
Network Management
.pdf
Ch.8 - Network Management
1Overview
2SNMP
3GET
4SET
5TRAP
6MIB
7"Future, SNMPv2 or HTML"
1
Ch.8 - Network Management
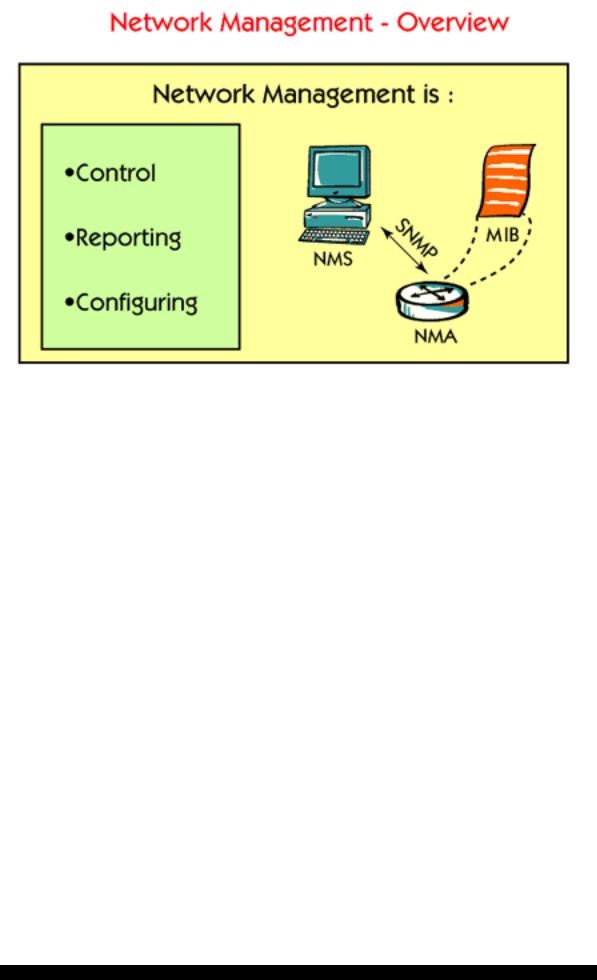
Network Management is used for the management of different components in a network.
With network management you can get information about errors and performance. You can also use network management for remote configuration of different devices.
Error control is done by continuous polling for status information about the ”health” of different components in the network. When something is wrong it is reported to the network administrator.
Network Management normally has 4 components:
1.The component that supervises. This component is called NMS, the Network Management Server, and is used to manage the entire network. It receives all the information and displays it. Commonly used NMS platforms are HP Open View and IBM Tivoli.
2.The component that is supervised. This component is called NMA, the Network Management Agent. The NMA is a network component, for example a router, a switch or a hub, but it could also be a host such as a workstation, a printer or a server.
3.A protocol that transfers the information between the agent and the server. One commonly used protocol is SNMP, the Simple Network Management Protocol.
4.A list of possible things to manage. These things are called MIB, the Management Information Base. Example of things that can be managed are: the time a device has been up and running since the last reboot, information from the routing table in a router and so on.
2

Ch.8 - Network Management
One protocol that is used for Network Management is called SNMP, which stands for Simple Network Management Protocol. The SNMP protocol is an ”open” standard for the Internet, which is described in an RFC. The SNMP protocol can be used for monitoring and controlling many different types of equipment from different manufacturers, and not only in TCP/IP networks.
SNMP uses answers and questions to transfer the information between an agent and the management server.
SNMP uses different commands for answering or storing different values to or from an agent. The different things which are possible to manage are different variables, called MIB, which stands for Management Information Base. These variables are grouped together in something called MIB modules, for example MIB I, MIB II and so on. MIB I and MIB II are standard MIB modules, described in RFCs. There are also vendor specific MIBs for management of vendor specific equipment.
There are five different commands used by SNMP:
1.With a ”GetRequest” you can fetch a value from a specific variable.
2.With a ”GetNextRequest” you can fetch the next value in a MIB category without knowing its exact name.
3.”SetRequest” is used for storing a value in a specific variable.
