
- •Introduction
- •Applications of Real-Time Systems
- •Voltage
- •Figure 7: Conversion of an Analog Signal to a 16 bit Binary Number
- •Figure 11: Schematic Representation of tmr
- •It is relatively simple to design a hardware equipment to be fault-tolerant. The following are two methods that are popularly used to achieve hardware fault-tolerance:
- •Software Fault-Tolerance Techniques
- •Types of Real-Time Tasks
- •Timing Constraints
- •Events in a Real-Time System
- •Figure 16: Delay Constraint Between Two Events el and e2
- •Examples of Different Types of Timing Constraints
- •Figure 19: Classification of Timing Constraints
- •Real-Time Task Scheduling
- •Figure 1: Relative and Absolute Deadlines of a Task
- •Figure 2: Precedence Relation Among Tasks
- •Types of Real-Time Tasks and Their Characteristics
- •Classification of Real-Time Task Scheduling Algorithms
- •Figure 5: An Example Schedule Table for a Cyclic Scheduler
- •Figure 6: Major and Minor Cycles in a Cyclic Scheduler
- •Comparison of Cyclic with Table-Driven Scheduling
- •Hybrid Schedulers
- •Event-driven Scheduling
- •Is edf Really a Dynamic Priority Scheduling Algorithm?
- •Implementation of edf
- •Figure 10: Priority Assignment to Tasks in rma
- •We now illustrate the applicability of the rma schodulability criteria through a few examples.
- •Deadline Monotonic Algorithm (dma)
- •Handling Aperiodic and Sporadic Tasks
- •Dealing With Task Jitter
- •W Good real-time task scheduling algorithms ensure fairness to real-time tasks while scheduling.
- •State whether the following assertions are True or False. Write one or two sentences to justify your choice in each case.
- •Figure 2: Unbounded Priority Inversion
- •Highest Locker Protocol(hlp)
- •Priority Ceiling Protocol (pcp)
- •Comparison of Resource Sharing Protocols
- •Handling Task Dependencies
- •Fault-Tolerant Scheduling of Tasks
- •Clocks in Distributed Real-Time Systems
- •Clock Synchronization
- •Figure 1: Centralized synchronization system
- •Cn Slave clocks
- •Commercial Real-Time Operating Systems
- •Time Services
- •Clock Interrupt Processing
- •Providing High Clock Resolution
- •Figure 2: Use of a Watchdog Tinier
- •Unix as a Real-Time Operating System
- •In Unix, dynamic priority computations cause I/o intensive tasks to migrate to higher and higher priority levels, whereas cpu-intensive tasks are made to seek lower priority levels.
- •Host-Target Approach
- •Preemption Point Approach
- •Self-Host Systems
- •Windows As a Real-Time Operating System
- •Figure 9: Task Priorities in Windows nt
- •Open Software
- •Genesis of posix
- •Overview of posix
- •Real-Time posix Standard
- •Rt Linux
- •7.8 Windows ce
- •Benchmarking Real-Time Systems
- •Figure 13: Task Switching Time Among Equal Priority Tasks
- •Real-Time Communication
- •Figure 2: a Bus Architecture
- •Figure 4: Logical Ring in a Token Bus
- •Soft Real-Time Communication in a lan
- •Figure 6: Priority Arbitration Example
- •Figure 8: Problem in Virtual Time Protocol
- •Figure 9: Structure of a Token in ieee 802.5
- •Figure 10: Frames in the Window-based Protocol
- •Performance Comparison
- •A Basic Service Model
- •Traffic Characterization
- •Figure 16: Constant Bit-Rato Traffic
- •Routing Algorithms
- •Resource Reservation
- •Resource Reservation Protocol (rsvp)
- •Traffic Shaping and Policing
- •Traffic Distortion
- •Traffic Scheduling Disciplines
- •Figure 20: Packet Service in Jittor-edd
- •Differentiated Services
- •Functional Elements of DiffServ Architecture
- •Real Time Databases
- •Isolation: Transactions are executed concurrently as long as they do not interfere in each other’s computations.
- •Real-Time Databases
- •Real-Time Database Application Design Issues
- •Temporal Consistency
- •Concurrency Control in Real-Time Databases
- •It can bo shown that pcp is doadlock froo and single blocking. Rocolloct that single blocking moans that once a transaction starts executing after being blocked, it may not block again.
