
- •Archives
- •What is an Archive?
- •What is a Self-Extracting Zip File?
- •Archive formats:
- •The WinZip window
- •Opening Archive
- •Viewing Files
- •Extracting Files
- •Create a New Archive
- •Adding Files
- •Deleting Files from Archive
- •Other Characteristics
- •The WinRar window
- •Viruses and anti-virus programs Keywords
- •6. Levels of polymorphism (Уровни полиморфизма). Факультативно….
- •7. Virus strain (Вирусный штам).
- •There are some famous examples of the viruses.
- •Tipes of viruses
- •5. Network virus (Сетевой вирус).
- •6. Encrypted virus (Шифрованный вирус).
- •Virus constructor (Конструктор для вирусов).
- •Anti-virus program
- •1. Firmware sentry (Программно-аппаратный сторож)
- •2. Anti- virus sentry (Программный антивирусный сторож).
- •4. Resident vaccine (Резидентная вакцина).
- •5. Anti-virus scanner (Антивирусный сканер)
- •6. Anti-virus disk inspector (Антивирусный ревизор диска).
- •The anti-virus scanner DoctorWeb (DrWeb).
- •Graphic mode of the DrWeb.
- •Graphic mode of the avp Kaspersky Anti-Virus.
The WinRar window
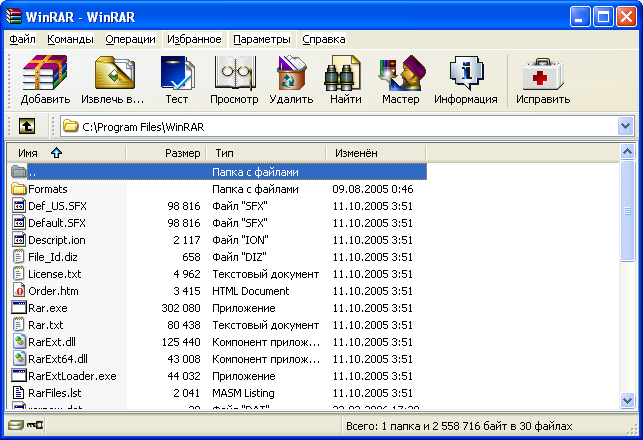
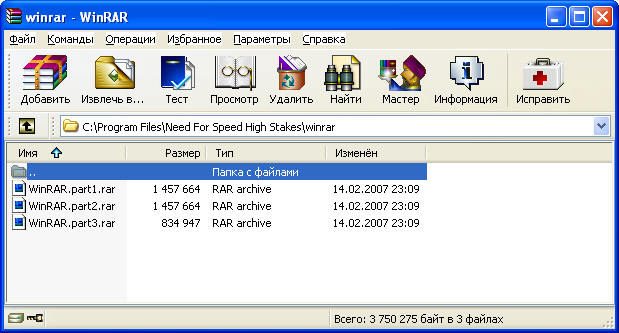
The WinRAR is archiver like WinZIP. But WinRAR can use a multivolume archive. WinRAR can cut big archive to many little parts. These parts could have different size. For extracting information from multivolume archive all parts of this archive must be moved into the same directory.
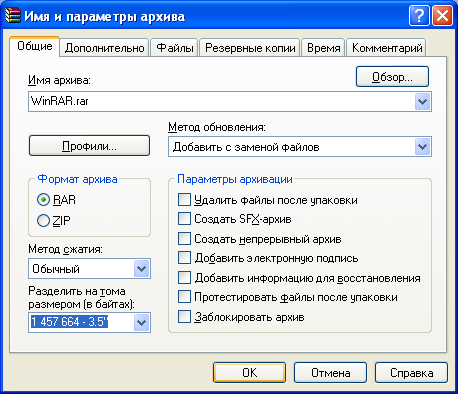
The result of the multivolume archive creation is something like that:
WinRAR can create Self-Extracting archives with extension EXE. In this case it is possible to extract information from that archive without WinRAR.