4.”GetResponse” is a response from an agent as a reply to a fetch or a store command.
5.”Trap” is an automatically generated ”alarm” from an agent when an important event has happened.
3
Ch.8 - Network Management
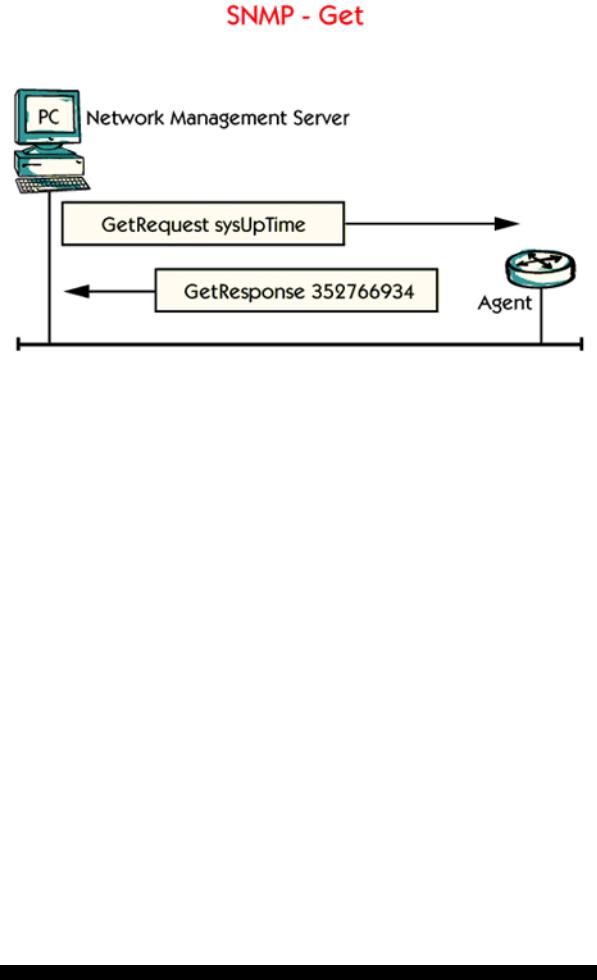
The Get command is used for polling information from a management agent.
In the picture you can see a ”GetRequest” question from the management server to the router. The question is about the sysUpTime of the router, which means the time the router has been running since the last reboot. The answer from the router is 352 766 934 hundredths of a second, which is about 1000 hours.
4
Ch.8 - Network Management
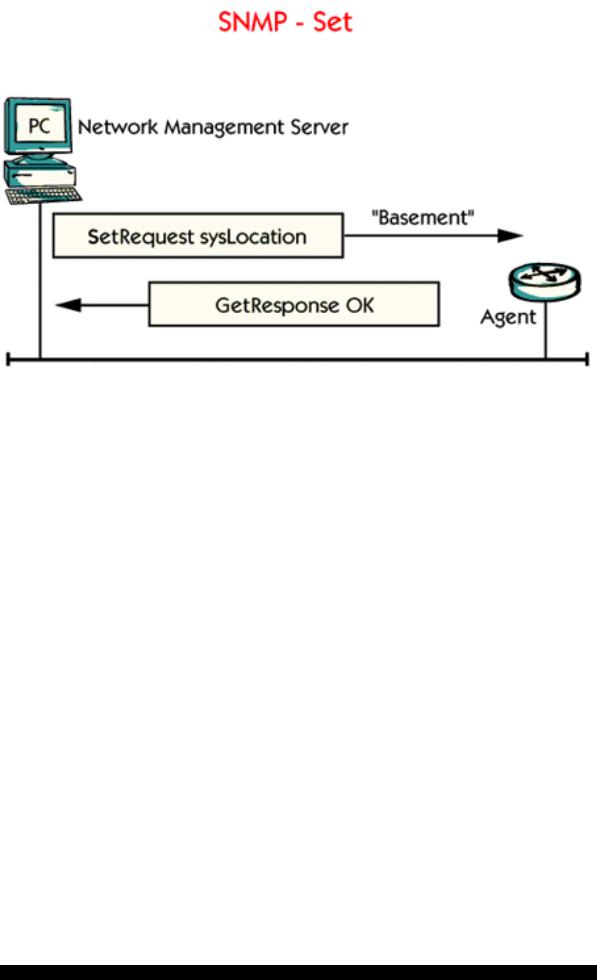
With the Set command there is a possibility to send information to an agent. This is one way of configuring different components from a management server.
