
- •Table of Contents
- •BackCover
- •Cryptography-A Very Short Introduction
- •Chapter 1: Introduction
- •Using this book
- •Chapter 2: Understanding Cryptography
- •The basic concepts
- •Chapter 3: Historical Algorithms: Simple Examples
- •Caesar Cipher
- •Simple Substitution Ciphers
- •The statistics of the English language
- •The Playfair Cipher
- •Homophonic Coding
- •Polyalphabetic Ciphers
- •Vigenère Ciphers
- •Transposition Ciphers
- •Super-encryption
- •Some conclusions
- •Appendix
- •Chapter 4: Unbreakable Ciphers?
- •Perfect secrecy
- •The one-time pad
- •Chapter 5: Modern Algorithms
- •Bit-strings
- •Stream ciphers
- •Block ciphers (ECB mode)
- •Hash functions
- •Public key systems
- •Chapter 6: Practical Security
- •Realistic security
- •Practical exhaustive key searches
- •Attacks on public key systems
- •Chapter 7: Uses of Cryptography
- •Using symmetric algorithms for confidentiality
- •Authentication
- •Using symmetric algorithms for authentication and data integrity
- •Digital signatures
- •Certification authorities
- •Public Key Infrastructure
- •The need for trust
- •Chapter 8: Key Management
- •The key life cycle
- •Key hierarchies
- •Managing keys in networks
- •Using a trusted management centre
- •Key recovery and key back-up
- •Chapter 9: Cryptography in Everyday Life
- •A cash withdrawal from an ATM
- •Pretty Good Privacy (PGP)
- •Secure web browsing
- •Using a GSM mobile phone
- •References and further reading

Polyalphabetic Ciphers
Team-Fly
Polyalphabetic Ciphers
When a homophonic cipher is used, the frequency histogram of the cryptogram is made flatter by increasing the size of the alphabet. This ensures that more than one ciphertext character may represent the same plaintext character. However, it is still true that each ciphertext character represents a unique plaintext character and there is always the danger of an attacker compiling a dictionary of known plaintext and ciphertext pairs for a given key.
Another way of achieving the objective of flattening the frequency histogram is by the use of a polyalphabetic cipher. When a polyalphabetic cipher is used, the ciphertext character replacing a particular plaintext letter may vary through the cryptogram and might, for instance, depend on its position in the plaintext message or the content of the plaintext that precedes it. For these ciphers it is now true that the same ciphertext character may represent different plaintext letters. This is not true for homophonic coding.
Once again we must point out that the simple examples of these ciphers that we describe are no longer used. However we discuss them in some detail as we can then illustrate a number of weaknesses that the modern algorithm designer has to avoid. As with our earlier examples, we include them to illustrate a number of cryptanalytic techniques and because they enable us to set exercises which are both informative and fun.
Team-Fly
file:///D|/1/4303/Fly0012.html [08.10.2007 12:51:07]
Vigenère Ciphers
Team-Fly
Vigenère Ciphers
The Vigenère Cipher is probably the best known of the 'manual' polyalphabetic ciphers and is named after Blaise de Vigenère, a 16thcentury French diplomat. Although it was published in 1586, it was not widely recognized until nearly 200 years later and was finally broken by Babbage and Kasiski in the middle of the 19th century. It is interesting to note that the Vigenère Cipher was used by the Confederate Army in the American Civil War. The Civil War occurred after the cipher had been broken. This is illustrated by the quotation by General Ulysses S. Grant: 'It would sometimes take too long to make translations of intercepted dispatches for us to receive any benefit from them, but sometimes they gave useful information.'