- •Speculative Concurrency Control
- •Comparison of Concurrency Control Protocols
- •Commercial Real-Time Databases
- •Figure 16: Uniform Priority Assignment to Tasks of Example 15
- •Version 2 cse, iit Kharagpur
Figure 2: Unbounded Priority Inversion
plest way to avoid priority inversions is to prevent preemption (from CPU usage) of the low priority task holding a critical resource by intermediate priority tasks. This can be achieved by raising the priority level of the low priority task to be equal to that of the waiting high priority task. In other words, the low priority task is made to inherit the priority of the waiting high priority task. This basic mechanism of a low priority task inheriting the priority of a high priority task forms the central idea behind the priority Inheritance Protocol (PIP)- This simple protocol serves as the basic real-time resource sharing mechanism, based on which more sophisticated protocols have been designed.
In the following sections we first discuss the basic priority inheritance protocol (PIP) in some detail. Subsequently, we discuss highest locker protocol (HLP) and priority ceiling protocol (PCP) that have been developed by extending the simple priority inheritance idea further.
Priority Inheritance Protocol (PIP)
The basic priority inheritance protocol (PIP) is a simple technique to share critical resources among tasks without incurring unbounded priority inversions. As it turns out, real-time operating system designers do not find it very difficult to support the basic priority inheritance mechanism. In fact, as we discuss in the Chapter 5, most of the real-time operating systems that are commercially available at present do support this protocol.
The basic PIP was proposed by Sha and Rajkumar [1]. The essence of this protocol is that whenever a task suffers priority inversion, the priority of the lower priority task holding the resource is raised through a priority inheritance mechanism. This enables it to complete its usage of the critical resource as early as possible without having to suffer preemptions from the intermediate priority tasks. When many tasks are waiting for a resource, the task holding the resource inherits the highest priority of all tasks waiting for the resource (if this priority is greater than its own priority). Since the priority of the low priority task holding the resource is raised to equal the highest priority of all tasks waiting for the resource being held by it, intermediate priority tasks can not preempt it and unbounded priority inversion is avoided. As soon as a task that had inherited the priority of a waiting higher priority task (because of holding a resource), releases the resource it gets back its original priority value if it is holding no other critical resources. In case it is holding other critical resources, it would inherit the priority of the highest priority task waiting for the resources being held by it.
Figure
3: Snapshots Showing Working of Priority Inheritance Protocol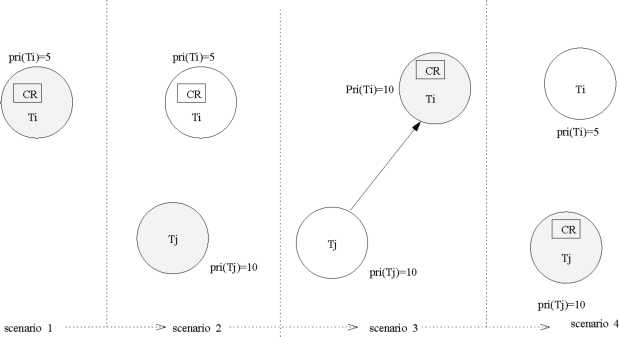
if |
the |
required grant it. |
resource |
is |
free then |
if |
the |
required |
resource |
is |
being held by a |
|
|
wait for |
the resource |
||
if |
the |
required |
resource |
is |
held by a lower |
wait for the resource the low priority task holding the resource acquires the highest priority of tasks waiting for the resource.
The priority changes that a task holding a resource undergoes has been illustrated through an example as shown in the Figs. 3 and 4. In Fig. 3 four consecutive scenarios in the execution a system deploying PIP are shown. In each scenario, the executing task is shown shaded, and the blocked task are shown unshaded. The priority changes that two tasks Ti and Tj undergo in the course of execution due to priority inheritance is shown. Ti is a low priority task with priority 5 and Tj is a higher priority task with priority 10. In scenario 1, I* is executing and has acquired a critical resource CR. In scenario 2, Tj has became ready and being of higher priority is executing. In scenario 3, Tj is blocking after requesting for the resource R and Ti inherits Tj’s priority. In scenario 4, Ti has unlocked the resource and has got back its original priority and Tj is executing with the resource.
