- •OSI Layers
- •TCP/IP Model
- •Common Application Layer Protocols
- •SNMPv3
- •Transport Layer Protocols
- •Domain Name System
- •DNS Poisoning
- •Domain Hijacking
- •Internet Protocol (IP) Networking
- •IP Classes
- •ICMP
- •IGMP
- •ARP Concerns
- •Secure Communication Protocols
- •Implications of Multilayer Protocols
- •Converged Protocols
- •Voice over Internet Protocol (VoIP)
- •Software-Defined Networking
- •Microsegmentation
- •Wireless Networks
- •Securing the SSID
- •Wireless Channels
- •Conducting a Site Survey
- •Wireless Security
- •Wi-Fi Protected Setup (WPS)
- •Wireless MAC Filter
- •Wireless Antenna Management
- •Using Captive Portals
- •General Wi-Fi Security Procedure
- •Wireless Communications
- •Wireless Attacks
- •Other Communication Protocols
- •Cellular Networks
- •Content Distribution Networks (CDNs)
- •Secure Network Components
- •Secure Operation of Hardware
- •Common Network Equipment
- •Network Access Control
- •Firewalls
- •Endpoint Security
- •Transmission Media
- •Network Topologies
- •Ethernet
- •Sub-Technologies
- •Summary
- •Exam Essentials
- •Written Lab
- •Review Questions
- •Protocol Security Mechanisms
- •Authentication Protocols
- •Port Security
- •Quality of Service (QoS)
- •Secure Voice Communications
- •Voice over Internet Protocol (VoIP)
- •Vishing and Phreaking
- •PBX Fraud and Abuse
- •Remote Access Security Management
- •Remote Connection Security
- •Plan a Remote Access Security Policy
- •Multimedia Collaboration
- •Remote Meeting
- •Instant Messaging and Chat
- •Load Balancing
- •Virtual IPs and Load Persistence
- •Active-Active vs. Active-Passive
- •Manage Email Security
- •Email Security Goals
- •Understand Email Security Issues
- •Email Security Solutions
- •Virtual Private Network
- •Tunneling
- •How VPNs Work
- •Always-On
- •Common VPN Protocols
- •Switching and Virtual LANs
- •Switch Eavesdropping
- •Private IP Addresses
- •Stateful NAT
- •Automatic Private IP Addressing
- •Third-Party Connectivity
- •Circuit Switching
- •Packet Switching
- •Virtual Circuits
- •Fiber-Optic Links
- •Security Control Characteristics
- •Transparency
- •Transmission Management Mechanisms
- •Prevent or Mitigate Network Attacks
- •Eavesdropping
- •Modification Attacks
- •Summary
- •Exam Essentials
- •Written Lab
- •Review Questions
- •Controlling Access to Assets
- •Controlling Physical and Logical Access
- •The CIA Triad and Access Controls
- •Managing Identification and Authentication
- •Comparing Subjects and Objects
- •Registration, Proofing, and Establishment of Identity
- •Authorization and Accountability
- •Authentication Factors Overview
- •Something You Know
- •Something You Have
- •Something You Are
- •Multifactor Authentication (MFA)
- •Two-Factor Authentication with Authenticator Apps
- •Passwordless Authentication
- •Device Authentication
- •Service Authentication
- •Mutual Authentication
- •Implementing Identity Management
- •Single Sign-On
- •SSO and Federated Identities
- •Credential Management Systems
- •Credential Manager Apps
- •Scripted Access
- •Session Management
- •Provisioning and Onboarding
- •Deprovisioning and Offboarding
- •Defining New Roles
- •Account Maintenance
- •Account Access Review
- •Summary
- •Exam Essentials
- •Written Lab
- •Review Questions
- •Comparing Access Control Models
- •Comparing Permissions, Rights, and Privileges
- •Understanding Authorization Mechanisms
- •Defining Requirements with a Security Policy
- •Introducing Access Control Models
- •Discretionary Access Control
- •Nondiscretionary Access Control
- •Implementing Authentication Systems
- •Implementing SSO on the Internet
- •Implementing SSO on Internal Networks
- •Understanding Access Control Attacks
- •Crackers, Hackers, and Attackers
- •Risk Elements
- •Common Access Control Attacks
- •Core Protection Methods
- •Summary
- •Exam Essentials
- •Written Lab
- •Review Questions
- •Security Testing
