
- •Основы письменной коммуникации в профессиональной деятельности в иноязычной среде
- •Самара 2012
- •Введение
- •Часть 1. Особенности научного стиля: лексические и фразеологические средства, разновидности и жанры Особенности научного стиля
- •Лексические средства научного стиля
- •Фразеологические средства научного стиля
- •Разновидности и жанры научного стиля
- •Компрессия текста и основные виды компрессии текста
- •Аннотация: понятие, функции, структура, характеристики
- •Основные характеристики аннотации:
- •Фразы, рекомендуемые для написания аннотации к научной статье:
- •Резюме: понятие, характеристики, план написания
- •Существует несколько обязательных характеристик хорошего резюме:
- •Пошаговый план написания резюме:
- •Рецензия: понятие и структура
- •Рецензия должна включать в себя следующую информацию:
- •Фразы, рекомендуемые для написания рецензии на научную статью:
- •Образцы компрессии текстов Аннотация статьи «Особенности самоконтроля младших школьников как универсального учебного действия»
- •Резюме статьи «Особенности самоконтроля младших школьников как универсального учебного действия»
- •Рецензия на статью «Особенности самоконтроля младших школьников как универсального учебного действия»
- •Часть 2. Практические задания Texte 1. What is a computer?
- •Texte 2. Basic features of database programs
- •Texte 3. Programming
- •Texte 4. Completely electronic device
- •Texte 5. Word-processing facilities
- •Internet software
- •Irc, audio and video chatting
- •Texte 6. Cryptography
- •1. Basic Terminology
- •2. Basic Cryptographic Algorithms
- •Texte 7. Hardware and software
- •Texte 8. Apple macintosh computers
- •Texte 9. Artificial intelligence
- •Texte 10. What is physics?
- •Texte 11. What are fuel cells?
- •Texte 12. How do solar cells work?
- •Texte 13. Mathematics as a science
- •Texte 14. Fields of mathematics
- •Texte 15. Mathematical beauty
- •Article 1. Mr-Radix: a multi-relational data mining algorithm
- •Introduction
- •Article 2. A survey of black hole attacks in wireless mobile ad hoc networks
- •1. Introduction
- •2. Background
- •2.1. Proactive (table-driven) Routing Protocol
- •2.2. Reactive (on-demand) Routing Protocol
- •2.3. Hybrid Routing Protocol
- •3. Single Black Hole Attack
- •3.1. Neighborhood-based and Routing Recovery Scheme [26]
- •3.2. Redundant Route Method and Unique Sequence Number Scheme [27]
- •3.3. Time-based Threshold Detection Scheme [28]
- •3.4. Random Two-hop ack and Bayesian Detection Scheme [29]
- •3.5. Resource-Efficient aCcounTability (reAct) Scheme based on Random Audits [30]
- •3.6. Detection, Prevention and Reactive aodv (dpraodv) Scheme [31]
- •3.7. Next Hop Information Scheme [32]
- •3.8. Nital Mistry et al.'s Method [33]
- •3.9. Intrusion Detection System based on Anti-black hole mechanism [34]
- •4. Collaborative Black Hole Attack
- •4.1. Dri Table and Cross Checking Scheme [36, 37]
- •4.2. Distributed Cooperative Mechanism (dcm) [38]
- •4.3. Hash based Scheme [39]
- •4.4. Hashed-based mac and Hash-based prf Scheme [40]
- •4.5. Backbone Nodes (bbn) and Restricted ip (rip) Scheme [41]
- •4.6. Bait dsr (bdsr) based on Hybrid Routing Scheme [43]
- •5. Conclusions and Future Works
- •Article 3. Quantum social networks
- •Introduction
- •1.2. Summary lead
- •2. Positive comments
- •3. Criticism and objections
- •4. Data analysis
- •5. Results and their representation
- •6. Conclusion
- •7. Prospects and applications
- •Appendix 2. Sample annotations
- •Appendix 3. Sample text with annotation
- •Appendix 4. Some tips on summary writing
- •Appendix 5. Some tips on review writing
- •I. Характеристика и описание работы
- •II. Структура работы. Характеристика построения книги и ее разделов
- •III. Вводная часть. Историческая справка. Выходные данные
- •IV. Основные достоинства и недостатки работы
- •1. Достоинства
- •2. Недостатки. Замечания
- •V. Оценка работы, рекомендации. Заключение
- •Sample review
- •Appendix 6. Spelling and punctuation Особенности орфографии английского языка
- •Литература
- •Научные журналы в электронном формате:
- •Содержание
- •Часть 1. Особенности научного стиля: лексические и фразеологические средства, разновидности и жанры 6
- •Часть 2. Практические задания 20
- •Основы письменной коммуникации в профессиональной деятельности в иноязычной среде
- •(Направление подготовки: 050100.62 «Педагогическое образование»; профили подготовки: «Математика и информатика», «Физика и информатика»)
2.3. Hybrid Routing Protocol
The hybrid routing protocol combines the advantages of proactive routing and reactive routing to overcome the defects of them. Most of hybrid routing protocols are designed as a hierarchical or layered network framework. In the beginning, proactive routing is employed to completely gather the unfamiliar routing information, then using the reactive routing to maintain the routing information when network topology changes. The familiar hybrid routing protocols are zone routing protocol (ZRP) [23] and temporally-ordered routing algorithm (TORA) [24].