In the picture NMS sets the location of the router to ”Basement”. This is a way for the system administrator to let the router store information that is physically located in the basement of the building.
The main advantage of configuring components in this way is that almost all vendors support SNMP in their products. Without SNMP you need different configuration programs for different types of equipment. A disadvantage with the SNMP protocol is that configuration with SNMP is not password protected with a secret word from the beginning. This means that unauthorized people can configure the devices if you don’t take care.
5
Ch.8 - Network Management
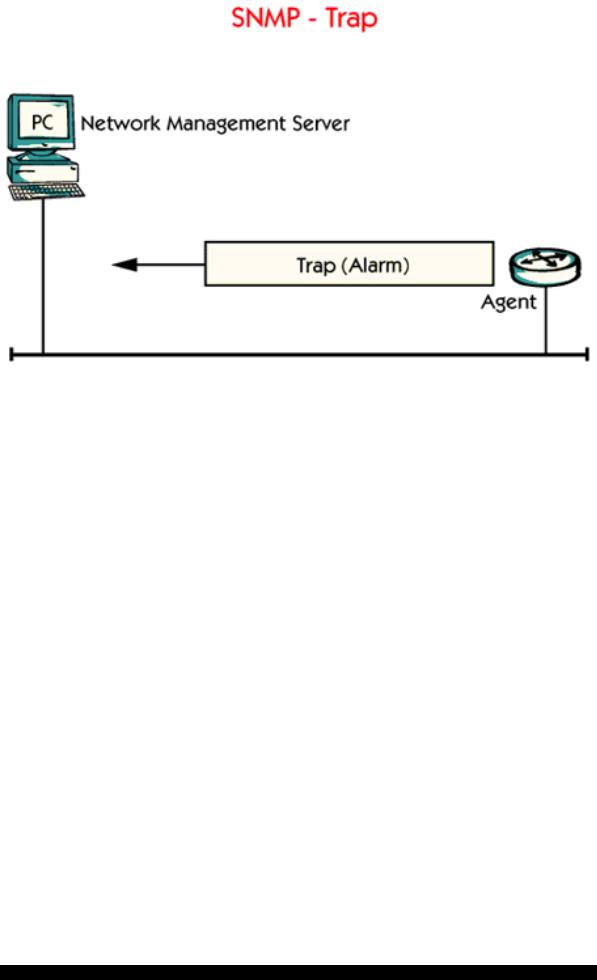
A Trap is a kind of alarm which is automatically generated and sent from an agent to the management server when something important has happened.
Examples of Trap messages are when a router has rebooted or if a link has gone up or down. Important for the Trap function is that the IP address of the Network Management Server is configured in the agent, so that the agent knows where to send the Traps.