- •Security Assessments
- •Security Audits
- •Performing Vulnerability Assessments
- •Describing Vulnerabilities
- •Vulnerability Scans
- •Penetration Testing
- •Compliance Checks
- •Code Review and Testing
- •Interface Testing
- •Misuse Case Testing
- •Test Coverage Analysis
- •Website Monitoring
- •Implementing Security Management Processes
- •Log Reviews
- •Account Management
- •Disaster Recovery and Business Continuity
- •Training and Awareness
- •Key Performance and Risk Indicators
- •Summary
- •Exam Essentials
- •Written Lab
- •Review Questions
- •Need to Know and Least Privilege
- •Separation of Duties (SoD) and Responsibilities
- •Two-Person Control
- •Job Rotation
- •Mandatory Vacations
- •Privileged Account Management
- •Service Level Agreements (SLAs)
- •Addressing Personnel Safety and Security
- •Duress
- •Travel
- •Emergency Management
- •Security Training and Awareness
- •Provision Resources Securely
- •Information and Asset Ownership
- •Asset Management
- •Apply Resource Protection
- •Media Management
- •Media Protection Techniques
- •Managed Services in the Cloud
- •Shared Responsibility with Cloud Service Models
- •Scalability and Elasticity
- •Provisioning
- •Baselining
- •Using Images for Baselining
- •Automation
- •Managing Change
- •Change Management
- •Versioning
- •Configuration Documentation
- •Managing Patches and Reducing Vulnerabilities
- •Systems to Manage
- •Patch Management
- •Vulnerability Management
- •Vulnerability Scans
- •Common Vulnerabilities and Exposures
- •Summary
- •Exam Essentials
- •Written Lab
- •Review Questions
- •Conducting Incident Management
- •Defining an Incident
- •Incident Management Steps
- •Basic Preventive Measures
- •Understanding Attacks
- •Intrusion Detection and Prevention Systems
- •Specific Preventive Measures
- •Logging and Monitoring
- •The Role of Monitoring
- •Log Management
- •Egress Monitoring
- •Automating Incident Response
- •Understanding SOAR
- •Threat Intelligence
- •Summary
- •Exam Essentials
- •Written Lab
- •Review Questions
- •The Nature of Disaster
- •Natural Disasters
- •Human-Made Disasters
- •Protecting Hard Drives
- •Protecting Servers
- •Protecting Power Sources
- •Trusted Recovery
- •Quality of Service
- •Recovery Strategy
- •Business Unit and Functional Priorities
- •Crisis Management
- •Emergency Communications
- •Workgroup Recovery
- •Alternate Processing Sites
- •Database Recovery
- •Recovery Plan Development
- •Emergency Response
- •Personnel and Communications
- •Assessment
- •Backups and Off-site Storage
- •Software Escrow Arrangements
- •Utilities
- •Logistics and Supplies
- •Recovery vs. Restoration
- •Testing and Maintenance
- •Structured Walk-Through
- •Simulation Test
- •Parallel Test
- •Lessons Learned
- •Maintenance
- •Summary
- •Exam Essentials
- •Written Lab
- •Review Questions
- •Investigations
- •Investigation Types
- •Evidence
- •Investigation Process
- •Major Categories of Computer Crime
- •Military and Intelligence Attacks
- •Business Attacks
- •Financial Attacks
- •Terrorist Attacks
- •Grudge Attacks
- •Thrill Attacks
- •Hacktivists
- •Ethics
- •Organizational Code of Ethics
- •(ISC)2 Code of Ethics
- •Ethics and the Internet
- •Summary
- •Exam Essentials
- •Written Lab
- •Review Questions
- •Software Development
- •Systems Development Lifecycle
- •Lifecycle Models
- •Gantt Charts and PERT
- •Change and Configuration Management
- •The DevOps Approach
- •Application Programming Interfaces
- •Software Testing
- •Code Repositories
- •Service-Level Agreements
- •Third-Party Software Acquisition
- •Establishing Databases and Data Warehousing
- •Database Management System Architecture
- •Database Transactions
- •Security for Multilevel Databases
- •Open Database Connectivity
- •NoSQL
- •Expert Systems
- •Machine Learning
- •Neural Networks
- •Summary
- •Exam Essentials
- •Written Lab
- •Review Questions
- •Malware
- •Sources of Malicious Code
- •Viruses