3. Single Black Hole Attack
A black hole problem means that one malicious node utilizes the routing protocol to claim itself of being the shortest path to the destination node, but drops the routing packets but does not forward packets to its neighbors. A single black hole attack is easily happened in the mobile ad hoc networks [25]. An example is shown as Figure 1, node 1 stands for the source node and node 4 represents the destination node. Node 3 is a misbehavior node who replies the RREQ packet sent from source node, and makes a false response that it has the quickest route to the destination node. Therefore node 1 erroneously judges the route discovery process with completion, and starts to send data packets to node 3. As what mentioned above, a malicious node probably drops or consumes the packets. This suspicious node can be regarded as a black hole problem in MANETs. As a result, node 3 is able to misroute the packets easily, and the network operation is suffered from this problem. The most critical influence is that the PDR diminished severely.
F
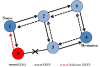 igure
1. The
single black hole problem. Figure
1 is an example of single black hole attack in the mobile ad hoc
networks [25].
Node 1 stands for the source node and node 4 represents the
destination node. Node 3 is a misbehavior node who replies the RREQ
packet sent from source node, and makes a false response that it has
the quickest route to the destination node. Therefore node 1
erroneously judges the route discovery process with completion, and
starts to send data packets to node 3. In the mobile ad hoc networks,
a malicious node probably drops or consumes the packets. This
suspicious node can be regarded as a black hole problem in MANETs. As
a result, node 3 is able to misroute the packets easily, and the
network operation is suffered from this problem.
igure
1. The
single black hole problem. Figure
1 is an example of single black hole attack in the mobile ad hoc
networks [25].
Node 1 stands for the source node and node 4 represents the
destination node. Node 3 is a misbehavior node who replies the RREQ
packet sent from source node, and makes a false response that it has
the quickest route to the destination node. Therefore node 1
erroneously judges the route discovery process with completion, and
starts to send data packets to node 3. In the mobile ad hoc networks,
a malicious node probably drops or consumes the packets. This
suspicious node can be regarded as a black hole problem in MANETs. As
a result, node 3 is able to misroute the packets easily, and the
network operation is suffered from this problem.
In the following, different detection schemes for single black hole attack are presented in a chronological order. The comparisons of different schemes are shown in Table 1.
Table 1. Comparison of Single Black Hole Attack Detection Schemes
3.1. Neighborhood-based and Routing Recovery Scheme [26]
Bo Sun et al. use AODV as their routing example, and claim that the on-demand routing protocols such as DSR are also suitably applied after a slightly modified. The detection scheme uses on a neighborhood-based method to recognize the black hole attack, and a routing recovery protocol to build the correct path. The neighborhood-based method is employed to identify the unconfirmed nodes, and the source node sends a Modify_Route_Entry control packet to destination node to renew routing path in the recovery protocol.
In this scheme, not only a lower detection time and higher throughput are acquired, but the accurate detection probability is also achieved. To deserve to be mentioned, the routing control overhead does not increase in Bo Sun et al.'s proposal. However, this scheme is useless when the attackers cooperate to forge the fake reply packets.