Viruses and anti-virus programs Keywords
COMPUTER VIRUS (Компьютерный вирус)
There is no precise definition of a computer virus. In general, we can say that it’s a program that can reproduce its own copies (possibly, in a modified form) that are capable of further reproduction. The term “computer virus” was introduced by F.Cohen in 1984.
1. CHECKSUM (Контрольная сумма).
A numeric value calculated for a file by a special algorithm. When a file changes, its checksum changes too. Checksums are used by disk inspectors to control data integrity.
2. SIGNATURE (Сигнатура)
A sequence of bytes that is specific (theoretically, unique) to a particular program. Signatures are used by anti-virus scanners for virus detection.
3. GOAT PROGRAM (программа “Козла”, программа-“дрозофила”).
A small test program that is infected with a virus in order to obtain the virus code.
4. CPU EMULATOR (Эмулятор Процессора)
A programmatic device that emulates CPU instructions. CPU emulation is used by anti-virus scanners to detect polymorphous viruses.
5. HEURISTIC ANALYZER (Эвристический анализ)
A programmatic device intended to detect code fragments typical to computer viruses. A heuristic analyzer is used to detect unknown viruses. The efficiency of a heuristic analyzer is determined by two parameters: percentage of detected viruses and percentage of false alarm (i.e. cases when the analyzer wrongly reports a virus in a file.) Russian scanner Doctor Web features a heuristic analyzer that is one of the best in the world.
6. Levels of polymorphism (Уровни полиморфизма). Факультативно….
Different polymorphous viruses can be detected and removed by algorithms of varying complexity. For instance, simple polymorphous viruses can be detected by a mask search, whereas complex viruses can be detected by essentially different algorithms. As of this writing, there are five levels of virus polymorphism.
7. Virus strain (Вирусный штам).
A modification of the original virus. Most commonly, strains appear due to the availability of virus source code.
There are some famous examples of the viruses.
One of the first most known viruses was named " Friday 13 ".
This virus operates only per day on Friday 13. The computer outputs crazy beeps, on the screen you can see the bright stain and the information in HDD is being deleted. Some viruses are not so dangerous as this.
The virus "Cookies" is known. It stops operation of the computer and writes on the screen "I want cookies!". If you enter from the keyboard a word "cookies", the computer will continue to work.
In reply to widely usage of the programs without license to use, the special virus was written. It stops operation of the computer and writes on the screen " stealing is bad! "
Today not only users are writing viruses. Now the many large military research institutes are developing new viruses. Because, the computer virus is a new secret weapon today.
The computers control today everything, including the armed forces. Therefore many military organizations wants to destroy the computer network of the country-opponent in case of war.
With appearance the Internet, the viruses have an opportunity to be distributed worldwide for a few hours. The virus reads a user electronic notepad and sends itself to all addresses.
So the virus "I love you!" has made economic damage more than all 2nd world war.
And what can't viruses do?
The computer virus can not infect the man.
The virus can not physically break down the device in the computer.
The virus can not get into the computer if it is off.
The virus can not infect the file on the write-protected diskette.
The virus can not get into the computer through scanner, keyboard, mouse, printer etc.
And what can viruses do?
The virus can get into the computer together with other program.
The virus can get into the computer through any resource of input of programs in the computer. For example, through a diskette, through the Internet, through a CD-ROM, through the modem, through e-mail etc.
The virus can delete any information on the computer.
The virus can slow down operation of the computer.
The virus can destroy operating system and the computer will not work at all.
The virus can be distributed through the Internet by self.
The virus can write itself to a diskette by self. (If the diskette is not write-protected).
The virus can break BIOS and stop the normal work of the motherboard.
The virus can make itself active by the special command. (by the special date, by the quantity of the infected files, by the command from other computer of the network).
The virus can infect even the anti-virus programs.
The virus can be included into the archive.
The virus can be existed even on an empty diskette (in a boot sector).