- •Logic Bombs
- •Trojan Horses
- •Worms
- •Spyware and Adware
- •Ransomware
- •Malicious Scripts
- •Zero-Day Attacks
- •Malware Prevention
- •Platforms Vulnerable to Malware
- •Antimalware Software
- •Integrity Monitoring
- •Advanced Threat Protection
- •Application Attacks
- •Buffer Overflows
- •Time of Check to Time of Use
- •Backdoors
- •Privilege Escalation and Rootkits
- •Injection Vulnerabilities
- •SQL Injection Attacks
- •Code Injection Attacks
- •Command Injection Attacks
- •Exploiting Authorization Vulnerabilities
- •Insecure Direct Object References
- •Directory Traversal
- •File Inclusion
- •Request Forgery
- •Session Hijacking
- •Application Security Controls
- •Input Validation
- •Web Application Firewalls
- •Database Security
- •Code Security
- •Secure Coding Practices
- •Source Code Comments
- •Error Handling
- •Hard-Coded Credentials
- •Memory Management
- •Summary
- •Exam Essentials
- •Written Lab
- •Review Questions
- •Chapter 2: Personnel Security and Risk Management Concepts
- •Chapter 3: Business Continuity Planning
- •Chapter 4: Laws, Regulations, and Compliance
- •Chapter 5: Protecting Security of Assets
- •Chapter 10: Physical Security Requirements
- •Chapter 11: Secure Network Architecture and Components
- •Chapter 12: Secure Communications and Network Attacks
- •Chapter 17: Preventing and Responding to Incidents
- •Chapter 18: Disaster Recovery Planning
- •Chapter 19: Investigations and Ethics
- •Chapter 20: Software Development Security
- •Chapter 21: Malicious Code and Application Attacks
- •Chapter 3: Business Continuity Planning
- •Chapter 5: Protecting Security of Assets
- •Chapter 6: Cryptography and Symmetric Key Algorithms
- •Chapter 12: Secure Communications and Network Attacks
- •Chapter 15: Security Assessment and Testing
- •Chapter 17: Preventing and Responding to Incidents
- •Chapter 18: Disaster Recovery Planning
- •Chapter 19: Investigations and Ethics
- •Chapter 21: Malicious Code and Application Attacks
- •Index
Implement and Manage Physical Security |
477 |
If not mandated by regulations, a self-imposed schedule of control testing should be implemented for door locks, fences, gates, access control vestibules, turnstiles, video cameras, and all other physical security controls.
Perimeter Security Controls
The accessibility to the building or campus location is also important. Single entrances are great for providing security, but multiple entrances are better for evacuation during emergencies. What types of roads are nearby, such as residential streets or highways? What means of transportation are easily accessible (trains, highway, airport, shipping)? What about traffic levels throughout the day?
Keep in mind that accessibility is also constrained by the need for perimeter security. The needs of access and use should meld and support the implementation and operation of perimeter security. The use of physical access controls and monitoring personnel and equip-
ment entering and leaving, as well as auditing/logging all physical events, are key elements in maintaining overall organizational security.
Fences, Gates,Turnstiles, and Access Control Vestibules
A fence is a perimeter-defining device. Fences are used to clearly differentiate between areas that are under a specific level of security protection and those that aren’t. Fencing can include a wide range of components, materials, and construction methods. It can consist of stripes painted on the ground, chain link fences, barbed wire, concrete walls, and even invisible perimeters using laser, motion, or heat detectors. Various types of fences are effective against different types of intruders:
■■Fences 3 to 4 feet high deter casual trespassers.
■■Fences 6 to 7 feet high are too hard to climb easily and deter most intruders, except determined ones.
■■Fences 8 or more feet high with strands of barbed or razor wire deter even determined intruders.