6
Ch.8 - Network Management
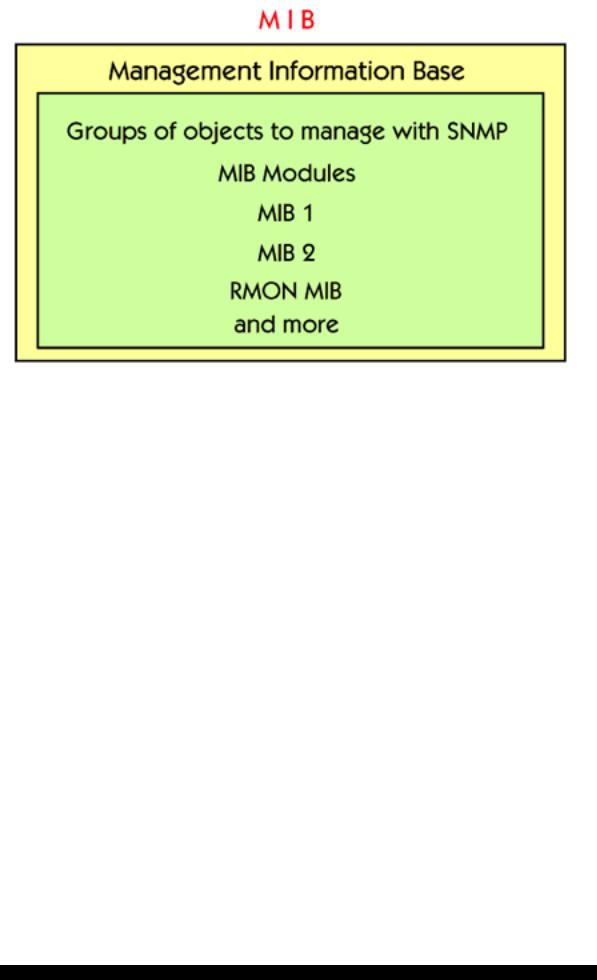
The MIB specifies network management variables and their meanings.
There are different types of MIB modules, for different types of management.
Inside a MIB module, the objects are grouped in different categories such as system, interfaces, IP, UDP, TCP and more.
Manufacturers are allowed to specify their own MIBs for their own equipment.
Example of vendor independent MIB modules are: MIB I, MIB II, RMON MIB. RMON stands for Remote Monitoring and is used for performance measurement.
ISO and ITU define the names of MIB variables.
7
Ch.8 - Network Management
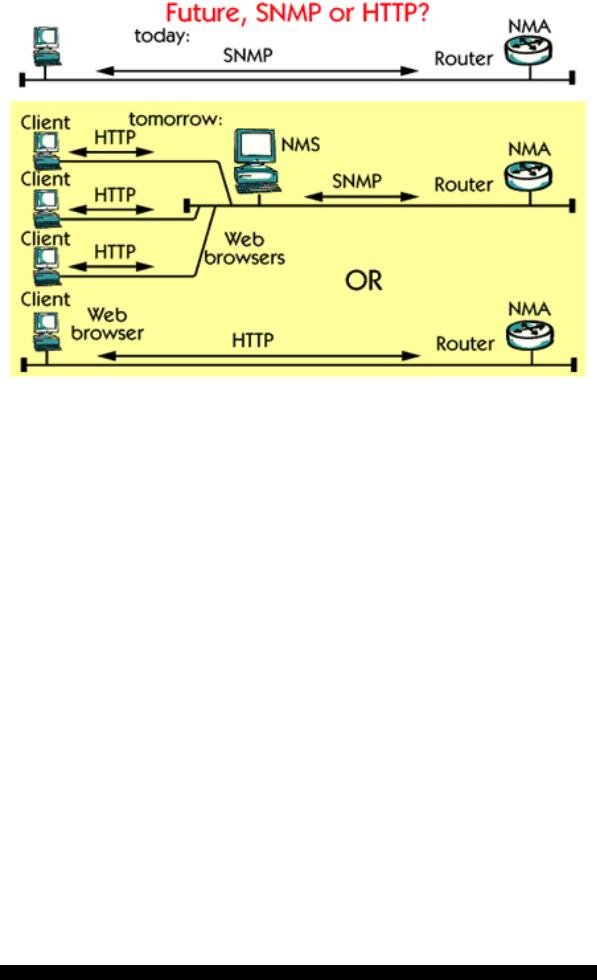
Today SNMP is widely used, but it is a very primitive protocol.
HTTP, which is a very popular protocol for web pages, can be used as an alternative for Network Management. You can use a common Web browser to manage different agents. In this case the agent must be converted in order to support access from the WEB browser.
A third alternative is also possible. This is a combination of both HTTP and SNMP. The idea is very simple. Instead of connecting the Web browser directly to the agent you connect it to the Network Management Server.
This requires no changes to the basic SNMP-based management strategy. Rather, it adds a Web interface to the existing SNMP management information in your network. There is a possibility to connect several web clients to the same management server, which gives flexibility for the network administrators.
8