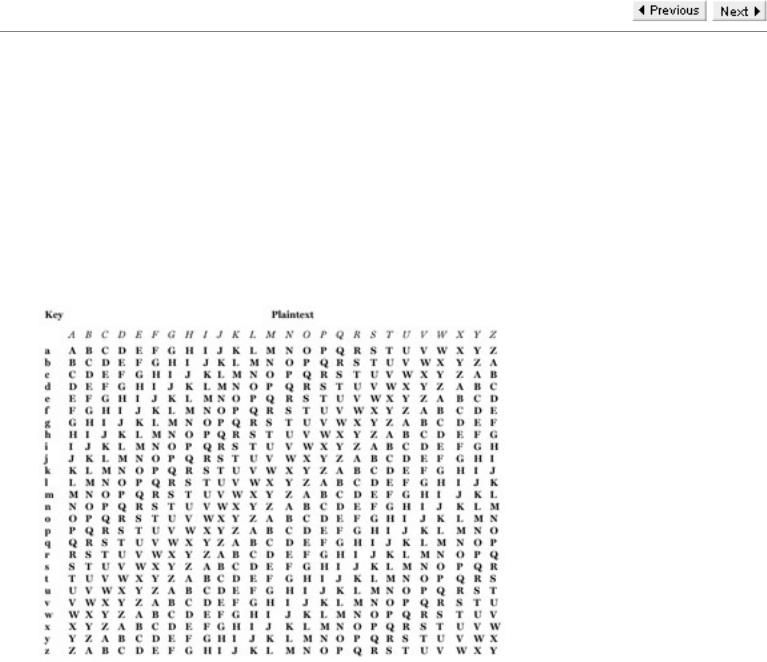
The Vigenère Cipher uses a Vigenère Square to perform encryption. The left-hand (key) column of this square contains the English alphabet and, for each letter, the row determined by that letter contains a rotation of the alphabet with that letter as the leading character. So each letter in the left-hand column gives a Caesar Cipher whose shift is determined by that letter. Thus, for example, the letter g gives the Caesar Cipher with shift 6.
The Vigenère Square
One of the most common methods for using the square to obtain a cipher involves choosing a keyword (or key phrase) with no repeated letters. If the plaintext message is longer than the keyword, then, by repeating the key as often as is necessary, we obtain a sequence of letters which is as long as the message. We then write this sequence of letters beneath our message. Thus, for example, if our message is PLAINTEXT and our keyword is 'fred' we obtain:
Message |
P L A I N T E X |
|
T |
Key |
f r e d f r e d f |
We now use the square to encrypt the message as follows.
To encrypt the initial letter P we use the key letter beneath it which, in this case, is f. Thus to encrypt P we go to the row of the square determined by f and read off the letter beneath P, which is U. Similarly we encrypt L by taking the letter underneath it in the row determined by r, which is C. The process for encrypting P with key letter f is illustrated here.
file:///D|/1/4303/Fly0013.html (1 von 4) [08.10.2007 12:51:08]

Vigenère Ciphers
Using the Vigenère Square to encrypt P with the key letter f
Any reader who completes this process should conclude that the complete cryptogram for PLAINTEXT with keyword fred is
UCELSLIAY.
This means we now have:
message: P L A I N T E X
T
key: f r e d f r e d f
ciphertext: U C E L S L I A
Y
We can now observe that the plaintext letter T is represented by both L and Y in the ciphertext and that the ciphertext letter L represents both I and T. Thus it is clear that, by using these ciphers, we can prevent the frequency of letters in the cryptogram having the same distinctive patterns as those exhibited by cryptograms resulting from Simple Substitution Ciphers.
There are many variations of the Vigenère Cipher, including one in which the keyword is allowed to have repeated letters. Each of them has slightly different characteristics that lead to slightly varying attacks. However we restrict our attention to the precise system that we have defined.
Vigenère Ciphers are a particular example of a polyalphabetic cipher in which a (short) sequence of Simple Substitution Ciphers is repeatedly used in strict rotation. The number of component ciphers used is called the period and, clearly, for the version of the Vigenère Cipher that we have described, the period is equal to the length of the keyword.
Before continuing our discussion of periodic ciphers it is worth noting that, for instance, a polyalphabetic cipher of period 3 is nothing more than a particular example of a Simple Substitution Cipher on trigrams. This simple observation is merely a special instance of the general
file:///D|/1/4303/Fly0013.html (2 von 4) [08.10.2007 12:51:08]
Vigenère Ciphers
principle that changing the alphabet can change the 'nature' of a cipher. For the present we are concentrating on ciphers where the basic symbols are the letters of the English alphabet. When discussing more modern ciphers, we tend to regard all messages as sequences of binary digits (0s and 1s).
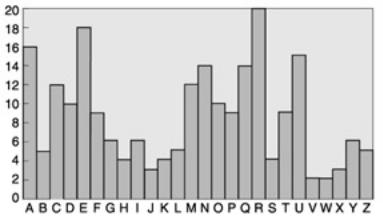
As we have already noted, one motivation for using polyalphabetic ciphers is to disguise the letter frequency of the underlying language. As an illustration of how this is achieved we include a histogram to show the frequency count for a specific cryptogram that was the result of using a Vigenère Cipher of period 3 on a passage of English text.