An advanced form of fencing is known as a perimeter intrusion detection and assessment system (PIDAS). A PIDAS is a fence system that has two or three fences used in concert to optimize security. PIDAS fencing is often present around military locations and prisons. Typically, a PIDAS fence has one main tall fence that may be 8 to 20 feet tall. The main fence may be electrified, may have barbed wire/razor wire elements, and/or can include touch detection technologies. This main fence is then surrounded by an outside fence, which may only be 4 to 6 feet tall. The purpose of this outer fence is to keep animals and casual trespassers from accessing the main fence. This reduces the nuisance alarm rate (NAR) or false positives from animals or foliage on interior fences. Additional fences can be located between the main fence and the exterior fence. These additional fences may be electrified or use barbed/razor wire. The space between the fences can serve as a corridor for guard patrols or wandering guard dogs. These corridors are kept free of vegetation.
478 Chapter 10 ■ Physical Security Requirements
A gate is a controlled exit and entry point in a fence or wall. The deterrent level of a gate must be equivalent to the deterrent level of the fence to sustain the effectiveness of the fence as a whole. Hinges and locking/closing mechanisms should be hardened against tampering, destruction, or removal. When a gate is closed, it should not offer any additional access vulnerabilities. Keep the number of gates to a minimum. They can be monitored by guards.
When they’re not protected by guards, use of dogs or security cameras is recommended. A turnstile (see Figure 10.5) is a form of gate that prevents more than one person at a time from gaining entry and often restricts movement in one direction. It is used to gain
entry but not to exit, or vice versa. A turnstile is basically the fencing equivalent of a secured revolving door. A turnstile can be designed to turn freely to allow easy egress. An ingress turnstile can be implemented with a locking mechanism that requires personnel to provide a code, combination, or credential before it will allow a single person to enter the secured area. A turnstile can be used as a personnel flow control device to limit the direction of travel and the speed of access (i.e., only one person can pass at a time after valid authentication).
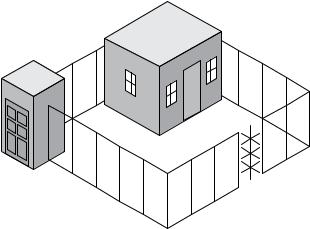
FIGURE 10 . 5 A secure physical boundary with an access control vestibule and a turnstile
Secured area
Mantrap
Turnstile
An access control vestibule (also known as a mantrap) is a double set of doors (also shown in Figure 10.5) that is often protected by a guard or some other physical layout that prevents piggybacking and can trap individuals at the discretion of security personnel. The purpose of an access control vestibule is to immobilize a subject until their identity and authentication authority are verified. If a subject is authorized for entry, the inner door opens, allowing entry into the facility or onto the premises. If a subject is not authorized, both doors remain closed and locked until an escort (typically a guard or a police officer) arrives to escort the subject off the property or arrest the subject for trespassing (this is known as a delay feature). Often
Implement and Manage Physical Security |
479 |
an access control vestibule includes a scale to prevent piggybacking or tailgating. Access control vestibules can be used to control entrance into a facility or entrance within a facility to a higher secured area, such as a data center or an SCIF.
Another key element of physical security, especially for data centers, government facilities, and highly secure organizations, is security bollards, which prevent vehicles from ramming access points and entrances. These can be permanently fixed in place or automatically rise from their installed base at a fixed time or an alert. They are often disguised as planters or other architectural elements. See the previous discussion of CPTED in the “Facility Design” section.
Barricades, in addition to fencing, are used to control both foot traffic and vehicles. K-rails (often seen during road construction), large planters, zigzag queues, bollards, and tire shredders are all examples of barricades. When used properly, they can control crowds and prevent vehicles from being used to cause damage to your building. Long straight and unobstructed vehicle paths should be avoided in order to prevent the buildup of excessive speed. If generators and fuel storage are present, additional layers of barricade protection may be necessary to prevent tampering or destruction.