In Fig. 4 the priority changes of tasks are captured on a time line. The task Tj initially locks the resource CR. After some time it is preempted by T2. The task T2 request the resource CR at t2. Since, Tj already holds the resource, T2 blocks and T3 inherits the priority of T2. This has been shown by drawing T2 and T3 at the same priority levels. Before T3 could complete use of resource CR, it is preempted by a higher priority task T\. T\ requests for CR1 at time t3 and T\ blocks as CR1 is still being held by T3. So, at this point there are two tasks (T2 and T\) waiting for the resource. T3 inherits the priority of the highest priority waiting task (that is, T\). T3 completes its usage of the resource at t4 and as soon as it releases the resource, it gets back its original priority. It should be noted that a lower priority task retains the inherited priority, until it holds the resource required by the waiting higher priority task. Whenever more than one higher priority task are waiting for the same resource, the task holding the resource inherits the maximum of the priorities of all waiting high priority tasks.
It is clear that PIP can let real-time tasks share critical resources without letting them incur unbounded priority
Figure
4: Priority Changes Under Priority Inheritance Protocol inversions.
However, it suffers from two important problems:
tl t2 t3 t4
time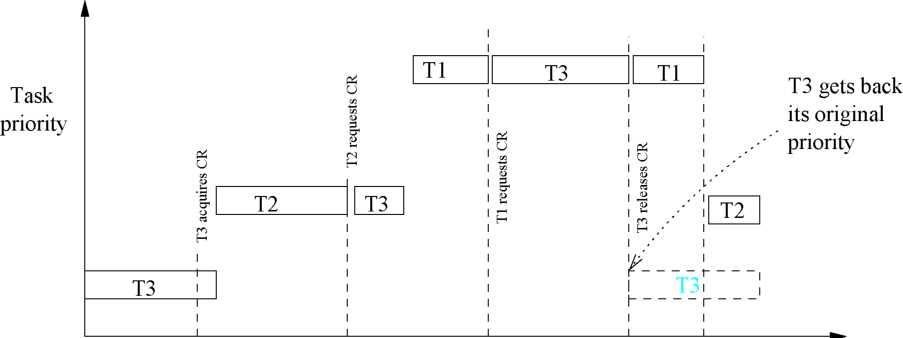
We elaborate these two issues in the following.
Deadlock: The basic priority inheritance protocol (PIP) leaves open the possibility of deadlocks. In the following we illustrate how deadlocks can occur in PIP using an example. Consider the following sequence of actions by two tasks Ti and T2 which need access to two shared critical resources CR1 and CR2.
Ti: Lock CR1, Lock CR2, Unlock CR2, Unlock CR1
T-2: Lock CR2, Lock CR1, Unlock CR1, Unlock CR2
Assume that T\ has higher priority than T2. T2 starts running first and locks critical resource CR2 (Ti was not ready at that time). After some time, T\ arrives, preempts T2, and starts executing. After some time, T\ locks CR1 and then tries to lock CR2 which is being held by T2. As a consequence T\ blocks and T2 inherits Ti’s priority according to the priority inheritance protocol. T2 resumes its execution and after some time needs to lock the resource CR1 being held by T\. Now, T\ and T2 are both deadlocked.
Chain Blocking: A task is said to undergo chain blocking, if each time it needs a resource, it undergoes priority inversion. Thus if a task needs n resources for its computations, it might have to undergo priority inversions n times to acquire all its resources. Let us now explain how chain blocking can occur using the example shown in Fig. 5. Assume that a task T\ needs several resources. In the first snapshot (shown in Fig. 5), a low priority task T2 is holding two resources CR1 and CR2, and a high priority task T\ arrives and requests to lock CR1. It undergoes priority inversion and causes T2 to inherit its priority. In the second snapshot, as soon as T2 releases CR1 its priority reduces to its original priority and T\ is able to lock CR1. In the third snapshot, after executing for some time, T\ requests to lock CR2. This time it again undergoes priority inversion since T2 is holding CR2. T\ waits until T2 releases CR2. From this example, we can see that chain blocking occurs when a task undergoes multiple priority inversions to lock its required resources.
T2
Executing T1 Executing T2
Executing
T1
Blocked
T1
Blocked T2 Blocked
Snapshot
1 Snapshot 2 Snapshot
3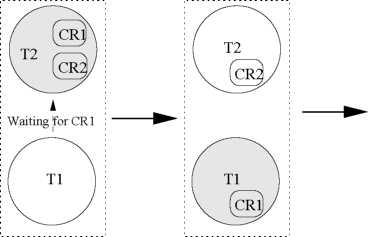
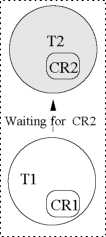 Figure
5: Chain Blocking in Priority Inheritance Protocol
Figure
5: Chain Blocking in Priority Inheritance Protocol