There are a number of obvious differences between this histogram and the one shown earlier. The most striking ones are that every letter occurs in the second histogram and that no letter dominates this histogram in quite the same way that H dominates the first one. This second histogram is undoubtedly flatter than the earlier one and, consequently, is not of such immediate assistance to a would-be attacker. Anyone looking at the second histogram would be tempted to deduce that the cryptogram letter R represents the plaintext E somewhere. However they would not know at which positions this occurred.
A frequency histogram for a cryptogram when three Simple Substitution Ciphers were used in strict rotation
In general we would expect the flatness of the histogram to reflect the length of the period and that longer periods make the ciphers harder to break. In some sense this is true. However all that using a periodic polyalphabetic cipher achieves in practice is to ensure that the cryptanalyst needs considerably more ciphertext to start an attack. In order to illustrate this, we concentrate on Vigenère Ciphers. Some of our assertions are true for any polyalphabetic cipher, whilst others rely on the characteristics of our definition of a Vigenère Cipher. It is important that the reader distinguishes between the two situations. Thus changing the polyalphabetic cipher may change the details of the attack and 'strengthen' the system slightly. However, polyalphabetic ciphers where the key is significantly shorter than the message are all vulnerable to some variation of the attacks exhibited here.
In order to break a Vigenère Cipher it is sufficient to determine the keyword. If the period is known and is not too long then this can be determined by writing a computer program to conduct an exhaustive key search. As an illustration readers might like to perform a key search on the cryptogram TGCSZ GEUAA EEWGQ AHQMC, given that it is the result of using a Vigenère Cipher with a keyword of length 3 on a passage of English text. Any reader who tries this is presented with an interesting problem of recognizing the correct keyword. The basic assumption is, presumably, that it is the only three-letter word which gives plaintext that is meaningful. However the real problem is how can one recognize that the plaintext is meaningful. One possibility is to sit at the screen and inspect the result of applying each key. Clearly this is both boring and time consuming. Alternatives must be found.
When conducting an exhaustive search for a keyword of length p, it is probably easier to try all sequences of p letters systematically than to
consider only English words. Thus for a Vigenère Cipher of known period p, an exhaustive key search probably requires 26p trials. This means that, as the period increases, exhaustive key searches can quickly become unmanageable. However, if the period is known then it is comparatively straightforward to determine the keyword without conducting a search. One way is to write the ciphertext in p rows in such a way that the cryptogram is reconstructed by writing each column in order. So, for instance, for p = 3, if the ciphertext is c1c2c3c4c5c6c7c8c9 ...
then we write it as
c1c4c7c10 . . .
c2c5c8cU . . .
c3c6c9c12 . . .
file:///D|/1/4303/Fly0013.html (3 von 4) [08.10.2007 12:51:08]

Vigenère Ciphers
Once this is done then each row is the result of using the same Simple Substitution Cipher that, for the particular case of a Vigenère Cipher, is an additive cipher. We can now use the statistical arguments of the last section on each individual row. In fact, for a Vigenère Cipher where the length of the cryptogram is long in comparison to the period p, it is probably sufficient to determine the most frequent letter in each row and assume that it represents either E, T, or A. This latter observation exploits the fact that, for each row, the Simple Substitution Cipher being used is a Caesar Cipher. This means, as we have already noted, that knowledge of a single plaintext and ciphertext pair is sufficient to determine the key. Consequently if the ciphertext equivalent of one single letter for each row can be determined, probably by a suitable mixture of intelligent guessing and luck, then the key can be determined.
The discussion so far suggests that the real problem facing the attacker of a Vigenère Cipher is the determination of the period p. One possibility is to systematically try all small values of p. However, there are also a number of simple, ingenious ways of achieving it. The most famous is known as the Kasiski test and is the one used by Babbage, who was the first person to break the cipher. His method was to search for repeated (long) strings of characters in the ciphertext. When they occur they are quite likely to represent identical passages of the message encrypted using identical keyboard letters. This implies that the gaps between these repeated patterns are likely to be multiples of the period. (The cryptanalysis of the Vigenère Cipher is discussed in detail in Singh's The Code Book.)
Team-Fly
file:///D|/1/4303/Fly0013.html (4 von 4) [08.10.2007 12:51:08]