Lighting
Lighting is the most commonly used form of perimeter security control providing the security benefit of deterrence. The primary purpose of lighting is to discourage casual intruders, trespassers, prowlers, or would-be thieves who would rather perform their misdeeds, such as vandalism, theft, and loitering, in the dark. Both interior and exterior lighting should
be implemented for security, especially related to parking areas, walkways, and entrances. Exterior lighting should generally be on from dusk until dawn. Interior lighting may be always on, switched manually, or triggered on demand, possibly via motion. Emergency lighting should be implemented in key areas (such as exits and escape routes) and triggered with the loss of power or along with a fire alarm. Lighting is often claimed to be the most commonly deployed physical security mechanism. However, lighting is only a deterrent and not a strong deterrent. It should not be used as the primary or sole protection mechanism except in areas with a low threat level. Your entire site, inside and out, should be well lit. This provides for easy identification of personnel and makes it easier to notice intrusions.
Lighting should not necessarily be used to illuminate the positions of guards, dogs, patrol posts, or other similar security elements. However, these can be illuminated if knowledge of their presence is to be used as a deterrent. Lighting should be combined with security guards, guard dogs, security cameras, or some other form of intrusion detection or surveillance mechanism. Lighting must not cause a nuisance or problem for nearby residents, roads, railways, airports, and so on. It should also never cause glare or reflective distraction to guards, dogs, and monitoring equipment, which could otherwise aid attackers during break-in attempts. Strong lights used to illuminate a building located on a fence line pointing inward can function as a means to hide intruders. Just think of standing in the dark with someone pointing a flashlight at you—you will be unable to see them because the light overpowers your vision.
480 Chapter 10 ■ Physical Security Requirements
It is generally accepted as a de facto standard that lighting used for perimeter protection should illuminate critical areas with at least 2 foot-candles of power (which is approximately 2 lumens, or 20 lux). Another common issue for the use of lighting is the placement of the lights. Standards seem to indicate that light poles should be placed the same distance apart as the diameter of the illuminated area created by illumination elements. Thus, if a lighted area is 40 feet in diameter, poles should be 40 feet apart. This light pole positioning allows for the intersection of lighted areas on the ground, thus preventing an intruder to gain access under the cover of darkness.
Security Guards and Guard Dogs
All physical security controls, whether static deterrents or active detection and surveillance mechanisms, ultimately rely on personnel to intervene and stop actual intrusions and attacks. Security guards exist to fulfill this need. Guards can be posted around a perimeter or inside to monitor access points or watch detection and surveillance monitors. The real benefit of guards is that they are able to adapt and react to various conditions or situations. Guards can learn and recognize attack and intrusion activities and patterns, can adjust to a changing environment, and can make decisions and judgment calls. Security guards are often an appropriate security control when immediate situation handling and decision making on site is necessary.
Guards should perform patrols both internally and externally to look for security violations, unauthorized entities, or other abnormalities throughout the facility and campus grounds. Patrols should be frequent, but at random intervals. This prevents an intruder from observing a pattern of patrols and then timing their break-in accordingly.
Unfortunately, using security guards is not a perfect solution. There are numerous disadvantages to deploying, maintaining, and relying on security guards. Not all environments and facilities support security guards. This may be because of actual human incompatibility or the layout, design, location, and construction of the facility. Not all security guards are themselves reliable. Prescreening, bonding, and training do not guarantee that you won’t end up with an ineffective or unreliable security guard.
Even if a guard is initially reliable, guards are subject to physical injury and illness, take vacations, can become distracted, are vulnerable to social engineering, and may become unemployable because of substance abuse. In addition, security guards usually offer protection only up to the point at which their life is endangered. Additionally, security guards are usually unaware of the scope of the operations within a facility and are therefore not thoroughly equipped to know how to respond to every situation. Though this is considered a disadvantage, the lack of knowledge of the scope of the operations within a facility can also be considered an advantage, because this supports confidentiality of those operations and thus helps reduce the possibility that a security guard will be involved in the disclosure of confidential information. Finally, security guards are expensive whether they are employees or provided by a third-party contractor.
Guard dogs can be an alternative to security guards. They can often be deployed as a perimeter security control. As a detection and deterrent, dogs are extremely effective. However, dogs are costly, require a high level of maintenance, and impose serious insurance and liability requirements.
